Officers from Poland's Central Bureau for Combating Cybercrime (CBZC) arrested a 47-year-old man suspected of creating, obtaining, and distributing computer programs used to illegally access information stored in IT systems. The arrest was carried out jointly by CBZC's Katowice and Kielce branches in the Małopolska (Lesser Poland) region.
During a search of the suspect's residence, officers seized a computer and mobile phones. Forensic analysis of the devices revealed stored digital data including logins, passwords, credit card numbers, and server IP addresses — data that could be used to breach electronic security systems and carry out various attacks, including ransomware deployments.
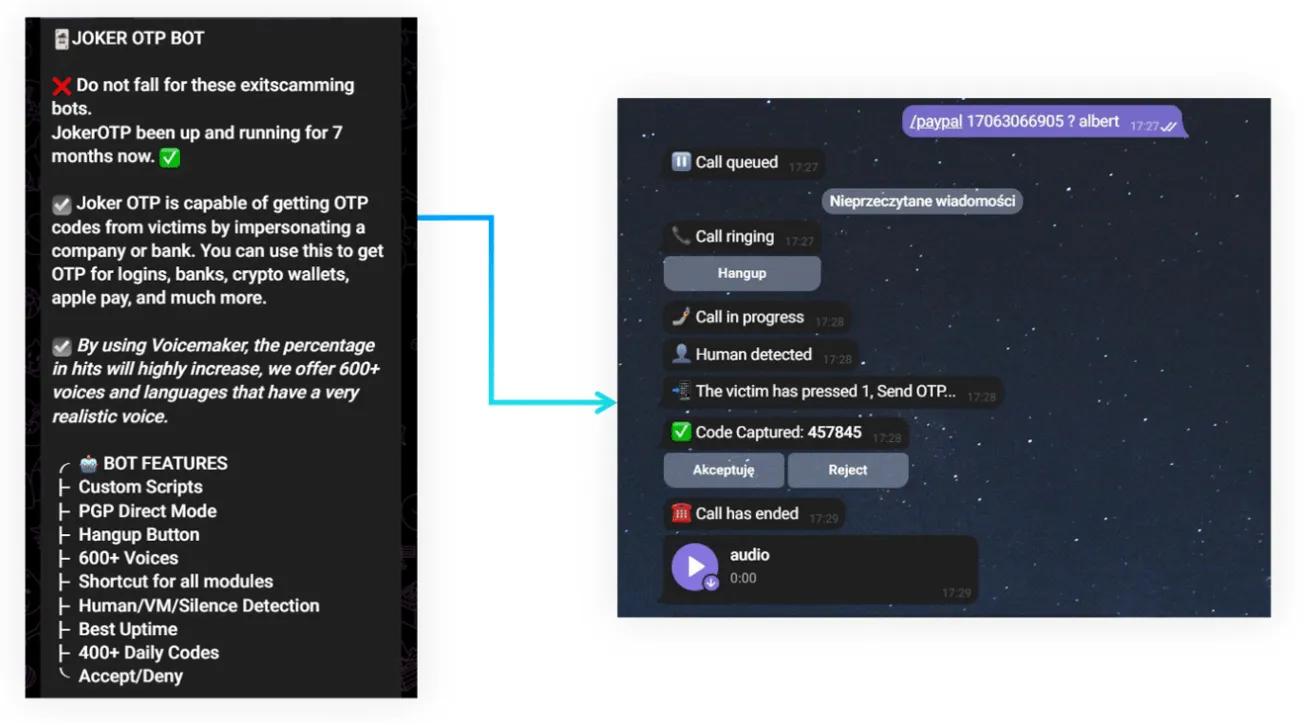
Investigators also found that the suspect had been communicating with the Phobos cybercriminal group through encrypted messengers. Phobos is a well-known ransomware operation.
The man was charged under Article 269b § 1 of the Polish Penal Code, which covers the creation, acquisition, and distribution of tools used for unauthorized access to computer systems. He faces up to 5 years in prison. The investigation is being supervised by the District Prosecutor's Office in Gliwice.
Connection to Europol's Operation Aether
The arrest was part of Poland's participation in Operation Aether, coordinated by Europol. The operation targeted individuals tied to the Phobos ransomware ecosystem, hitting both the backend infrastructure (RaaS services) and the operators/affiliates responsible for carrying out intrusions and encrypting victim data. Key outcomes of the broader operation included the extradition of an alleged Phobos administrator to the United States and coordinated arrests across Europe and beyond, combined with technical takedowns of cybercriminal infrastructure.
About Phobos
- Phobos operated as a Ransomware-as-a-Service (RaaS) model, where the developers provided the ransomware to affiliates who carried out attacks and split the profits.
- The group and its affiliates victimized over 1,000 targets worldwide, including hospitals, schools, nonprofits, government entities, and private companies.
- Known victims include public schools in California and Connecticut, healthcare providers in Maryland, and a contractor working with the U.S. Department of Defense.
- According to U.S. Department of Justice filings, total ransom payments linked to Phobos exceeded $16 million.
- Independent analysis (ThreatDown) put the average individual ransom demand at roughly $54,000, though actual demands varied widely.
- Exact revenue figures are difficult to pin down due to the use of cryptocurrency and darknet infrastructure.