US Tax Service Portal Allegedly Compromised: Root SSH Access to Client Database Offered for Sale
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more – independently from the above standard subscriptions.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
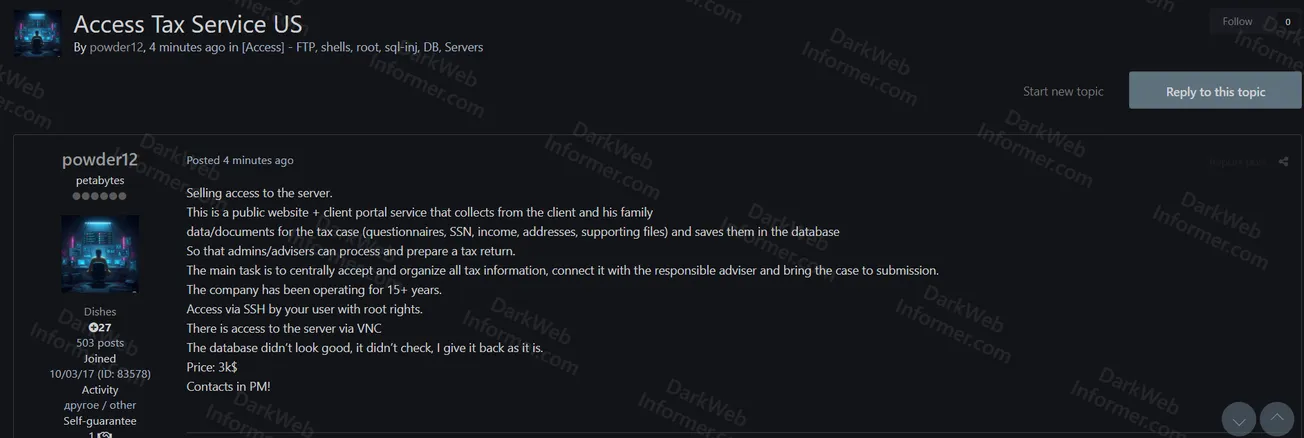
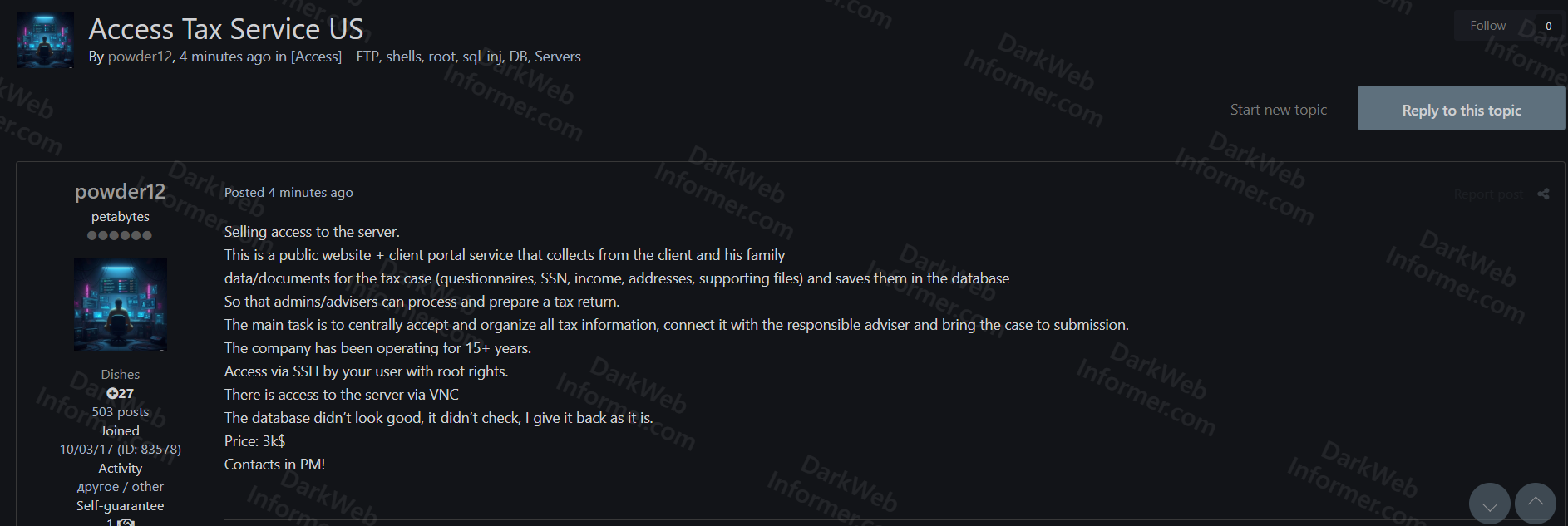
A threat actor using the handle "powder12" is offering unauthorized root SSH access to a US-based tax service server. The compromised system is described as a public website and client portal service that collects and stores sensitive client and family tax data for case processing. The company has been operating for over 15 years.
- Service Type: Public website and client portal for tax case management
- Company Operations: 15+ years in business
- Primary Function: Collect client and family data/documents for tax cases, organize information, connect with responsible advisers, and prepare tax returns for submission
- Data Collection: Questionnaires, Social Security Numbers (SSN), income records, addresses, supporting files
- Database Access: All collected tax information stored in database accessible to admins/advisers for processing and preparing tax returns
- Access Type: SSH access with root privileges via provided user account
- Secondary Access: Server accessible via VNC (Virtual Network Computing)
- Database Status: Database not thoroughly examined by seller ("didn't look good, didn't check, I give it back as it is")
- Pricing: 3k$ (approximately $3,000 USD)
Indicators of Compromise (IOCs)
No IOCs were disclosed by the threat actor in this claim.
Initial Access Sale URL
Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Dark Web Informer © 2026 | Cyber Threat Intelligence