ProjectDiscovery, the team behind widely-used tools like Subfinder and Nuclei, has released TLDFinder - an open-source utility designed to enumerate private top-level domains (TLDs) and discover associated domains that traditional subdomain enumeration tools completely miss.
What Problem Does TLDFinder Solve?
Most offensive security professionals and bug bounty hunters are familiar with subdomain enumeration. Tools like Subfinder, Amass, and others have made discovering subdomains under .com, .net, and .org a routine part of any reconnaissance workflow. But there's an entire layer of attack surface that's been largely overlooked: private TLDs.
Many large organizations own their own top-level domains. Google owns .google, .goog, and .go. Marriott owns .marriott. Netflix owns .netflix. American Express owns both .americanexpress and .amex. These aren't subdomains - they're entirely separate domain hierarchies that exist outside the scope of traditional enumeration.
Until now, there hasn't been a practical, passive way to discover what domains exist under these private TLDs. Researchers either had to request zone files directly from TLD owners (which would tip off the target during a red team engagement) or attempt brute-force approaches with wordlists. Neither option was ideal.
Origin Story - Born From a Red Team Engagement
TLDFinder originated from real-world need. Idan Ron, a researcher at Mandiant (now part of Google Cloud's threat intelligence group), was conducting a red team assessment against a major retail company when he discovered through SSL certificate analysis that the target owned its own TLD. He went looking for tools to enumerate domains under that TLD and found nothing suitable.
The core insight was straightforward: many of the passive data sources used for subdomain enumeration - certificate transparency logs, DNS datasets, WHOIS databases - also index domains under private TLDs. The data was already there. Nobody had built a tool to query it this way.
Ron collaborated with ProjectDiscovery to build TLDFinder, which applies the same passive enumeration methodology that Subfinder uses for subdomains, but targets private TLDs instead.
How It Works
TLDFinder operates in multiple discovery modes and pulls from a variety of passive data sources. At a high level, the tool:
- Identifies private TLDs by searching IANA's TLD registry and other sources for TLDs matching a target organization name.
- Enumerates domains under those TLDs by querying passive data sources - certificate transparency logs (crt.sh), DNS intelligence APIs (Netlas, HackerTarget), WHOIS databases, and others.
- Optionally resolves discovered domains actively to confirm which ones are live.
The tool accepts either a private TLD directly (e.g., google) or a full domain (e.g., example.google), from which it auto-extracts the TLD portion.
Example usage:
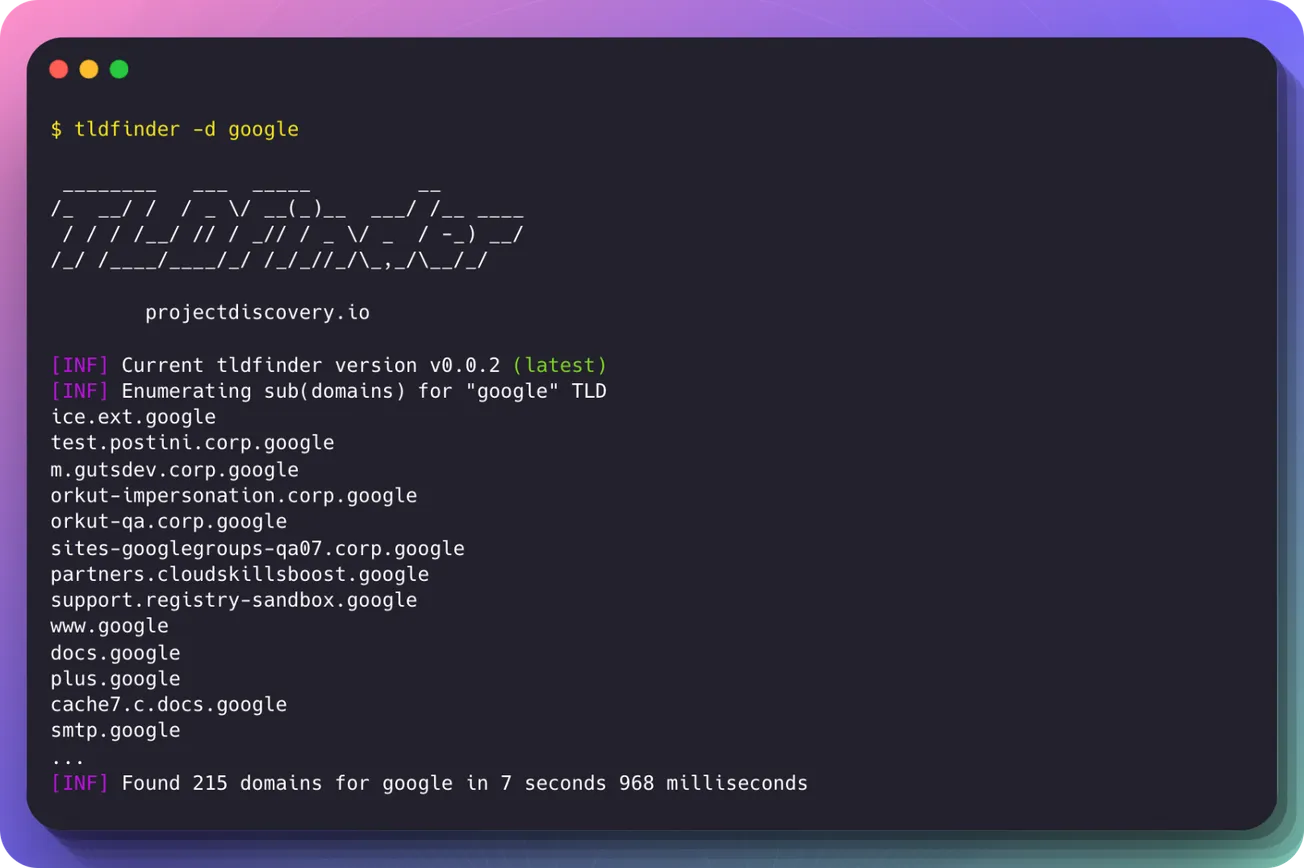
tldfinder -d google
In a demonstration run against Google's private TLD, the tool discovered 215 domains in under 8 seconds - including internal-looking hostnames like test.postini.corp.google, orkut-qa.corp.google, and partners.cloudskillsboost.google.
Why This Matters for Threat Intelligence and Security Research
The implications here are significant across multiple disciplines:
For red teamers and penetration testers, private TLD enumeration dramatically expands the attack surface map. As bug bounty researcher Jason Haddix has noted, every new apex domain discovered roughly quadruples the chances of finding a vulnerability. Domains under private TLDs are often internal or development-oriented, which frequently means weaker security posture.
For threat intelligence analysts, monitoring private TLDs provides visibility into infrastructure that organizations may not realize is publicly discoverable. Internal hostnames, staging environments, and development infrastructure that leak into certificate transparency logs or DNS datasets can reveal organizational structure, technology stack, and potential exposure.
For defenders, the existence of this tool is a reminder that private TLDs are not inherently private. If your organization owns a TLD, the domains registered under it are visible through the same passive sources that expose any other domain. Security teams should be running tools like TLDFinder against their own TLDs to understand what's discoverable.
Key Features
- Passive and active discovery modes - passive DNS lookups by default, with optional active resolution
- Multiple data sources - queries certificate transparency, DNS datasets, WHOIS, and other intelligence APIs
- Rate limiting controls - configurable per-source rate limits to avoid burning API keys
- Flexible output - standard text or JSON output, with source attribution
- Source filtering - include or exclude specific data sources
- Proxy support - route requests through HTTP proxies for operational security
Installation
TLDFinder is written in Go and requires Go 1.21+. Install via:
go install github.com/projectdiscovery/tldfinder/cmd/tldfinder@latest
Pre-compiled binaries are also available on the GitHub releases page. The tool is MIT licensed.
Bottom Line
TLDFinder fills a genuine gap in the reconnaissance toolkit. Subdomain enumeration has been a solved problem for years, but private TLD enumeration was effectively a blind spot. For any organization that owns a private TLD - and there are hundreds of them - this tool surfaces an attack surface that has been largely invisible to both attackers and defenders.
The project is actively maintained by ProjectDiscovery and available at github.com/projectdiscovery/tldfinder.