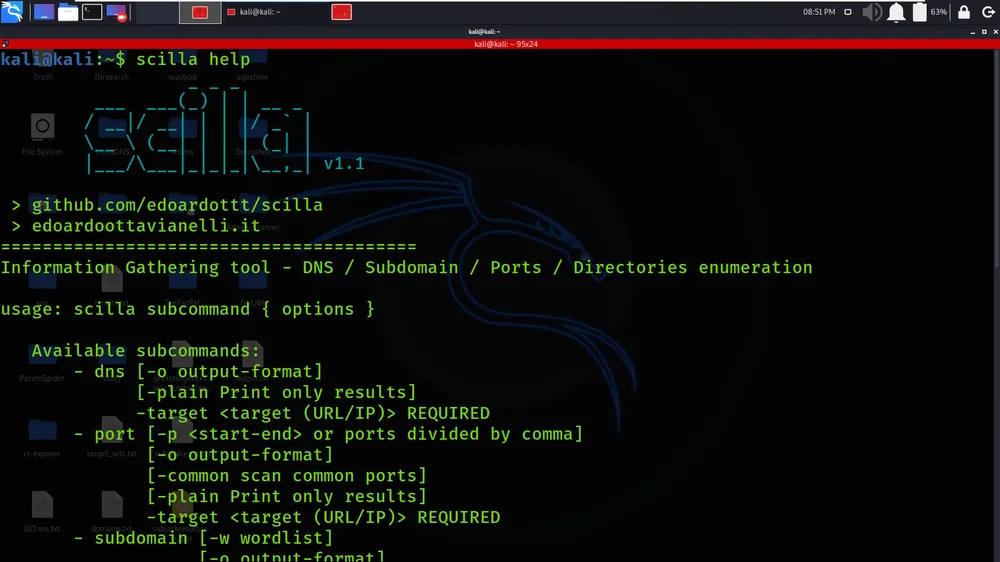
Link: https://www.shodan.io/
Shodan is a search engine for Internet-connected devices. Unlike traditional search engines like Google or Bing, which index web content, Shodan indexes information about devices connected to the Internet. This includes not only servers and websites but also Internet of Things (IoT) devices, webcams, routers, databases, and more.
Key Features of Shodan:
- Device Discovery: Shodan can discover a wide variety of devices connected to the Internet, including webcams, routers, servers, and industrial control systems.
- Port Scanning: It provides insights into the open ports on devices, which can indicate what services or applications are running.
- Security Analysis: Shodan is widely used for security research as it can identify vulnerabilities and security misconfigurations in Internet-connected devices. Researchers and organizations use it to find exposed devices and address security issues.
- Filtering and Searching: Users can filter results by country, operating system, service, or network, making it a powerful tool for understanding the landscape of connected devices in specific sectors or regions.
- Data Access: Shodan provides APIs that allow developers and researchers to integrate its data into their applications or conduct large-scale analysis.
- Reports and Alerts: Users can set up alerts to notify them when certain types of devices or specific vulnerabilities appear on the Internet.
- Research and Intelligence: Shodan is a valuable tool for cybersecurity professionals, researchers, and law enforcement agencies for conducting digital investigations and threat intelligence gathering.
Use Cases:
- Security Audits: Organizations can use Shodan to find and secure their exposed devices.
- Research: Academics and researchers use Shodan to study the IoT landscape and device vulnerabilities.
- Threat Intelligence: It is used to monitor for malicious activity and understand the exposure of critical infrastructure.