Recurpay SaaS Subscription Platform Allegedly Breached Again, Exposing Order and Payment Data
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
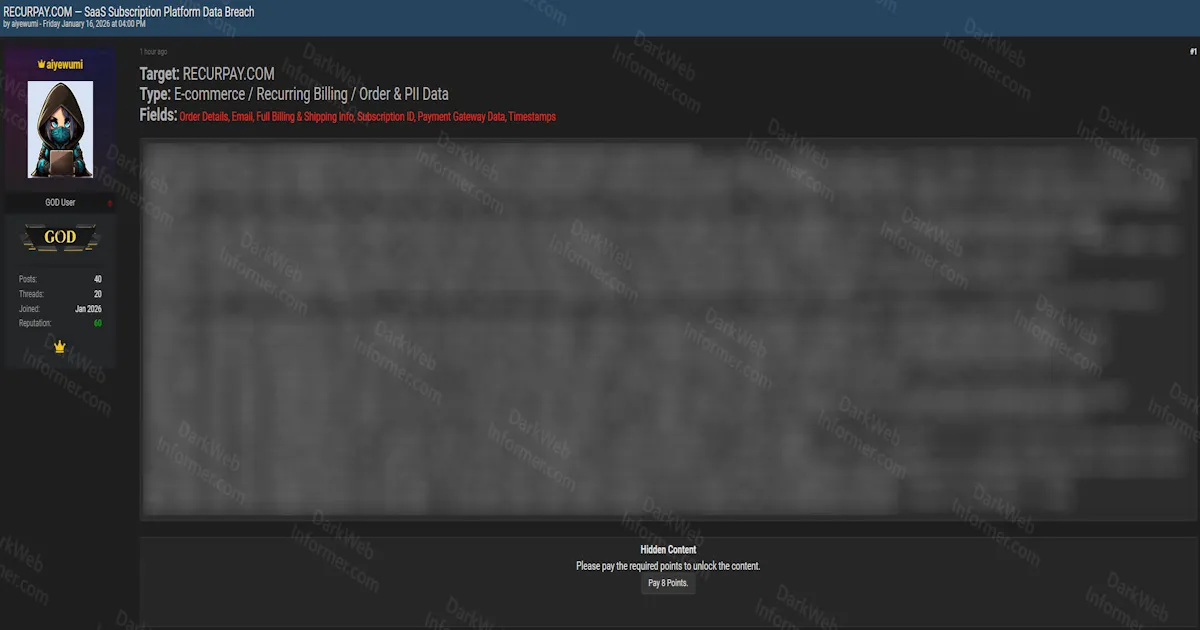
A threat actor operating under the handle "aiyewumi" claims to have breached Recurpay, an e-commerce recurring billing and subscription management SaaS platform based in India. The post describes Recurpay as handling "E-commerce / Recurring Billing / Order & PII Data" and lists the exposed fields as order details, email, full billing and shipping info, subscription ID, payment gateway data, and timestamps.
The sample data visible in the screenshot shows records containing customer names, email addresses, phone numbers, physical addresses across various Indian cities (Goa, West Bengal, Tamil Nadu, Maharashtra, Karnataka, Assam, Rajasthan), order amounts in INR, shipping methods ("Standard Shipping"), product details ("Friends Easy Adult Diapers.123", "Friends Premium Diapers", "Friends Premium Diaper Pants"), subscription statuses (fulfilled, cancelled), and timestamps ranging from 2020 to 2022. This marks the second reported breach of the platform, following a previous incident on July 2, 2025.
This post is for subscribers on the Plus, Pro and Elite tiers
SubscribeAlready have an account? Sign In