Threat Actor Claims to Sell 5 Billion Unique Email:Password Credential Compilation
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
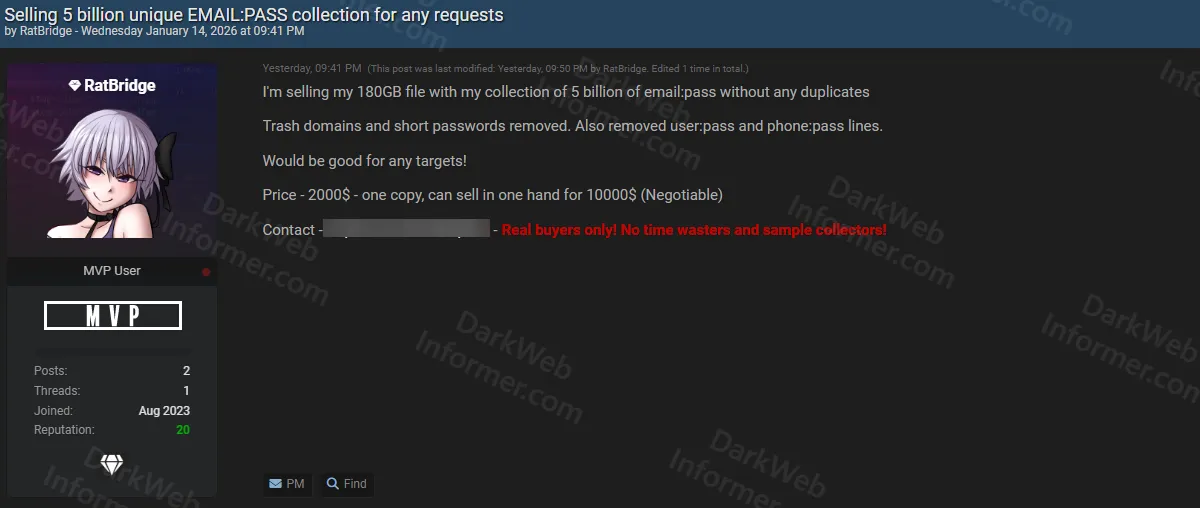
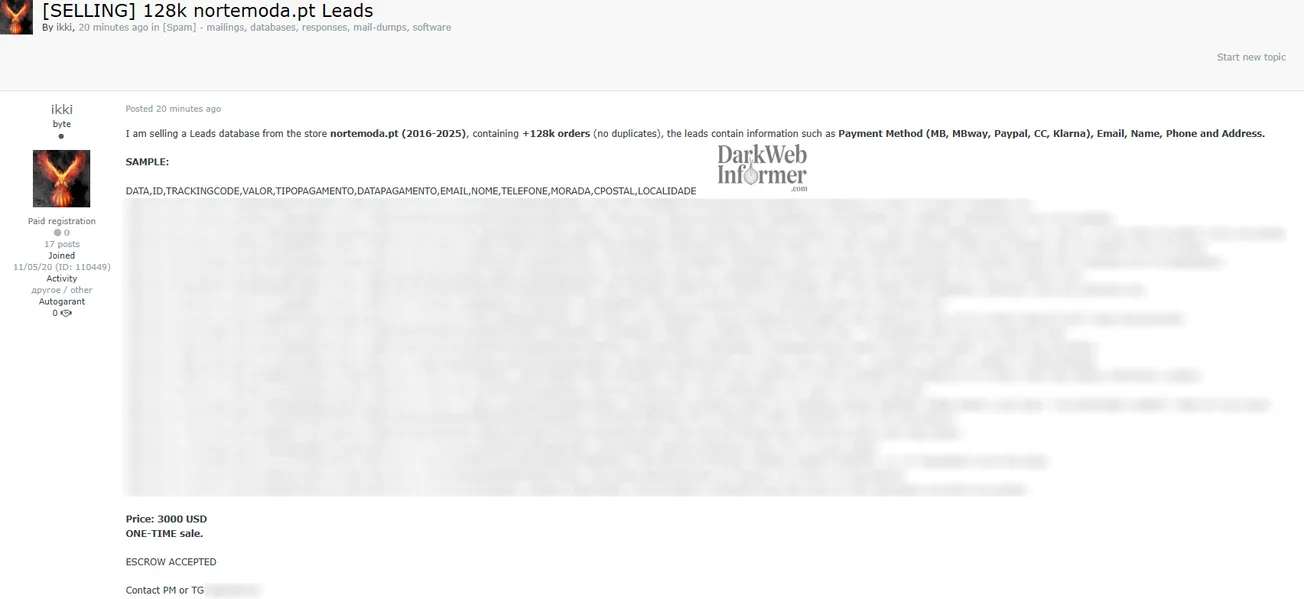
A threat actor operating under the handle "RatBridge" claims to be selling a credential compilation containing 5 billion unique email:password pairs. According to the post, the dataset is distributed as a 180GB file and has been cleaned to remove duplicates. The threat actor states that trash domains, short passwords, user:pass formats, and phone:pass formats have been removed from the collection.
The actor claims the dataset "would be good for any targets," suggesting it is intended for credential stuffing attacks. Pricing is listed at $2,000 for a single copy, with an option to purchase exclusive rights for $10,000 (negotiable). Contact is offered through Telegram, with a note stating "Real buyers only! No time wasters and sample collectors!"
This post is for subscribers on the Plus, Pro and Elite tiers
SubscribeAlready have an account? Sign In