Original Link: http://dreadytofatroptsdj6io7l3xptbet6onoyno2yv7jicoxknyazubrad[.]onion/post/faa65a9e868bd63b6bbf. The donation address at the bottom of the article is NOT mine, it is that of the user who created this guide.
Images from the post are at the bottom!
mason's OpSec-Guide
This Guide of mine will be split into multiple parts. Don't wonder, I've teased parts of it with this account as well as /u/thenarrator (I don't use that account anymore though). Have a nice read! Donations are welcome, as this was a bit of work, look at the bottom of each post for my XMR-address.
Section 1 - What is OpSec?
OpSec is the short form of Operations-Security, the term originates from military practices.
Back then the military noticed, that it is very important that no information could fall into the hands of their enemies.
In our day and age it is harder than ever to stay anonymous and secure while using the internet, and be honest to yourself;
who doesn't want to experience the wonders of modern technology?
In conclusion what this guide aims for is really good anonymity which is supposed to be as close to perfect as possible, because
nothing is perfect ;).
1.1 - What do we have to protect from who?
To lay a foundation for our OpSec we first need to find out what data is to be protected and who it is to be protected from.
Obviously this may vary depending on your situation but in this guide specifically I will assume you are an average DW-User
(Deep-/Dark-web) that aims to be as anonymous as possible so that LE (Law-Enforcement) and other possible online threat-actors
can't get to you. So what data do we need to protect? The most important data will be all of your personal info (e.g. address,
email, full name, DOB etc.) and everything that may help one to identify it (e.g. IP-Address to name one factor). This process is
also referred to as building a/your threat model.
Section 2 - The Practice of Digital-OpSec
OpSec doesn't only matter in the digital world, yet it is still an extremely important aspect so we will talk about that first.
First of all you probably want to install a new OS (Operating-System) because chances are high you are reading this on Windows or
MacOs. These two popular OSs aren't recommended for our practices for two main reasons;
On one hand they don't give you much room to modify them which is something we need to be able to do,
On the other hand we shouldn't use them because they are closed source (that basically means their code is not public).
Using OpenSource-Software doesn't automatically improve your security but it has the benefit that the users can look through
the code and make sure that the alphabet boys can't backdoor your System with the kind of ease which the NSA could backdoor Windows.
I encourage you to read about it.
But what Operating System are we going to choose? Depends.
If you would say you are a rather tech-savvy person I enourage you to choose something like QubesOS, if you struggle to install
applications on Windows without the Microsoft-Store a rather bare-metal Linux distro (Distribution) may already be very challenging
for you. What Options are there?
-QubesOS
QubesOS works a lot with virtualization (imagine a computer in your computer, or multiple :D) but using it won't affect you like
a miracle and you won't automatically become impossible to trace, rather it really depends on how you use it. In QubesOS you can
operate different Qubes [which are basically just virtual-machines (google that term!], when that concept is used right it can be
a very solid foundation for your OpSec. The goal is to spread your activities through as many Qubes as possible. And then the
security measurements taken by you within the Qubes also matters a lot.
For that OS you will need a relatively beefy PC/Laptop. I recommend at least 16 GB of RAM.
-WhonixOS
Whonix is an OS which tries to offer privacy by heavily relaying on the TOR-Network (will be explained later on).
It consists of the Whonix-Gateway as well as the Whonix-Workstation. The gateway does what it's named after with the help of TOR
and the Workstation provides an isolated enviroment that runs user-applications. This Architecture provides Privacy mainly by
protecting against DNS-Leaks.
-A Hardened Bare-Metal Linux-Distro
The best example for a bare-metal distro is gentoo. But I am listing this option to provide an OS that may be a bit more
user-friendly than the first two so gentoo won't do the trick, rather i encourage you to look into something like Void-Linux,
with some Sandboxing (google this term) this distro can also be pretty secure. You may need to watch a tutorial regarding the install
and then get familiar with the Linux command-line.
How do you install your new OS of choice?
You want to download an application like balena-etcher (etcher.balena.io) which lets you write so called .iso files onto an
installation-medium (USB-Stick would be the best) and make it bootable. You can download the .iso file from the offical website
of the OS. Using balena-etcher is pretty self explanatory, if you are stuck somewhere watch a tutorial.
After finishing the creation of the bootable USB-Stick you want to restart your Laptop and boot into the BIOS (F9,F10,F11 or some
similar function-key) then (depending on BIOS) directly go to install your new OS or go into something like the BOOT-Section
and prioritize the USB. From there on the Installation-Wizard should guide you until the OS is installed. I encourage you to enable
FDE (Full-Disk-Encryption), that option should be available during the installation.
Note:
If not actively using you Laptop, shut it down! In sleep mode FDE is useless.
During installation don't enter any personal
info (e.g. real name as user) but this should also be common sense.
Congrats to you for having installed your new OS, time to get familiar.
Section 2.1 - Passwords
Store passwords in a good password manager — KeePass is recommended. I use KeePassXC as it doesn't store your data on a server.
Generate 40 character passwords containing a completely random assortment of upper and lowercase letters, numbers and symbols
that have high entropy.
Use a different password on each website.
Don't forget to set a good Password for KeePass, containing no dictionary-words.
Section 2.2 - Browser
When it comes to choosing your clear-net (opposite of dark-net) browser there are two options that I can recommend;
Chromium and Firefox.
Chromium is a security-oriented open source project behind the well known Chrome browser.
I use Firefox which is mostly personal preference. In this section we will go through hardening Firefox (do the same if you use
Chromium with a guide, there are many online, and un-google it). Hardening will increase your footprint but you shouldn't use either
without so that e.g. no telemetry data is sent.
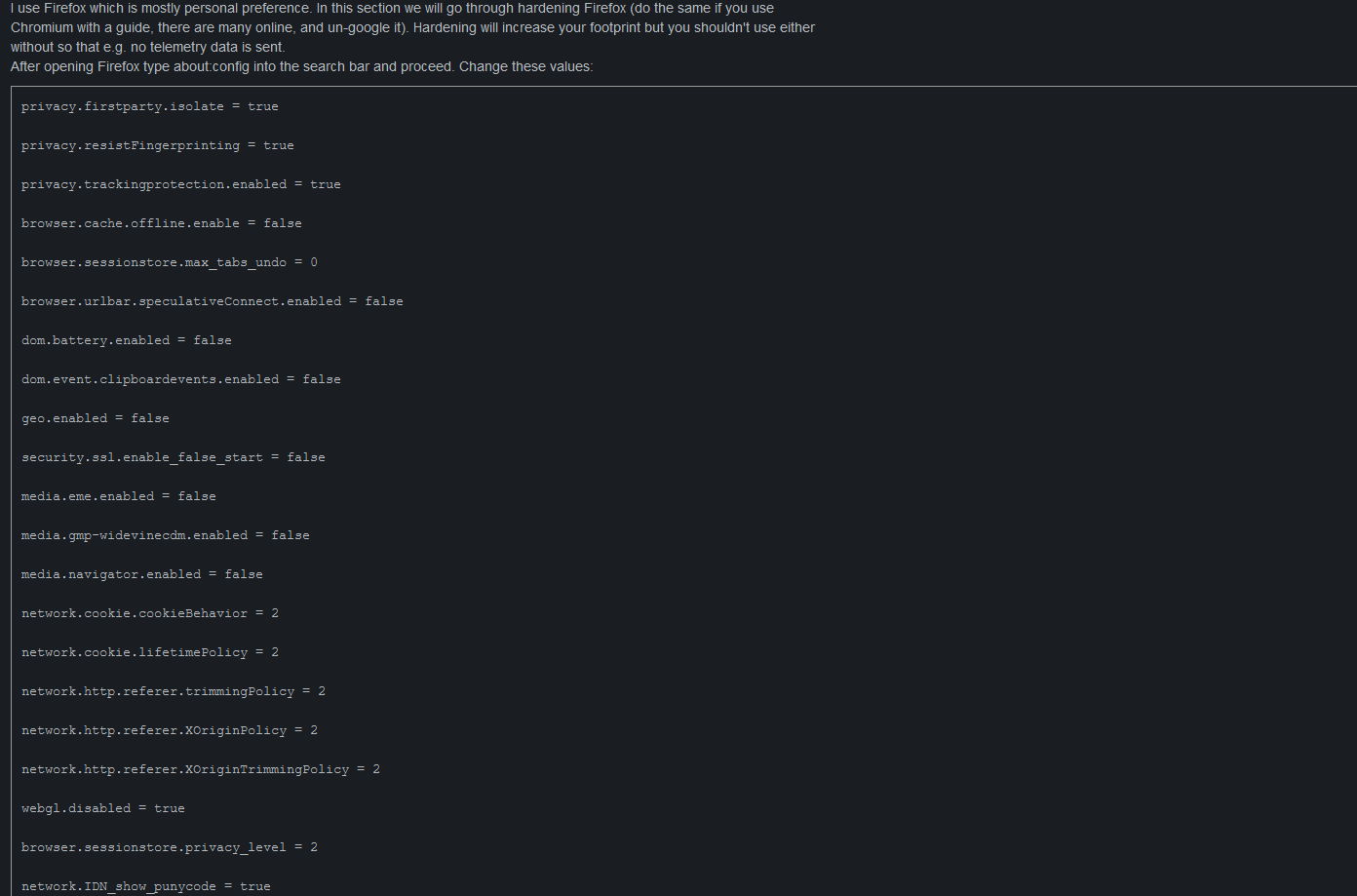
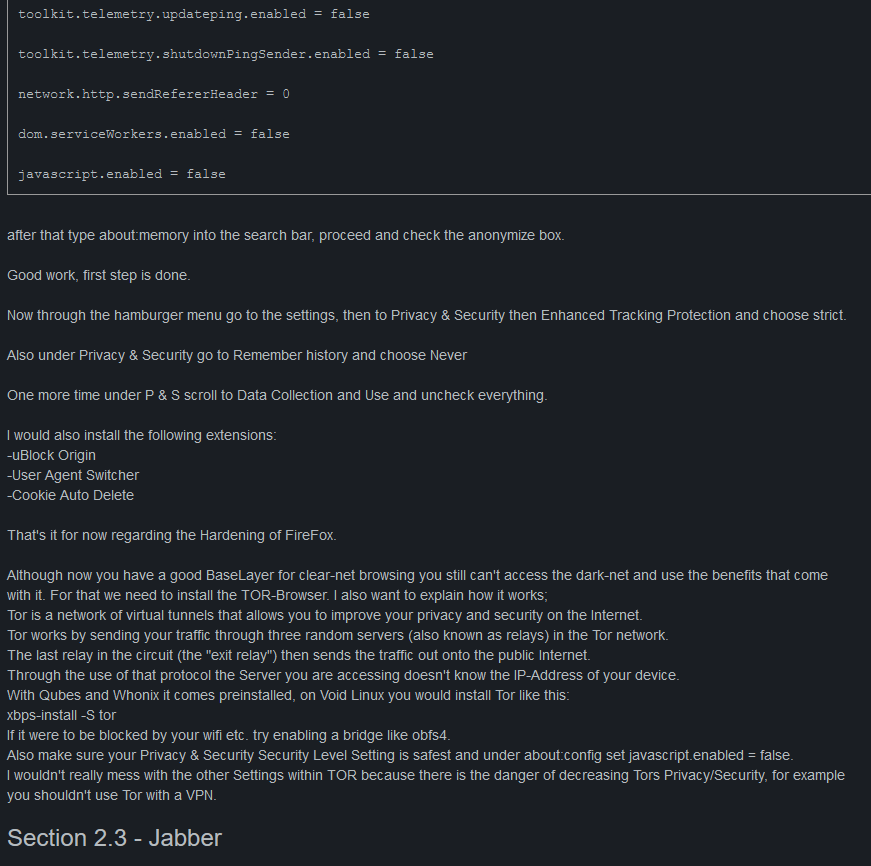
After opening Firefox type about:config into the search bar and proceed. Change these values:
privacy.firstparty.isolate = true
privacy.resistFingerprinting = true
privacy.trackingprotection.enabled = true
browser.cache.offline.enable = false
browser.sessionstore.max_tabs_undo = 0
browser.urlbar.speculativeConnect.enabled = false
dom.battery.enabled = false
dom.event.clipboardevents.enabled = false
geo.enabled = false
security.ssl.enable_false_start = false
media.eme.enabled = false
media.gmp-widevinecdm.enabled = false
media.navigator.enabled = false
network.cookie.cookieBehavior = 2
network.cookie.lifetimePolicy = 2
network.http.referer.trimmingPolicy = 2
network.http.referer.XOriginPolicy = 2
network.http.referer.XOriginTrimmingPolicy = 2
webgl.disabled = true
browser.sessionstore.privacy_level = 2
network.IDN_show_punycode = true
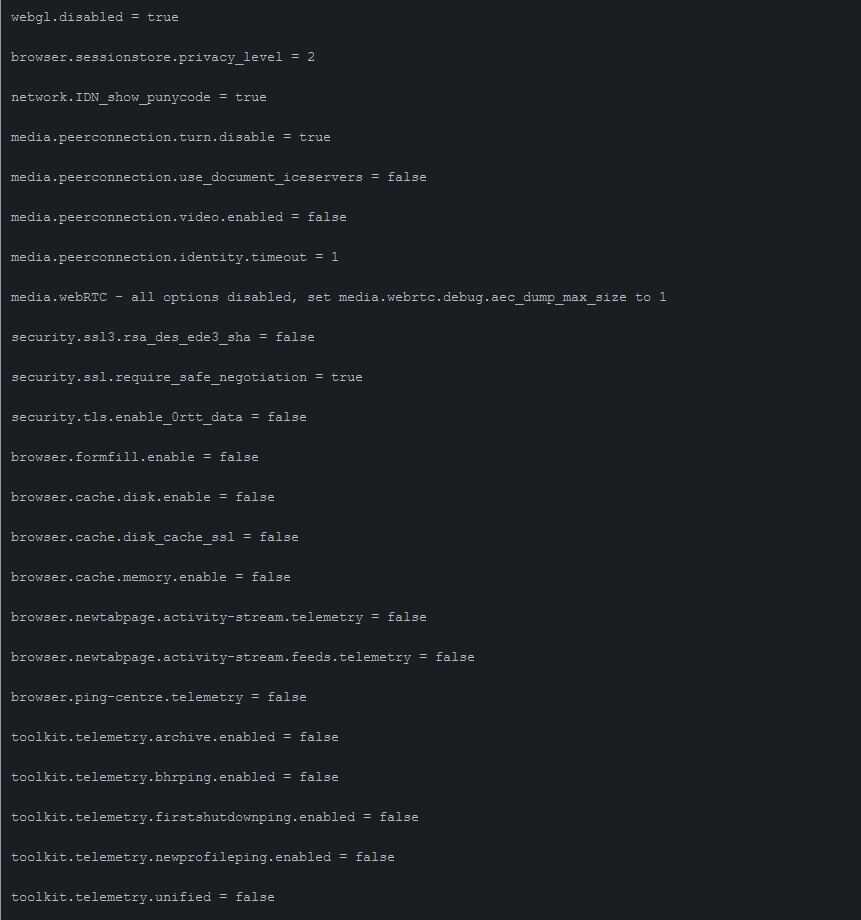
media.peerconnection.turn.disable = true
media.peerconnection.use_document_iceservers = false
media.peerconnection.video.enabled = false
media.peerconnection.identity.timeout = 1
media.webRTC - all options disabled, set media.webrtc.debug.aec_dump_max_size to 1
security.ssl3.rsa_des_ede3_sha = false
security.ssl.require_safe_negotiation = true
security.tls.enable_0rtt_data = false
browser.formfill.enable = false
browser.cache.disk.enable = false
browser.cache.disk_cache_ssl = false
browser.cache.memory.enable = false
browser.newtabpage.activity-stream.telemetry = false
browser.newtabpage.activity-stream.feeds.telemetry = false
browser.ping-centre.telemetry = false
toolkit.telemetry.archive.enabled = false
toolkit.telemetry.bhrping.enabled = false
toolkit.telemetry.firstshutdownping.enabled = false
toolkit.telemetry.newprofileping.enabled = false
toolkit.telemetry.unified = false
toolkit.telemetry.updateping.enabled = false
toolkit.telemetry.shutdownPingSender.enabled = false
network.http.sendRefererHeader = 0
dom.serviceWorkers.enabled = false
javascript.enabled = falseafter that type about:memory into the search bar, proceed and check the anonymize box.
Good work, first step is done.
Now through the hamburger menu go to the settings, then to Privacy & Security then Enhanced Tracking Protection and choose strict.
Also under Privacy & Security go to Remember history and choose Never
One more time under P & S scroll to Data Collection and Use and uncheck everything.
I would also install the following extensions:
-uBlock Origin
-User Agent Switcher
-Cookie Auto Delete
That's it for now regarding the Hardening of FireFox.
Although now you have a good BaseLayer for clear-net browsing you still can't access the dark-net and use the benefits that come
with it. For that we need to install the TOR-Browser. I also want to explain how it works;
Tor is a network of virtual tunnels that allows you to improve your privacy and security on the Internet.
Tor works by sending your traffic through three random servers (also known as relays) in the Tor network.
The last relay in the circuit (the "exit relay") then sends the traffic out onto the public Internet.
Through the use of that protocol the Server you are accessing doesn't know the IP-Address of your device.
With Qubes and Whonix it comes preinstalled, on Void Linux you would install Tor like this:
xbps-install -S tor
If it were to be blocked by your wifi etc. try enabling a bridge like obfs4.
Also make sure your Privacy & Security Security Level Setting is safest and under about:config set javascript.enabled = false.
I wouldn't really mess with the other Settings within TOR because there is the danger of decreasing Tors Privacy/Security, for example
you shouldn't use Tor with a VPN.
Section 2.3 - Jabber
Jabber is an instant-messaging service which runs on the so called XMPP-protocol. Anyone using an XMPP-client can communicate with
another person using an XMPP-client, as long as some measurements are met.
The Client we will use is called pidgin. In addition it is recommended to
make use of the OTR-Plugin (Off the Record), read more about it here: otr.cypherpunks.ca
To install pidgin with OTR run:
sudo apt install pidgin pidgin-otr
Then open pidgin and click "Tools" then "Plugins" then search for "Off-the-Record" and enable it.
To chat you also need to use a server, I use the one Calyx Institute provides. Read about it here:
https://calyxinstitute.org/projects/digital-services/xmpp
Again setting up an Account with Pidgin is rather self-explanatory and you can't really mess up.
Many Vendors and other DW-Users have their contact info displaid in their profile, through that you can contact them.
8BF2qMuVi19Mri8pvp8QJdRufDMFWWac9XAjD9fMaz8bg6AHjJmnPczGNqTMLHhZzbZKbmmDGqZKkQgWTBSmwZAgEapPjJB