Dark Web Informer — Cyber Threat Intelligence
Threat Actor Offers WordPress Admin, Shell, and Database Access to Unidentified US E-Commerce Shop
Quick Facts
Date & Time
2026-02-11 21:33:56 UTC
Threat Actor
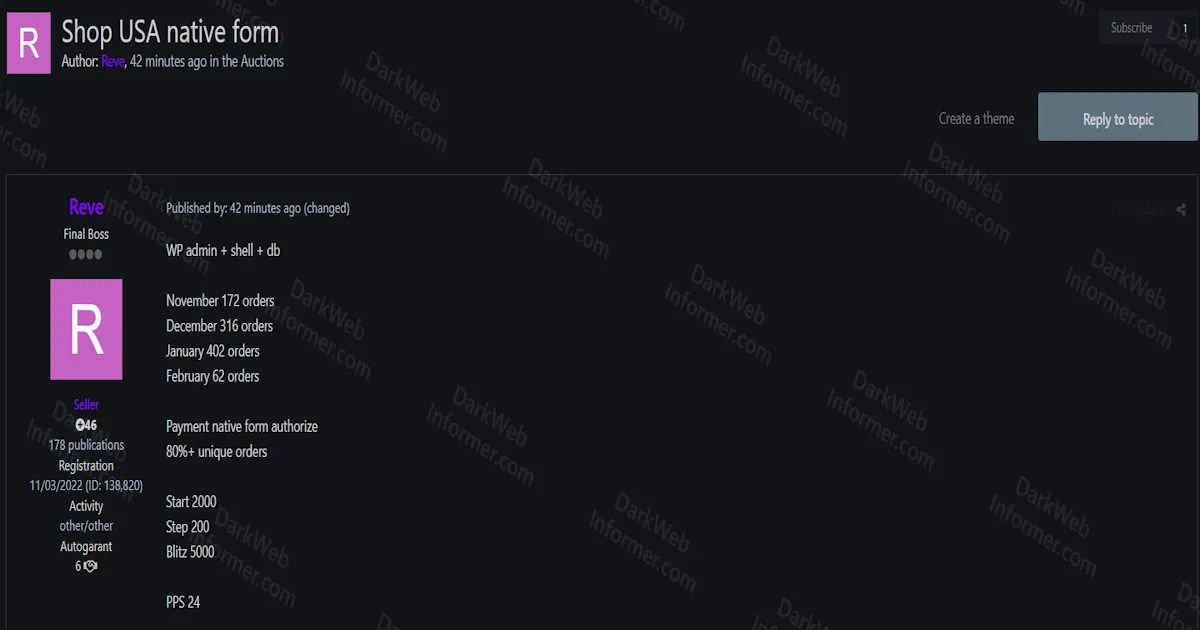
Reve
Victim Country
 United States
United StatesIndustry
E-commerce & Online Stores
Victim Organization
Unidentified
Victim Site
Unknown
Category
Initial Access
Severity
🟡 Medium
Network
Open Web
Victim Profile
Unidentified US E-Commerce Shop
WordPress-based online store with native payment processing Organization
Unidentified
Sector Type
Private
Industry
E-commerce & Online Stores
Country
 United States
United States Platform
WordPress
Payment System
Native Form (Authorize.net)
Description
An unidentified US-based e-commerce store running on WordPress with native payment form authorization. The shop appears to have moderate traffic with 952 total orders logged between November 2025 and February 2026. The threat actor claims 80%+ unique orders, suggesting legitimate customer activity.
Incident Overview
A threat actor using the handle "Reve" has posted an auction listing offering complete unauthorized access to an unidentified US-based e-commerce shop. The listing includes WordPress admin panel access, web shell access, and database access, representing full control over the compromised platform.