X Thread: https://x.com/DarkWebInformer/status/1848443935191961936
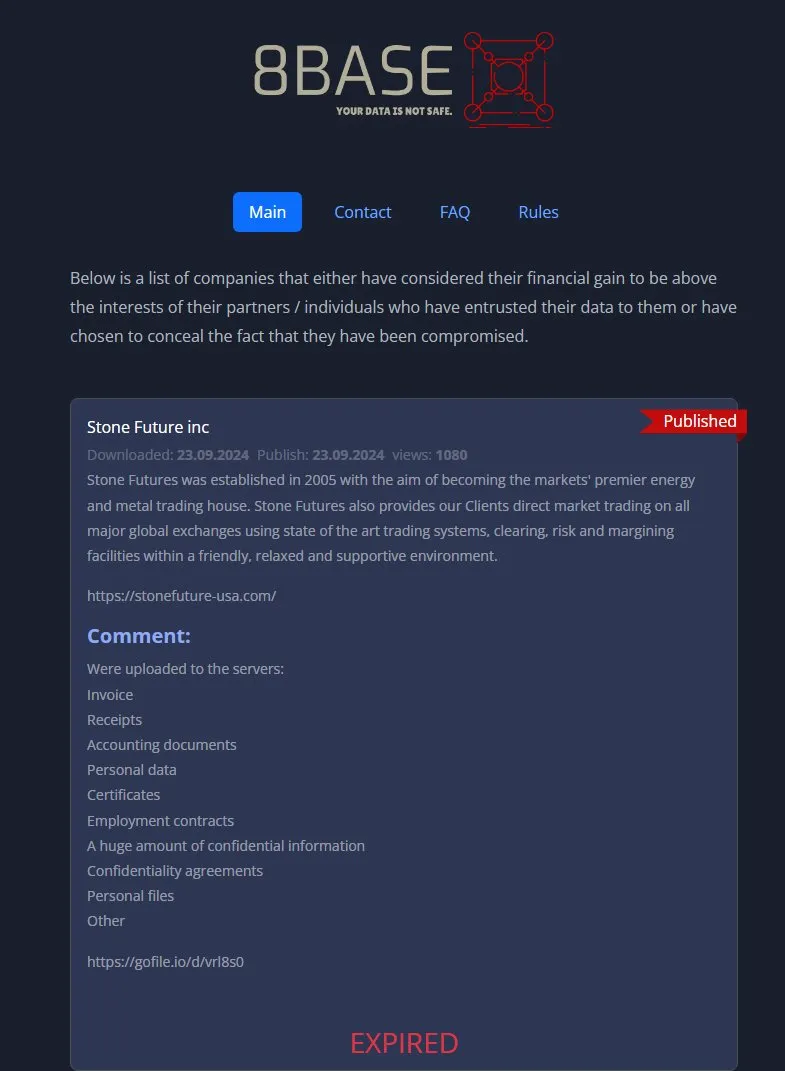
Recently I've seen 'fresh' stealer logs with more than the norm of stolen credentials with large companies in them. I want to provide two examples here; EA and Salesforce.
I sent an email to EA on October 18th and have yet to hear back. In the first screenshot you can see I was able to access credentials from someone with EA, but did not go any further to remain ethical. EA which is known to be a terrible company with consumers, shows how terrible of a company they are not to return my email.
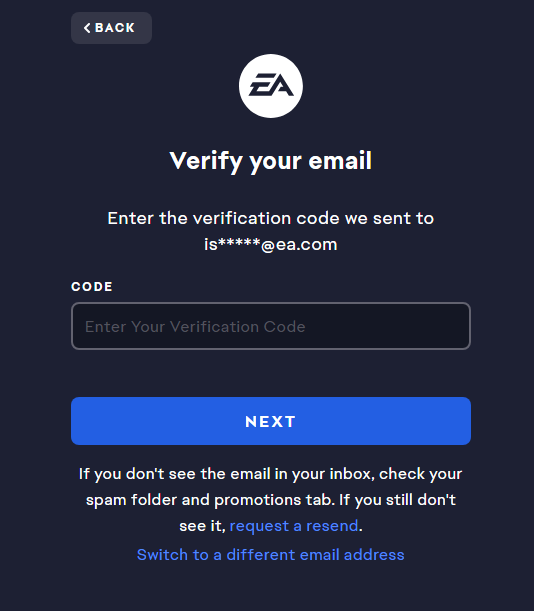
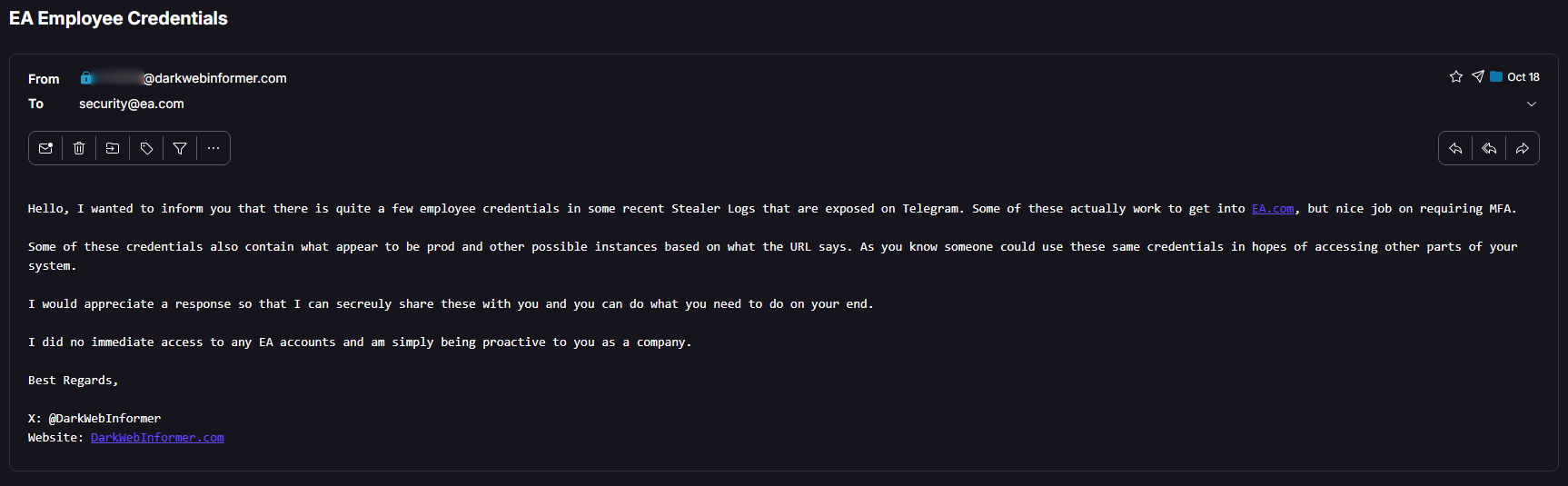
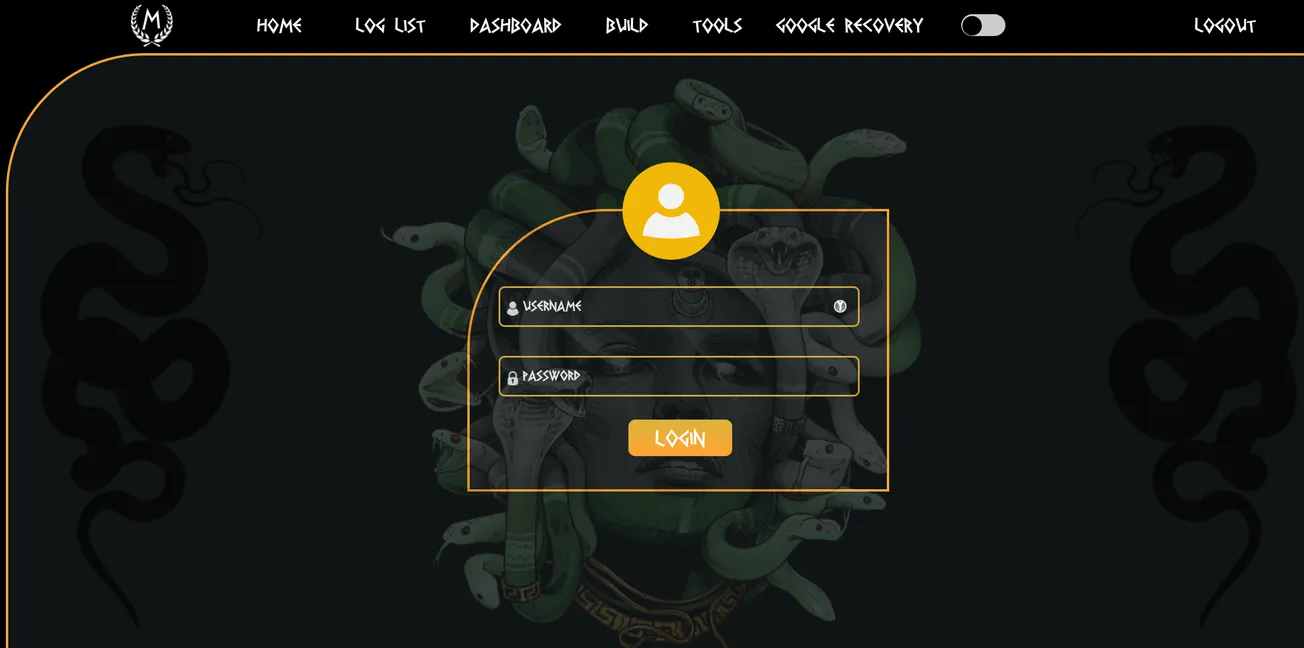
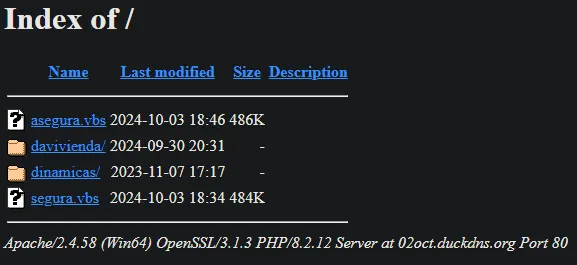
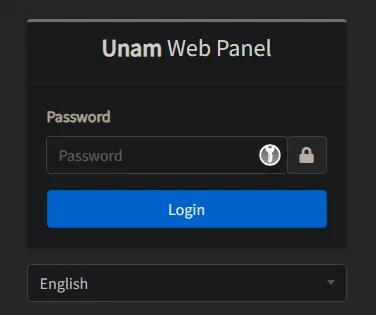
Moving on.. I was able to do the same exact thig with Salesforce.. but in this case the logs I were reviewing showed a DEV instance that was publicly available to login to. I've left part of it un-redacted. Salesforce was pretty quick in returning their message to me, as well as all responses. THIS... THIS is how a company should be proactive.
If you are a large company, don't be surprised if you here from me this week and the weeks after. BE PROACTIVE and DON'T BE LIKE EA!
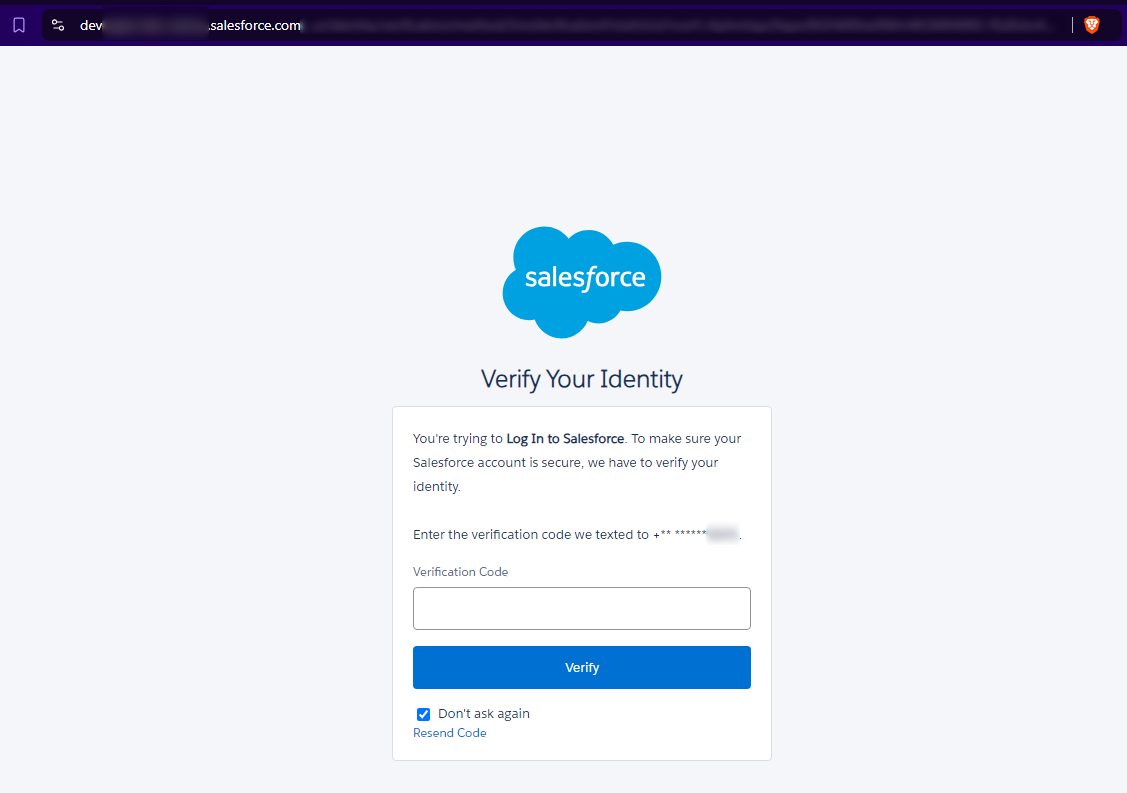
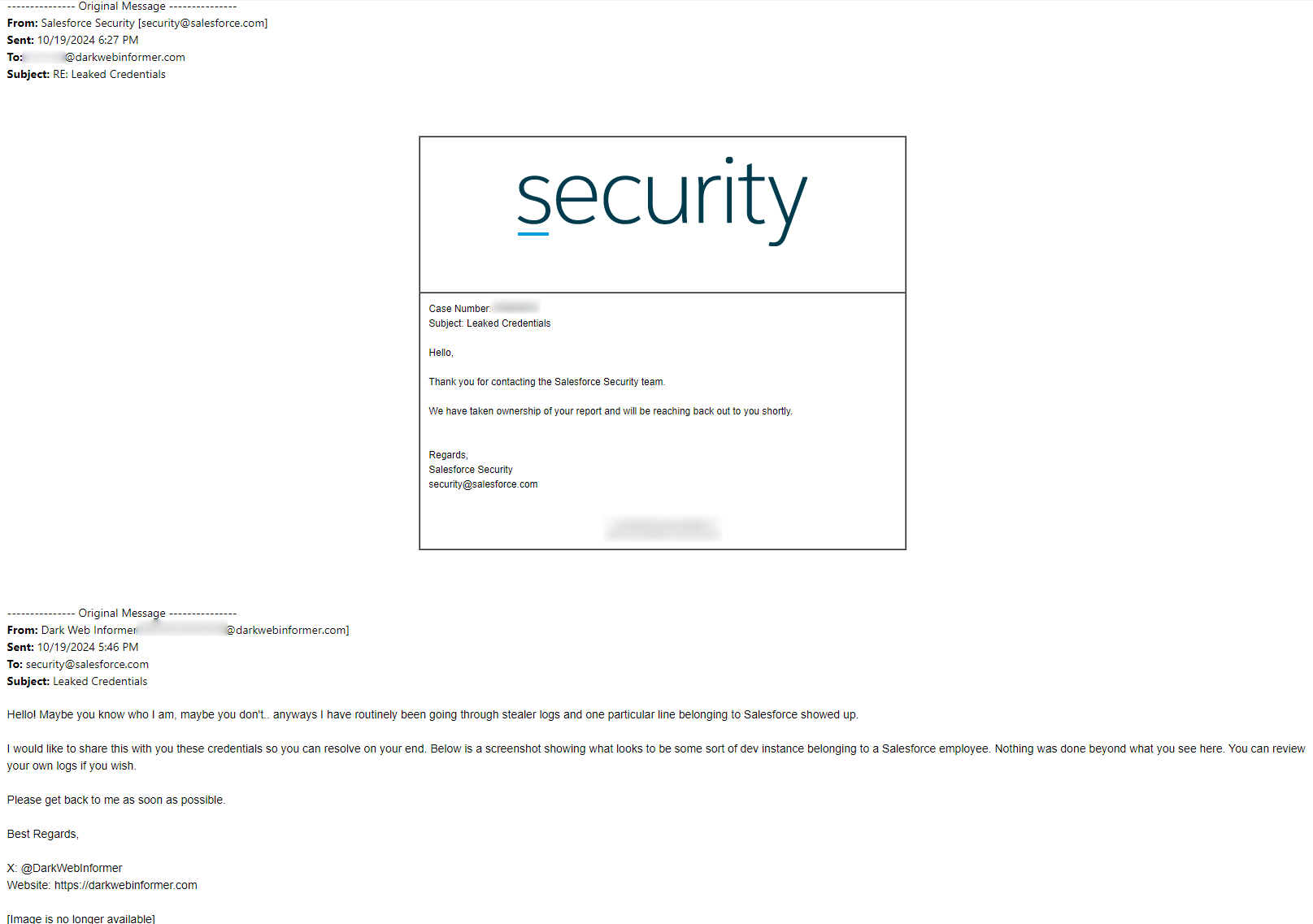
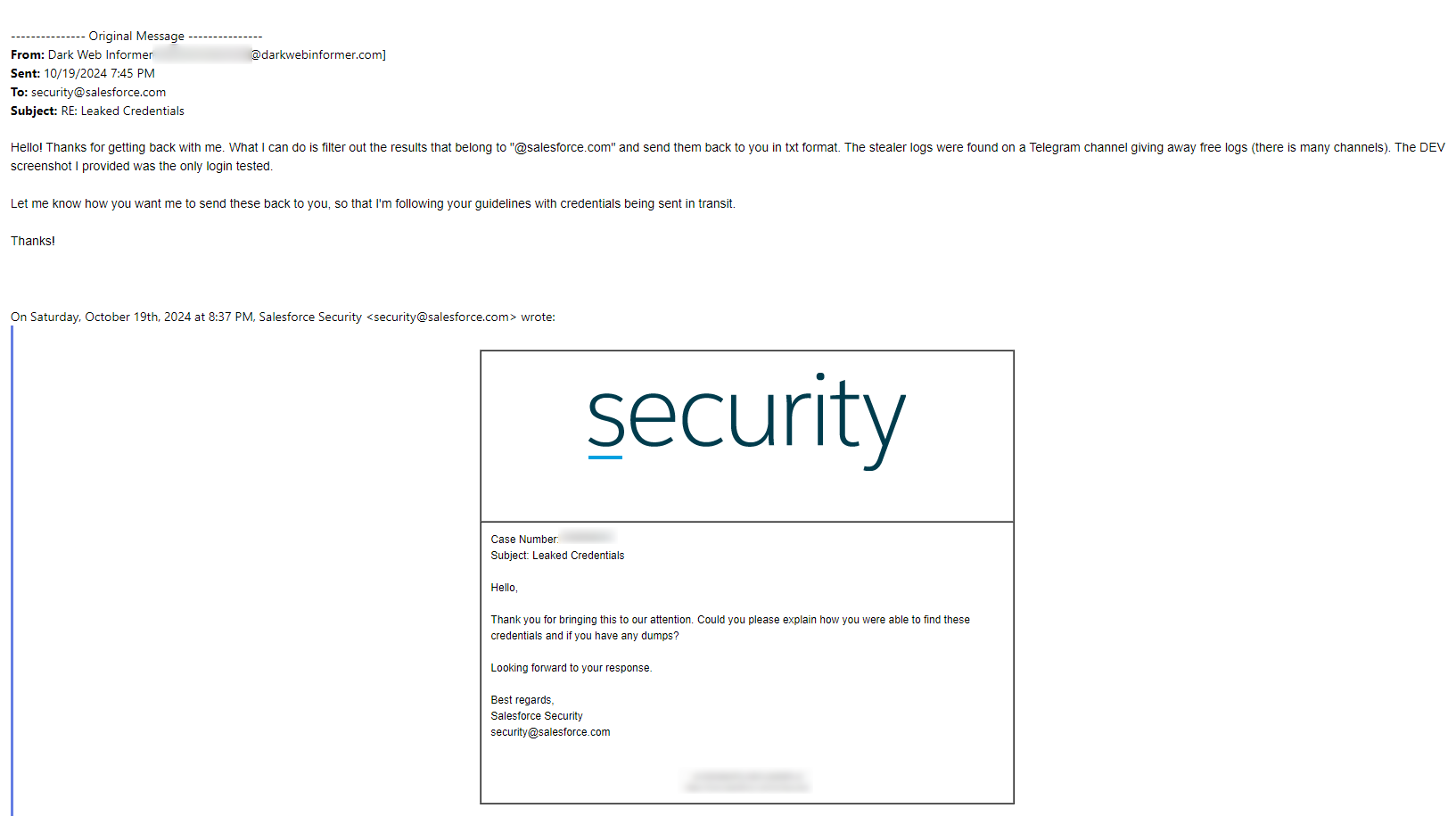
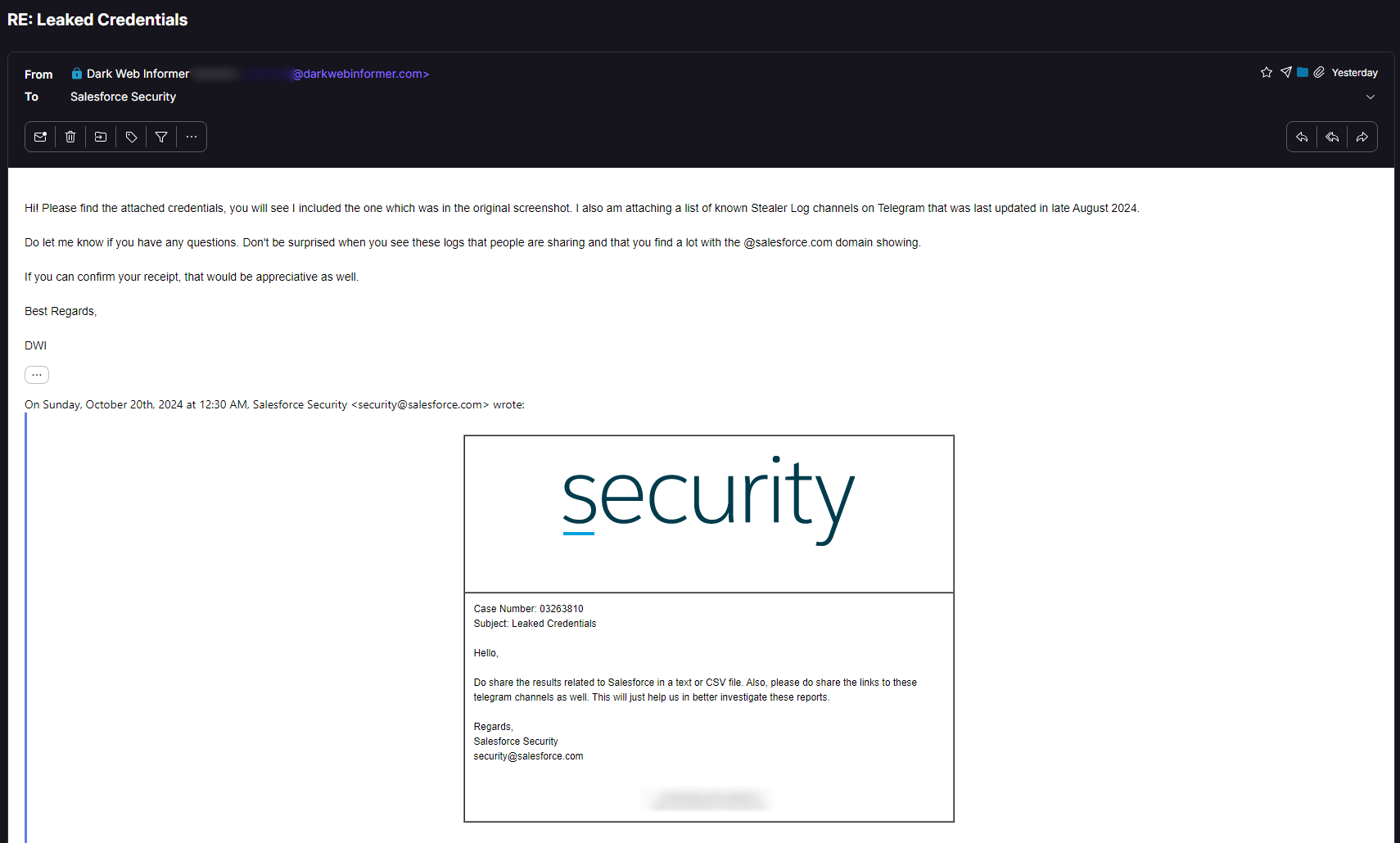
In both examples, the credentials were both in the same exact logs. The stealer family is well known.
I'll be sharing more of this in the future.
Rating: A for @salesforce
Rating: F for @EA