Polish Logistics Giant InPost Allegedly Breached with 2 Million Employee Records Exposed
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more – independently from the above standard subscriptions.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
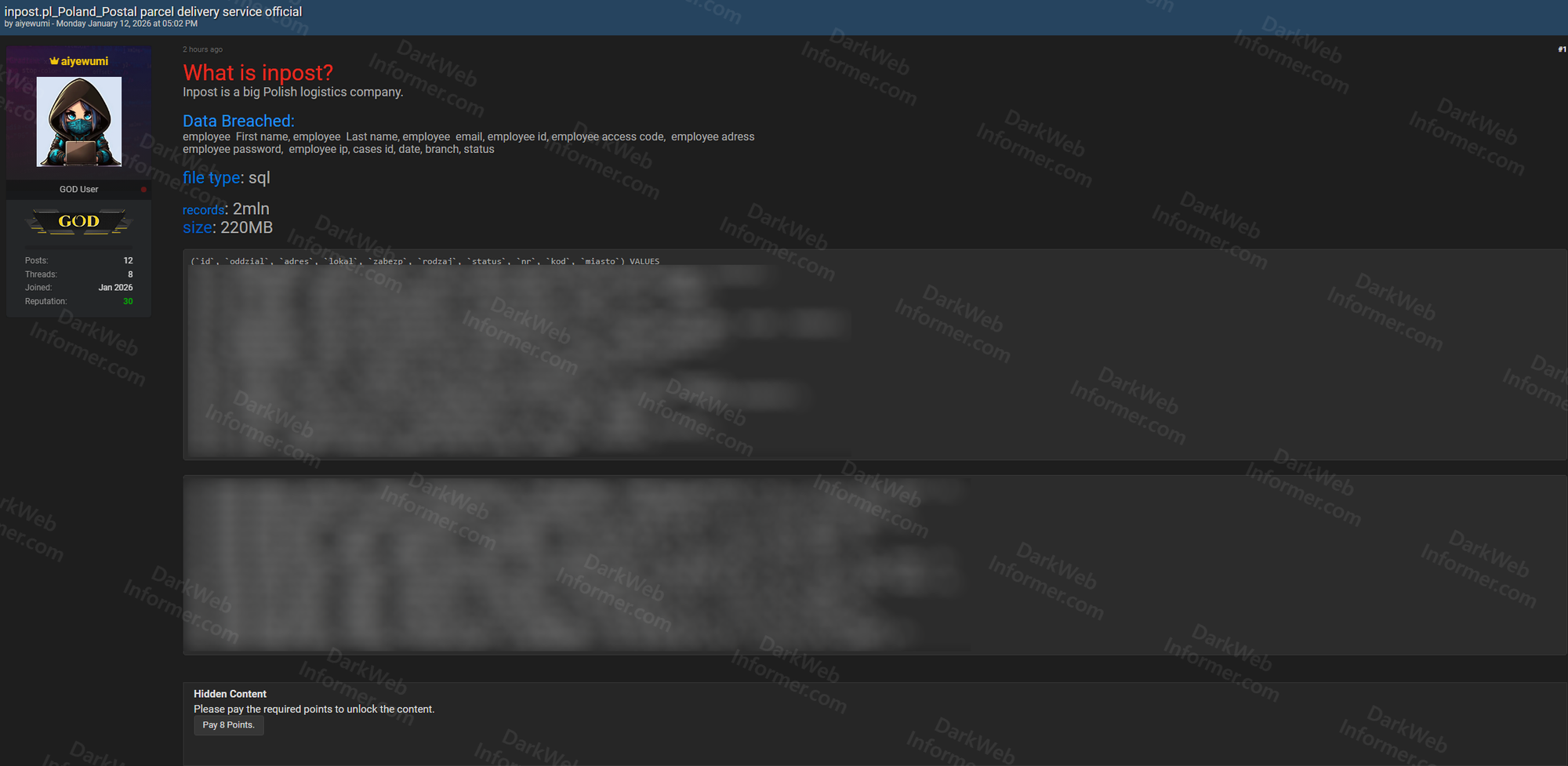
A threat actor using the handle "aiyewumi" claims to have breached the database of InPost, described as a major Polish logistics company specializing in postal and parcel delivery services. The exposed data is reportedly in SQL format and approximately 220MB in size, containing around 2 million employee records.
- Company Description: InPost is a big Polish logistics company
- File Type: SQL database
- Total Records: Approximately 2 million records
- File Size: 220MB
- Employee First Names: Full employee first name data
- Employee Last Names: Full employee last name data
- Employee Emails: Corporate email addresses
- Employee IDs: Internal employee identification numbers
- Employee Access Codes: System access codes and credentials
- Employee Addresses: Physical address information
- Employee Passwords: Password data (likely hashed)
- Employee IP Addresses: IP address logs
- Case IDs: Internal case identification numbers
- Dates: Timestamp and date information
- Branch Information: Branch location and assignment data
- Status Information: Employee or case status indicators
- Sample Data: SQL data visible in screenshot showing InPost locations (Centrala, Gdynia, Katowice, etc.)
- Post Status: Posted 2 hours ago (as of alert time)
- Access: Hidden content requiring payment of 8 points to unlock
Indicators of Compromise (IOCs)
No IOCs were disclosed by the threat actor in this claim.
Breach Claim URL
Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Dark Web Informer © 2026 | Cyber Threat Intelligence