Massive Initial Access Sale: 10K Webshells, 5K WHMCS Access, and 50K+ Compromised Domains Allegedly Offered
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more – independently from the above standard subscriptions.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
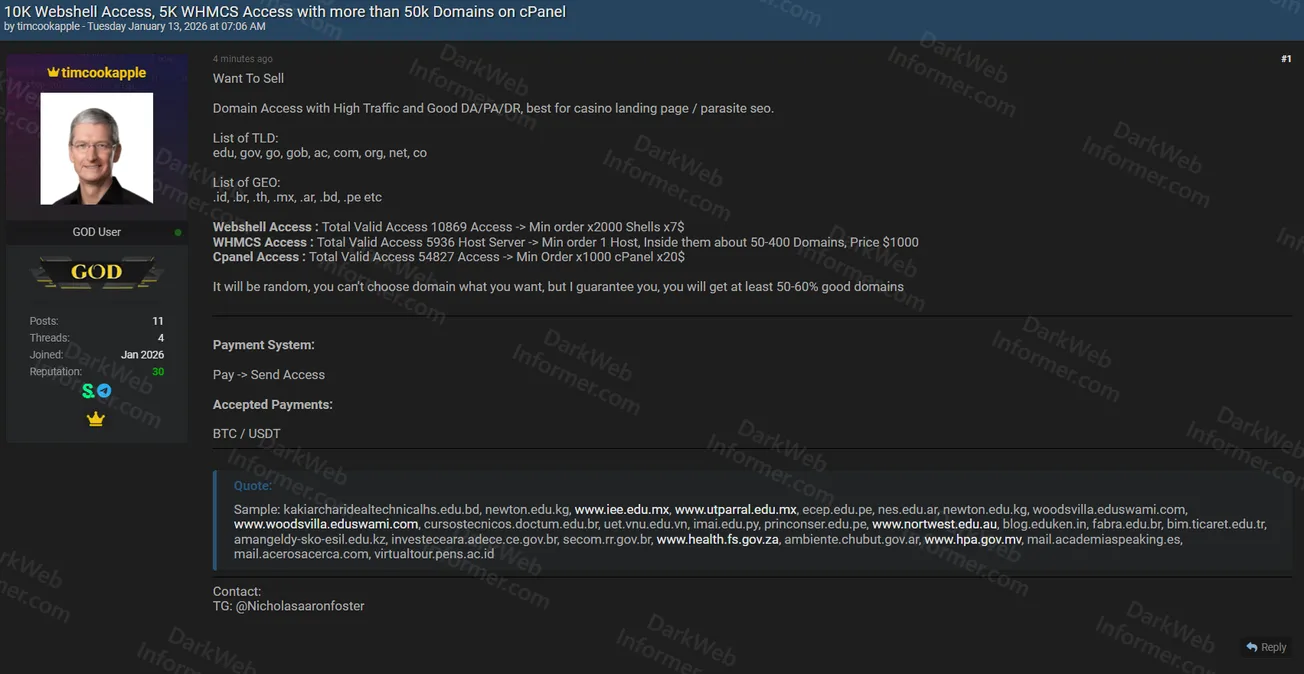
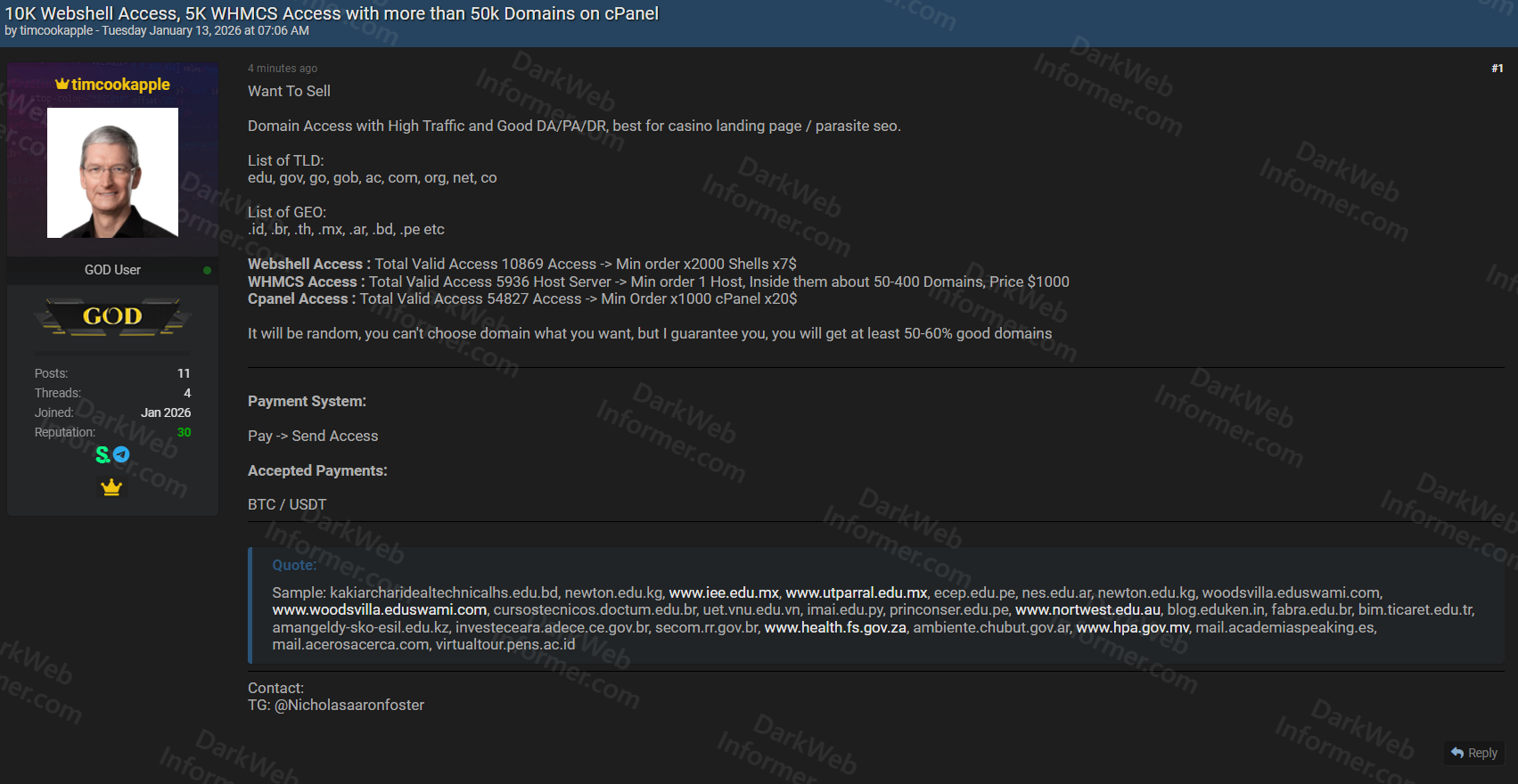
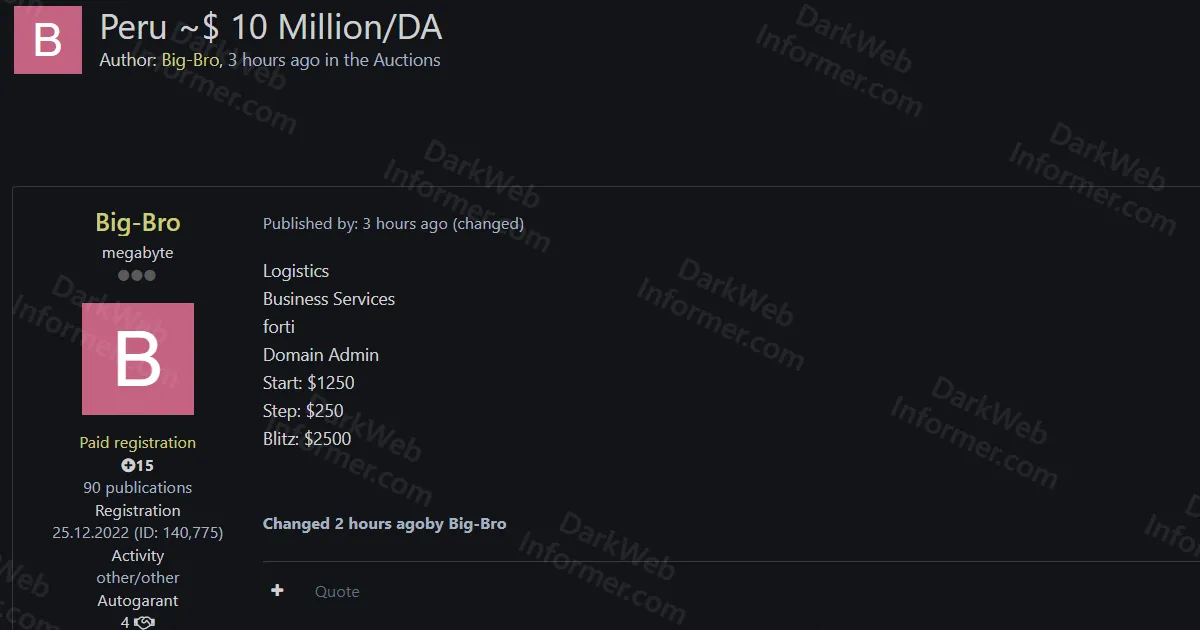
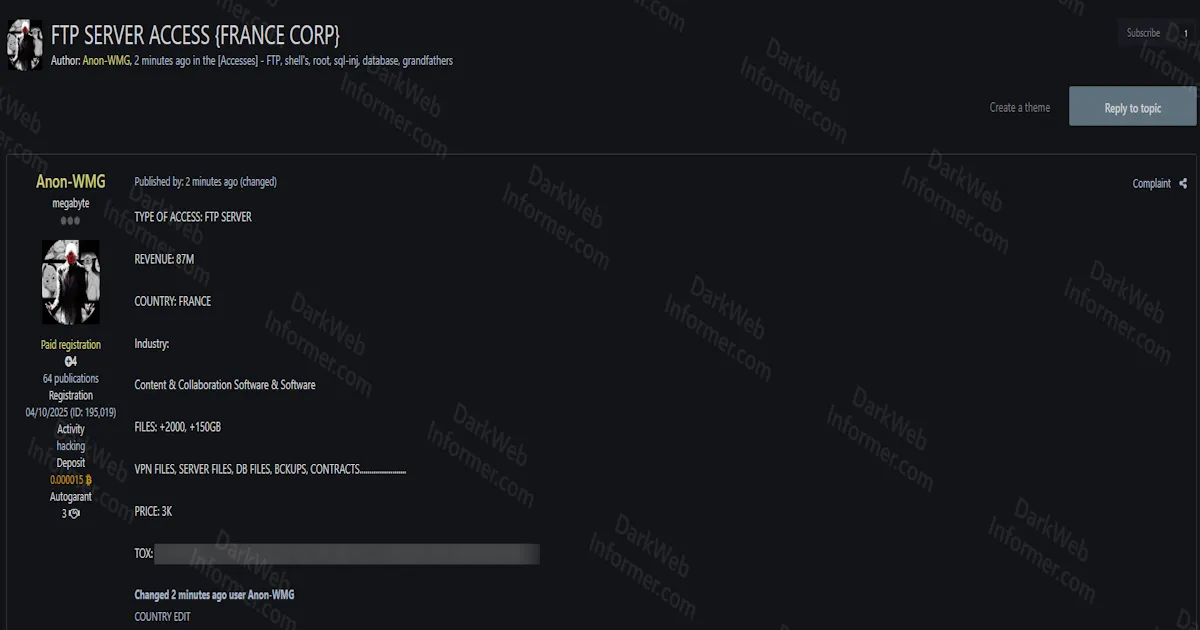
A threat actor using the handle "timcookapple" is offering a massive collection of unauthorized access credentials for sale, including webshells, WHMCS hosting server access, and cPanel control panel access affecting over 50,000 domains globally. The seller claims these compromised domains have high traffic and good domain authority metrics, making them ideal for malicious activities such as casino landing pages or parasite SEO campaigns.
- Purpose: Domain access with high traffic and good DA/PA/DR metrics for casino landing pages or parasite SEO
- Total Webshell Access: 10,869 valid webshell accesses
- Minimum Webshell Order: 2,000 shells x7$ (minimum purchase $14,000)
- Total WHMCS Access: 5,936 valid WHMCS host server accesses
- WHMCS Domain Count: Each host server contains approximately 50-400 domains
- WHMCS Pricing: $1,000 per host (minimum order 1 host)
- Total cPanel Access: 54,827 valid cPanel accesses
- Minimum cPanel Order: 1,000 cPanel x20$ (minimum purchase $20,000)
- Total Affected Domains: Over 50,000 domains across all access types
- Affected TLDs (Top-Level Domains): .edu, .gov, .go, .gob, .ac, .com, .org, .net, .co
- Affected GEOs (Geographic Extensions): .id, .br, .th, .mx, .ar, .bd, .pe, etc.
- Domain Selection: Random allocation (buyer cannot choose specific domains)
- Quality Guarantee: At least 50-60% of domains are guaranteed to be "good domains"
- Payment System: Pay first, then receive access
- Accepted Payments: BTC / USDT
- Contact Method: Telegram @Nicholasaaronfoster
- Sample Domains Visible: Multiple educational and government domains from various countries including Mexico, Australia, Myanmar, Peru, Argentina, Indonesia, Brazil, South Africa, and others
Indicators of Compromise (IOCs)
Telegram Handle
https://t[.]me/Nicholasaaronfoster
Note: This Telegram handle is the contact point for purchasing the unauthorized access credentials.
Initial Access Sale URL
Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Dark Web Informer © 2026 | Cyber Threat Intelligence