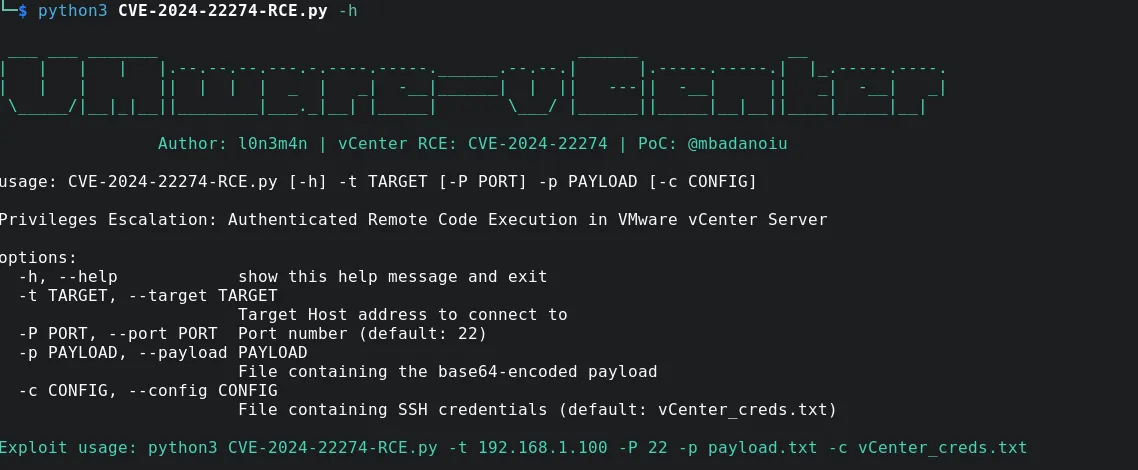
Privilege Escalation: VMware vCenter Server Authenticated RCE
The “com.vmware.appliance.recovery.backup.job.create” and the “com.vmware.appliance.recovery.backup.validate” API components are vulnerable to a flag injection attack that can be leveraged to execute arbitrary commands as the root user on the target system."
To work with this PoC exploit, you must have valid credentials and log in to the VMware vCenter Server shell via SSH. The user must have the "admin" role, as specified in the vcenter_creds.txt file.
$ git clone https://github.com/l0n3m4n/CVE-2024-22274-RCE.git
$ cd CVE-2024-22274-RCE
$ python3 -m venv venv && source venv/bin/activate
$ pip install -r requirements.txt