Saudi Arabia Government Postal System Domain Controller Access Allegedly For Sale
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more – independently from the above standard subscriptions.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
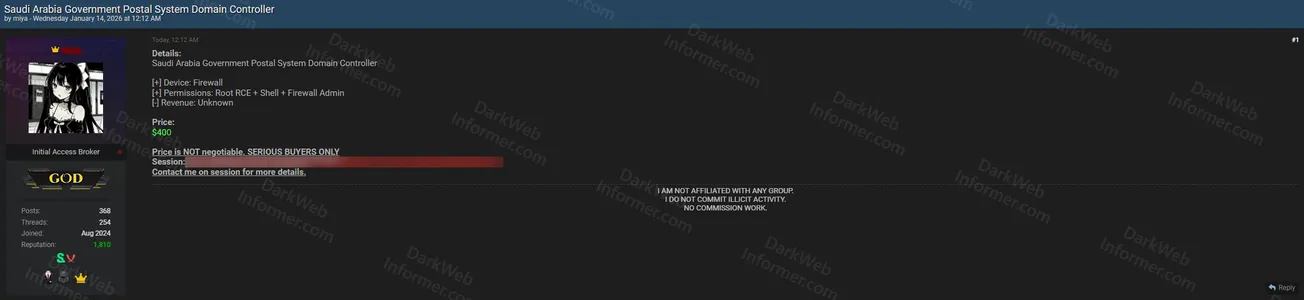
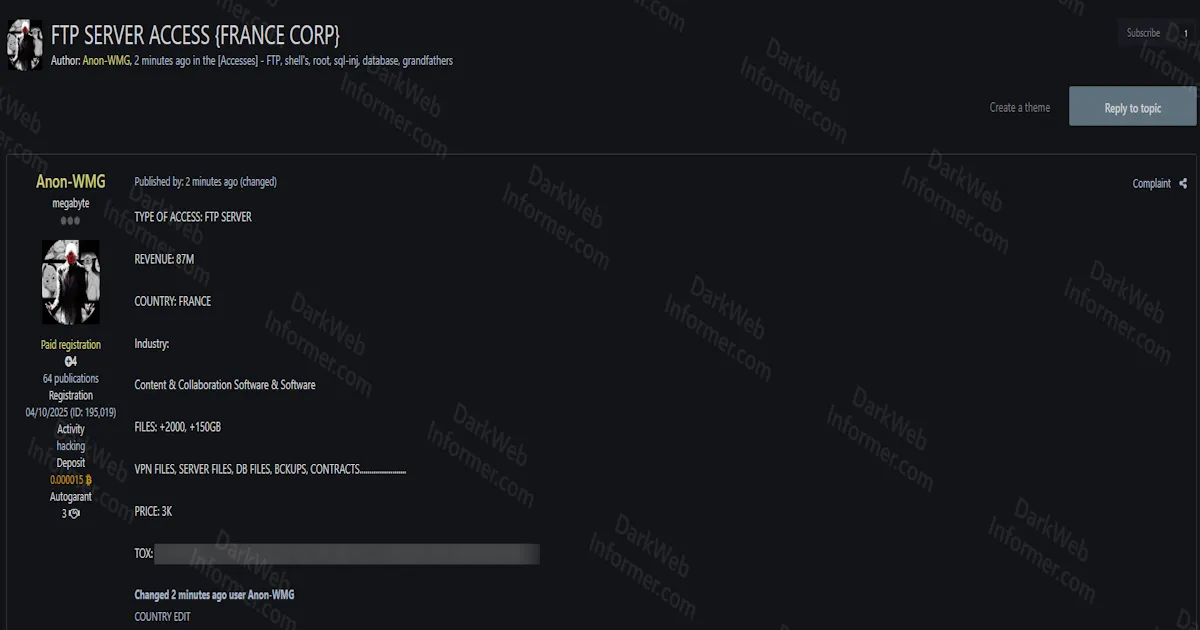
An initial access broker operating under the handle "miya" claims to be selling unauthorized access to the Saudi Arabia Government Postal System Domain Controller. According to the advertisement posted on BreachForums, the threat actor is offering access to a firewall device with root-level Remote Code Execution capabilities, shell access, and firewall administrator permissions. The claimed access includes unknown revenue potential for the compromised system.
The threat actor has set the price at $400 USD and explicitly states the offer is non-negotiable, intended for serious buyers only. The listing includes a session ID for potential buyers to verify the access. The seller emphasizes they are not affiliated with any group, do not commit illicit activity, and are offering this access without commission work. Interested parties are instructed to contact the threat actor via their session for additional details.