Dell Technologies Employee Database Exposed with 5K+ Records and Internal Network Access
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more – independently from the above standard subscriptions.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
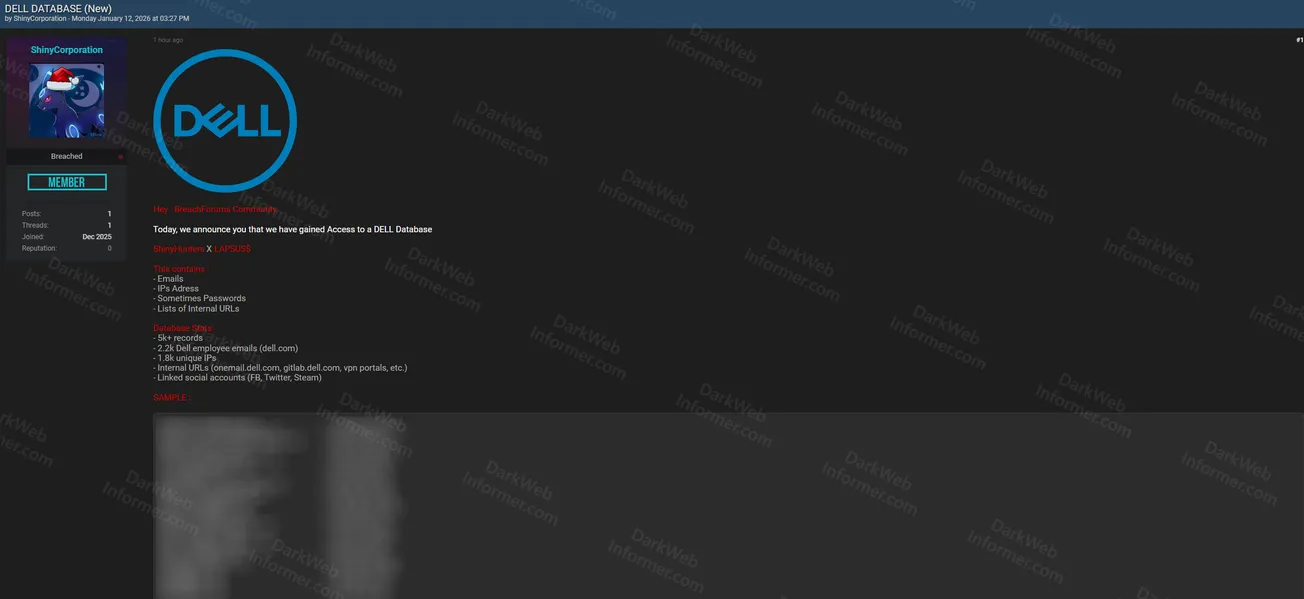
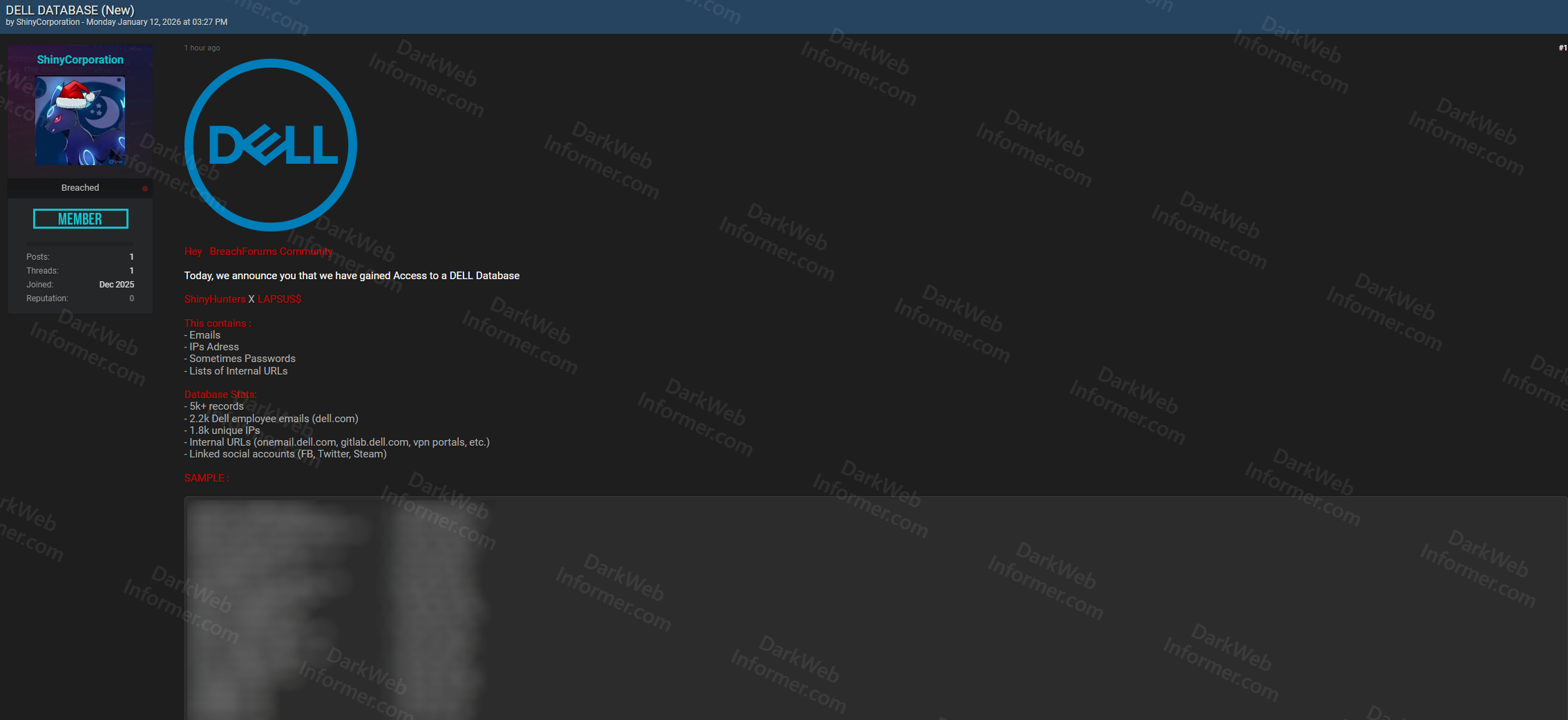
Threat actors using the handles "ShinyCorporation" and "LAPSUS" claim to have gained unauthorized access to a Dell Technologies database. The compromised dataset reportedly contains employee-related information including email addresses, IP addresses, occasional passwords, and lists of internal URLs.
- Collaboration: ShinyHunter X LAPSUS
- Total Records: 5K+ records
- Employee Emails: Approximately 2.2K Dell employee email addresses (dell.com)
- Unique IP Addresses: Around 1.8K unique IPs
- Passwords: Some passwords included in the dataset
- Internal URLs: Lists of internal Dell URLs and systems
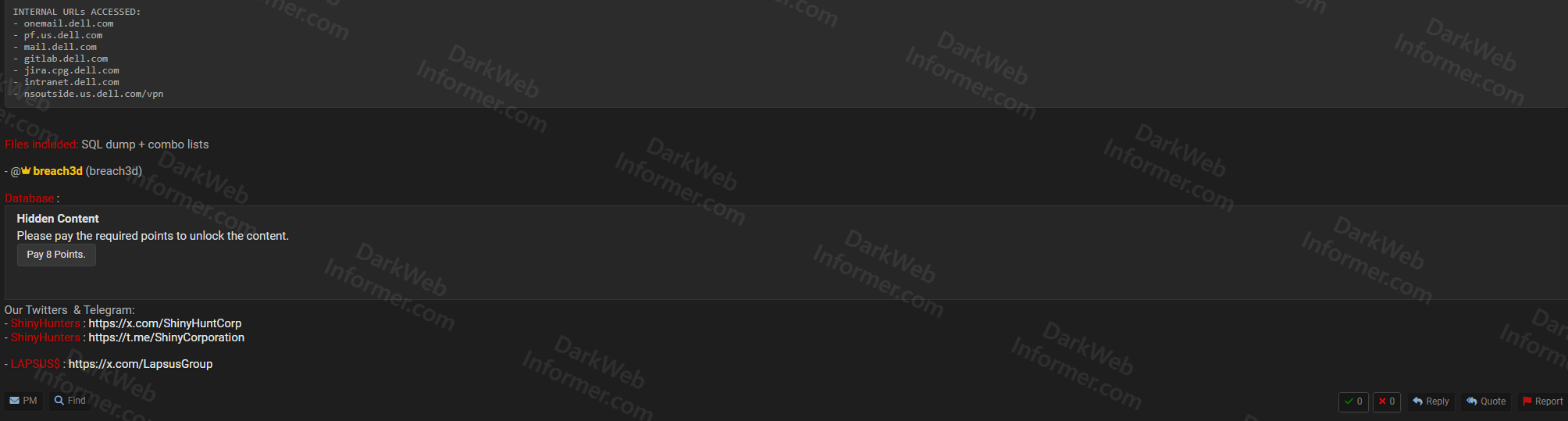
- Internal Systems Accessed: onemail.dell.com, pf.us.dell.com, mail.dell.com, gitlab.dell.com, intra.cps.dell.com, cstools.dell.com, nsoutside.us.dell.com/vpn
- Linked Social Accounts: Facebook, Twitter, Steam accounts linked to employee profiles
- Sample Data: Email addresses and IP addresses visible in screenshot
- Files Included: SQL dump + combo lists
- Access Method: Data hosted at breach3d (breach3d)
- Social Media: Twitter (@ShinyHuntCorp), Telegram (t.me/ShinyCorporation), LAPSUS (x.com/LapsusGroup)
Indicators of Compromise (IOCs)
ShinyHunters Twitter/X
https://x[.]com/ShinyHuntCorp
Note: This Twitter/X account is associated with the ShinyHunters threat actor group.
ShinyHunters Telegram
https://t[.]me/ShinyCorporation
Note: This Telegram channel is associated with the ShinyHunters threat actor group.
LAPSUS$ Twitter/X
https://x[.]com/LapsusGroup
Note: This Twitter/X account is associated with the LAPSUS$ threat actor group.
Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Dark Web Informer © 2026 | Cyber Threat Intelligence