Link: https://pipl.com
In the world of cybersecurity, the need for accurate, real-time intelligence on individuals has never been more pressing. Whether tracking down a threat actor or vetting suspicious online profiles, having a tool that provides actionable data is crucial. That's where Pipl.com comes in—a search engine with the power to connect the dots across the digital landscape, making it a valuable asset for cybersecurity professionals.
What Is Pipl.com?
At its core, Pipl.com is a people search engine, but not just any typical one. It scours the deep web, collecting information from social networks, databases, and public records to uncover the digital footprints that most search engines miss. It’s not just about pulling names or addresses; Pipl goes deeper by linking online personas through email addresses, usernames, social media profiles, and more.
This is where it becomes highly relevant for cybersecurity. When investigating a phishing attack, tracking down the source of a data breach, or even uncovering connections between fraudulent accounts, Pipl’s extensive data access can help identify the threat actor’s full online presence.
Why Cybersecurity Experts Should Care
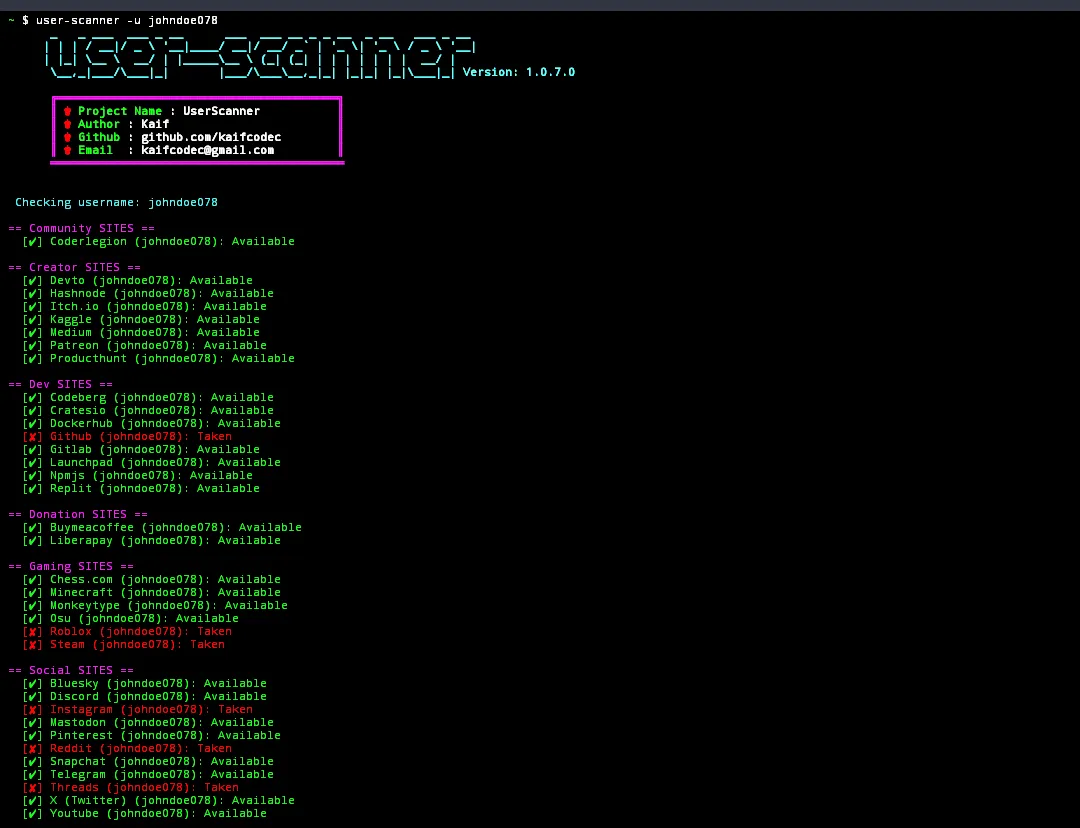
Cybersecurity pros often face a challenge when trying to link online behavior to real-world identities. Malicious actors hide behind false profiles, disposable emails, or anonymized handles. Pipl’s technology excels at mapping these digital breadcrumbs back to actual identities, aiding in everything from threat intelligence to incident response. Here are a few ways Pipl.com can be a game-changer:
- Threat Actor Identification
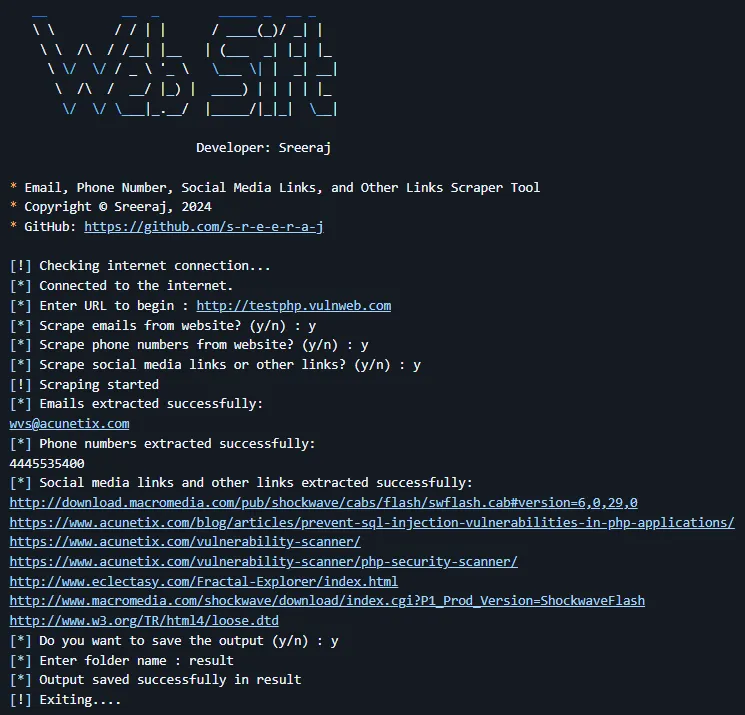
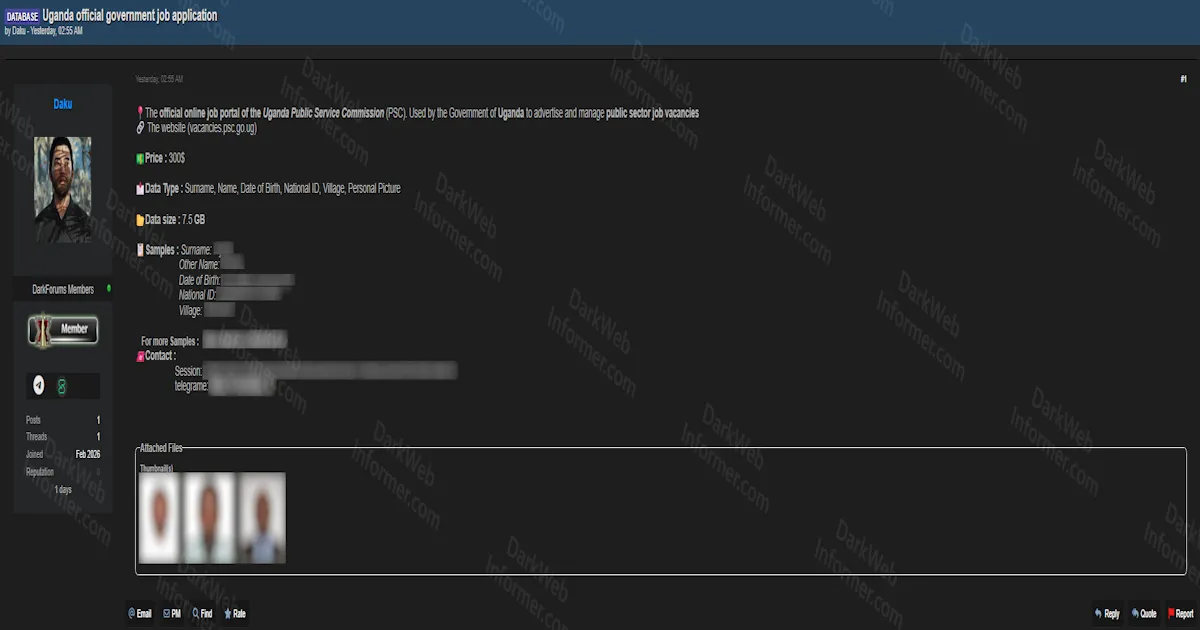
Pipl’s ability to aggregate data from across the internet makes it invaluable for identifying threat actors. By running a simple query using an email address or username, you can pull a web of associated social media accounts, websites, and other personal details that help build a profile on the attacker. - Fraud Detection
Pipl is often used in fraud investigations to verify identities. Cybercriminals often create fake profiles, which makes tracking them challenging. Pipl can compare the details provided with its extensive datasets, potentially exposing fraudulent behaviors. - Dark Web Insights
The deep web search capability of Pipl provides a unique opportunity to access information beyond the surface web. It’s useful in dark web monitoring, where the breadcrumbs left behind in obscure forums or lesser-known networks can be linked back to more well-known platforms.
Use Cases in Cybersecurity
Let’s say you’re working on a breach investigation where the attacker used a fake email address to compromise user accounts. Traditional investigative methods might hit a wall, but with Pipl, you could input that email address and discover associated social media profiles, usernames, and even potential real-world identifiers.
In another instance, suppose you’re analyzing a phishing campaign. You have the attacker’s email and a couple of shady usernames. Plugging these into Pipl could reveal connected platforms, giving you insight into the threat actor’s broader online activities, helping you anticipate future attacks.
Privacy and Ethical Considerations
One thing to keep in mind: Pipl’s vast reach raises some ethical questions around privacy. It’s important for cybersecurity experts to handle the data responsibly and ensure compliance with local and international privacy laws like GDPR. While Pipl provides powerful insights, it’s essential to balance these capabilities with ethical considerations, especially when handling sensitive personal information.
How to Get the Most Out of Pipl
To make the most of Pipl.com, focus on the following tactics:
- Be specific with search queries. Inputting a combination of known identifiers (email, username, name) will yield better results than just one data point.
- Leverage Pipl's API. For larger-scale investigations, Pipl offers an API that allows for bulk searches, ideal for organizations handling multiple cases at once.
- Cross-reference your findings. Use Pipl in conjunction with other open-source intelligence (OSINT) tools to validate findings and build stronger threat profiles.
Conclusion
For cybersecurity professionals, Pipl.com offers a powerful way to track and identify malicious actors across the vast expanses of the internet. From its deep web insights to its ability to tie together seemingly unrelated data points, Pipl is a tool worth having in your arsenal for everything from fraud detection to threat actor identification.
As with all tools, its effectiveness comes down to how well you use it. When wielded responsibly, Pipl can make your cyber investigations faster, more precise, and much more effective.
Link: https://pipl.com