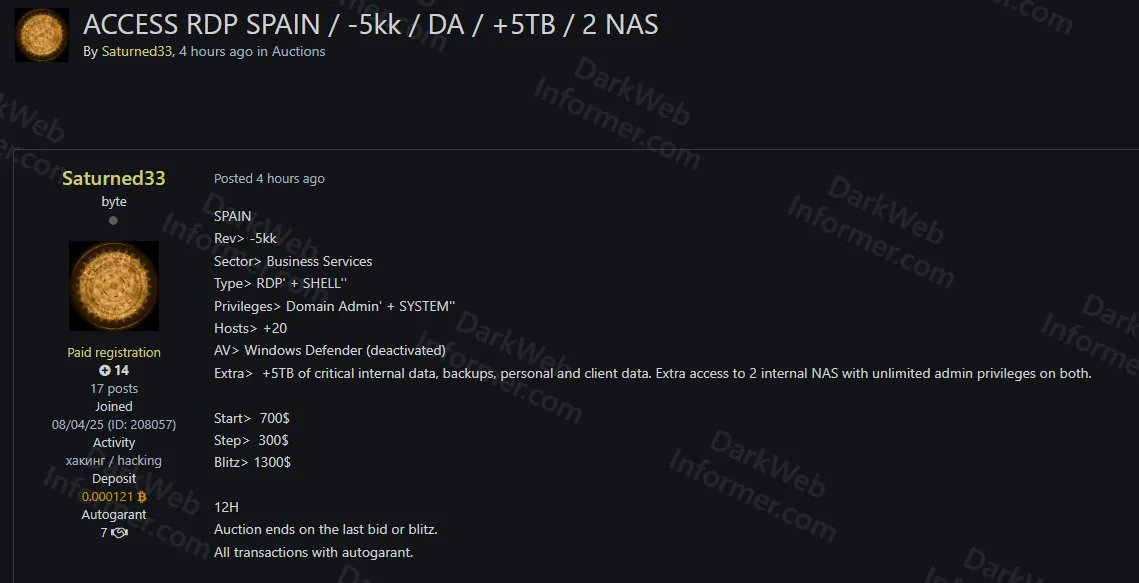
New Zealand E-commerce Store CMS Admin Access Allegedly for Sale with Active Payment Redirect
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
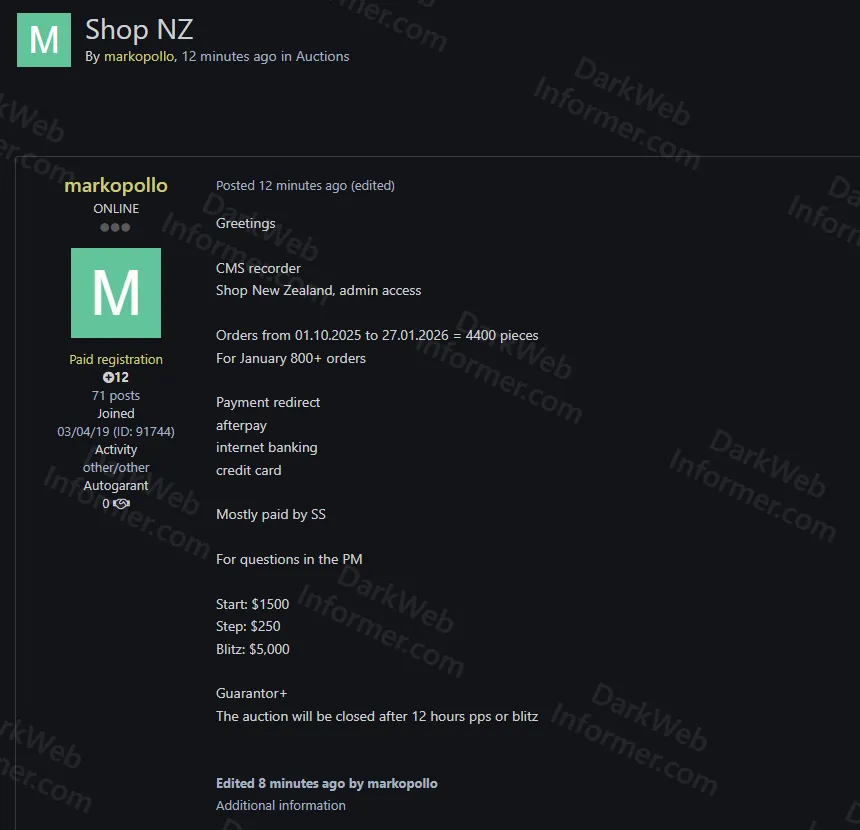
A threat actor operating under the handle "markopollo" is auctioning unauthorized CMS administrator access to an unidentified New Zealand-based online shop on the Exploit forum. According to the listing, the access includes a "CMS recorder" and admin-level privileges to the shop's content management system. The threat actor claims the shop has processed 4,400 orders between October 1, 2025 and January 27, 2026, with 800+ orders in January 2026 alone.
The listing indicates that a payment redirection mechanism has been deployed on the compromised store, capable of intercepting payments through Afterpay, internet banking, and credit card transactions. The threat actor notes that payments are "mostly paid by SS" (likely referring to a payment processor or screenshot verification). The auction starts at $1,500 USD with a $250 step increment and a blitz (buy-it-now) price of $5,000 USD. The auction runs for 12 hours after the last bid or blitz purchase, with Guarantor+ escrow protection.
This post is for subscribers on the Plus, Pro and Elite tiers
SubscribeAlready have an account? Sign In