Russian Eco-Fuel Company Palevo Allegedly Breached with 2021 User Registration Data Leaked
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more – independently from the above standard subscriptions.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
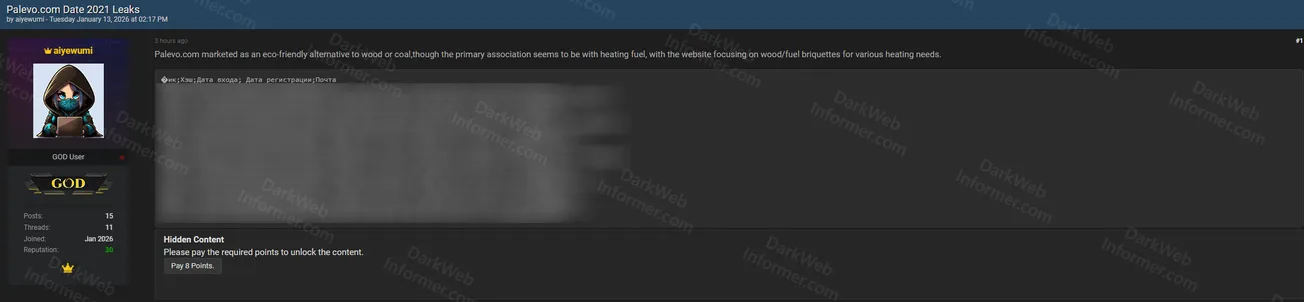
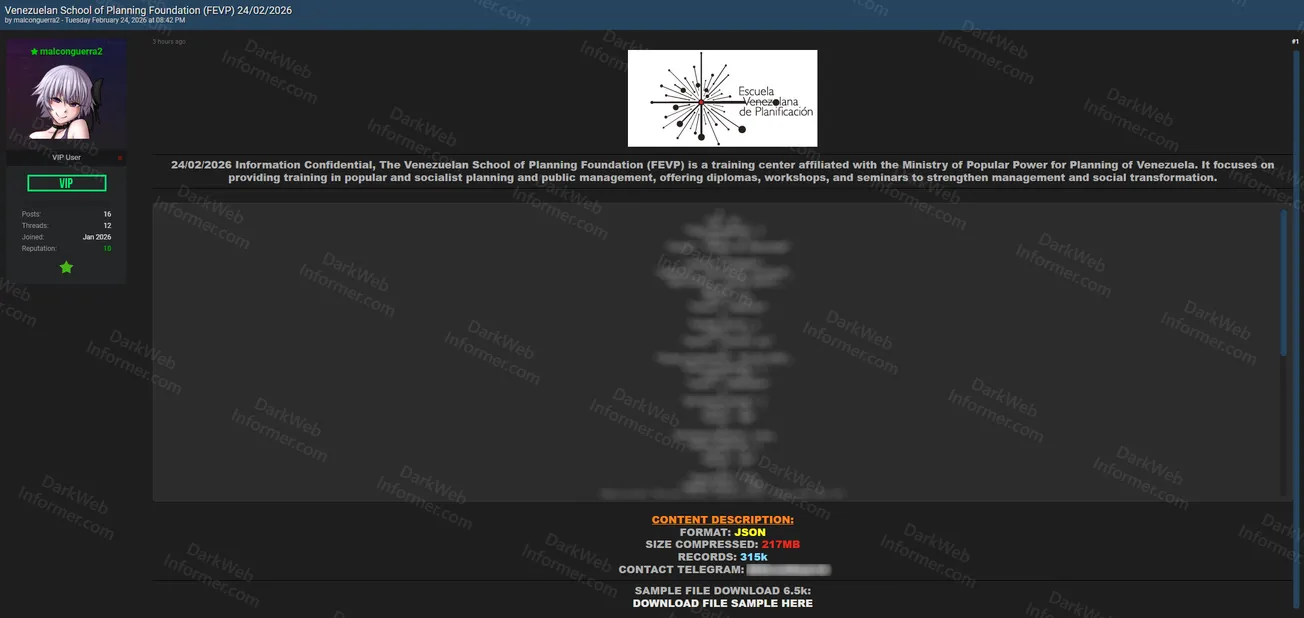
A threat actor using the handle "aiyewumi" claims to have leaked historical user registration data from Palevo.com, a Russian company marketed as an eco-friendly alternative to wood or coal heating fuel. The company's primary focus is on wood and fuel briquettes for various heating needs. The leaked data is dated from 2021 and contains user account information.
- Company Description: Eco-friendly alternative to wood or coal heating fuel, specializing in wood/fuel briquettes for heating needs
- Data Origin: 2021 user registration records
- Usernames: Customer account usernames
- Email Addresses: Customer email addresses
- Account Identifiers (bander): Unique account identification codes
- Registration Timestamps (Дата регистрации): Date and time of account registration
- Sample Data Format: Screenshot shows structured data fields including username, email, bander ID, and registration date/time
- Sample Usernames Visible: Including entries like JmzyXsqy, qooXMqxocj, woodlll, and various others
- Sample Email Domains: Multiple Russian email domains visible (@list.ru, @mail.ru, @bk.ru, @yandex.ru, @gmail.ru, etc.)
- Date Range Visible: Registration dates from 2006 to 2008 visible in sample data
- Post Status: Posted 3 hours ago (as of alert time)
- Access: Hidden content requiring payment of 8 points to unlock
Indicators of Compromise (IOCs)
No IOCs were disclosed by the threat actor in this claim.
Breach Claim URL
Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Dark Web Informer © 2026 | Cyber Threat Intelligence