Max Messenger Suffers Alleged Complete Infrastructure Breach Exposing 154 Million Users
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more – independently from the above standard subscriptions.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
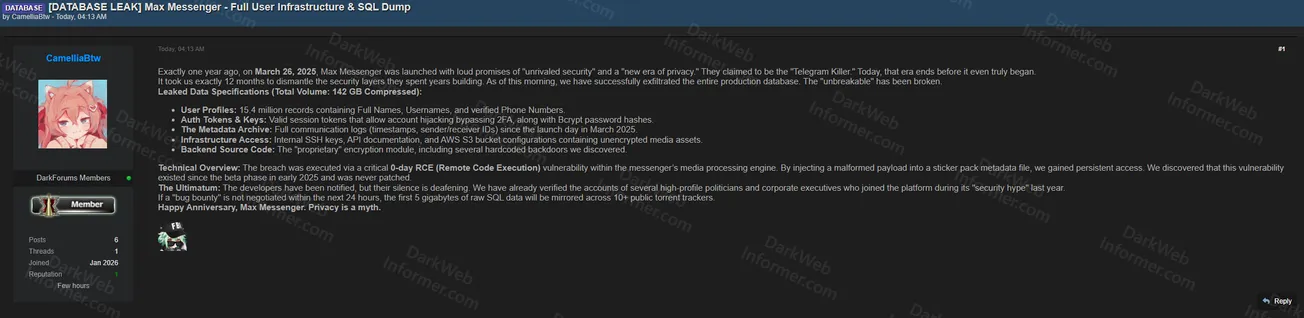
A threat actor operating under the handle "CamelliaBtw" claims to have fully compromised Max Messenger, a messaging platform that launched on March 26, 2025. The threat actor alleges that Max Messenger promoted itself with claims of "unrivaled security" and as a "new era of privacy," positioning itself as the "Telegram Killer." According to the post, this breach occurred exactly one year after the platform's launch.
The threat actor claims the dataset includes approximately 154 million user records containing full names, usernames, and verified phone numbers. The breach allegedly also includes valid session tokens that allow account hijacking by bypassing 2FA, along with Bcrypt password hashes. Additional compromised data reportedly consists of full communication logs with timestamps and sender/receiver IDs, internal SSH keys, API documentation, and AWS S3 bucket configurations containing unencrypted media assets. The threat actor also claims to have obtained the backend source code, including what they describe as a "proprietary" encryption module with several hardcoded backdoors.
According to the claim, the breach was executed via a critical 0-day Remote Code Execution vulnerability within the messenger's media processing engine. The threat actor states they injected a malformed payload into a sticker pack metadata file to gain persistent access. The post indicates the breach was executed within 5 days, remained undetected for 299 days, and was never patched.
The threat actor notes that verified accounts of several high-profile politicians and corporate executives who joined the platform during its "security hype" last year are included in the compromised data. They claim the first 5 gigabytes of raw SQL data will be mirrored across 10+ public torrent trackers within the next 24 hours. The post concludes with: "Happy Anniversary, Max Messenger. Privacy is a myth."