Direct Link: http://dreadytofatroptsdj6io7l3xptbet6onoyno2yv7jicoxknyazubrad[.]onion/post/5dec54524d886d6963fb
The donation address at the end of the post is NOT mine. It is that of the creator of this guide.
Images from the post are at the bottom!
The post reads as follows:
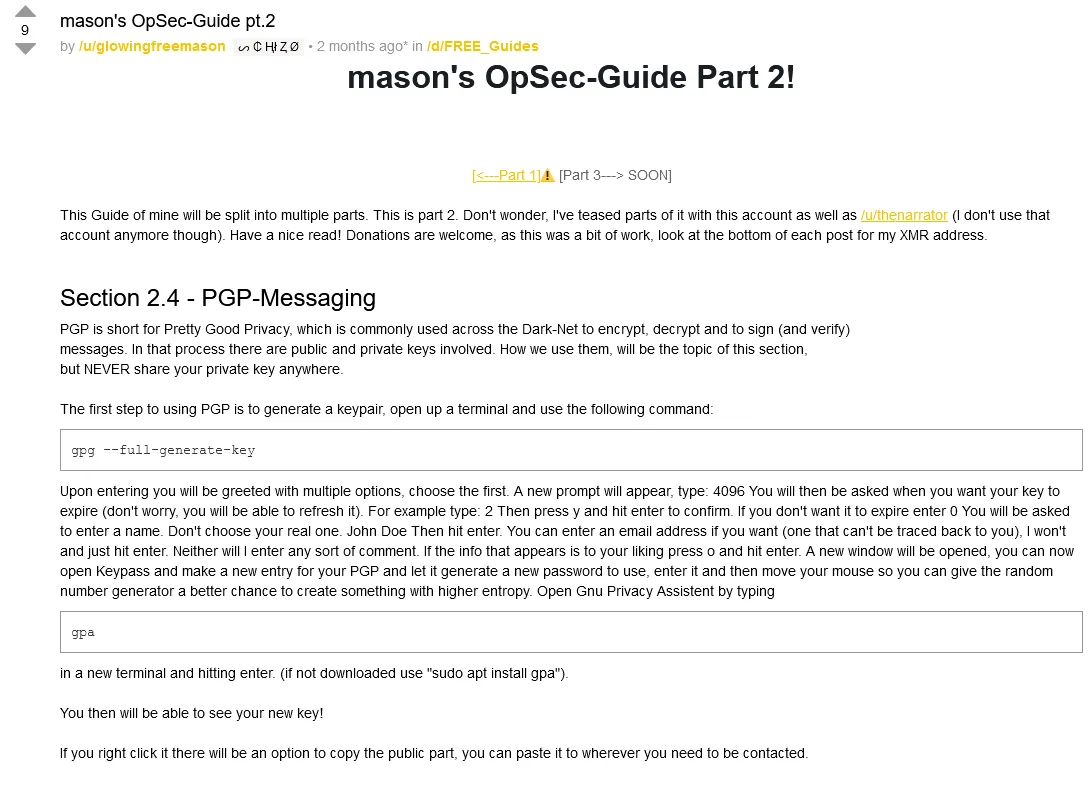
"This Guide of mine will be split into multiple parts. This is part 2. Don't wonder, I've teased parts of it with this account as well as /u/thenarrator (I don't use that account anymore though). Have a nice read! Donations are welcome, as this was a bit of work, look at the bottom of each post for my XMR address.
Section 2.4 - PGP-Messaging
PGP is short for Pretty Good Privacy, which is commonly used across the Dark-Net to encrypt, decrypt and to sign (and verify)
messages. In that process there are public and private keys involved. How we use them, will be the topic of this section,
but NEVER share your private key anywhere.
The first step to using PGP is to generate a keypair, open up a terminal and use the following command:
gpg --full-generate-key
Upon entering you will be greeted with multiple options, choose the first. A new prompt will appear, type: 4096 You will then be asked when you want your key to expire (don't worry, you will be able to refresh it). For example type: 2 Then press y and hit enter to confirm. If you don't want it to expire enter 0 You will be asked to enter a name. Don't choose your real one. John Doe Then hit enter. You can enter an email address if you want (one that can't be traced back to you), I won't and just hit enter. Neither will I enter any sort of comment. If the info that appears is to your liking press o and hit enter. A new window will be opened, you can now open Keypass and make a new entry for your PGP and let it generate a new password to use, enter it and then move your mouse so you can give the random number generator a better chance to create something with higher entropy. Open Gnu Privacy Assistent by typing
gpa
in a new terminal and hitting enter. (if not downloaded use "sudo apt install gpa").
You then will be able to see your new key!
If you right click it there will be an option to copy the public part, you can paste it to wherever you need to be contacted.
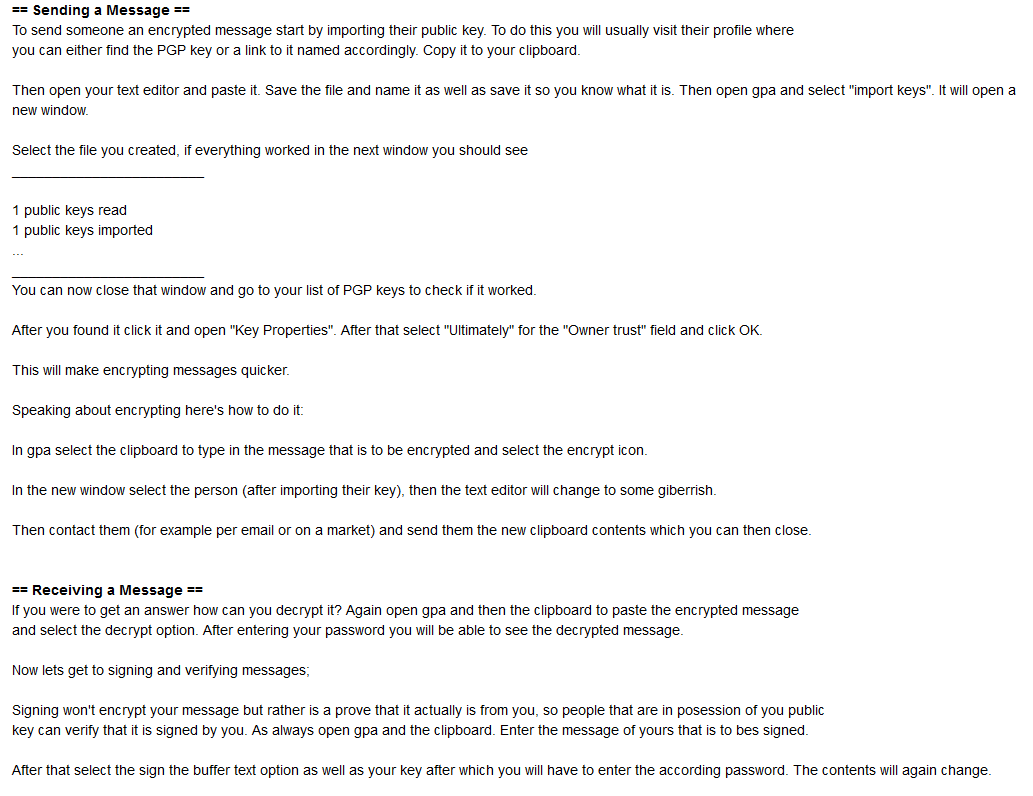
== Sending a Message ==
To send someone an encrypted message start by importing their public key. To do this you will usually visit their profile where
you can either find the PGP key or a link to it named accordingly. Copy it to your clipboard.
Then open your text editor and paste it. Save the file and name it as well as save it so you know what it is. Then open gpa and select "import keys". It will open a new window.
Select the file you created, if everything worked in the next window you should see
1 public keys read
1 public keys imported
...
You can now close that window and go to your list of PGP keys to check if it worked.
After you found it click it and open "Key Properties". After that select "Ultimately" for the "Owner trust" field and click OK.
This will make encrypting messages quicker.
Speaking about encrypting here's how to do it:
In gpa select the clipboard to type in the message that is to be encrypted and select the encrypt icon.
In the new window select the person (after importing their key), then the text editor will change to some giberrish.
Then contact them (for example per email or on a market) and send them the new clipboard contents which you can then close.
== Receiving a Message ==
If you were to get an answer how can you decrypt it? Again open gpa and then the clipboard to paste the encrypted message
and select the decrypt option. After entering your password you will be able to see the decrypted message.
Now lets get to signing and verifying messages;
Signing won't encrypt your message but rather is a prove that it actually is from you, so people that are in posession of you public
key can verify that it is signed by you. As always open gpa and the clipboard. Enter the message of yours that is to bes signed.
After that select the sign the buffer text option as well as your key after which you will have to enter the according password. The contents will again change.
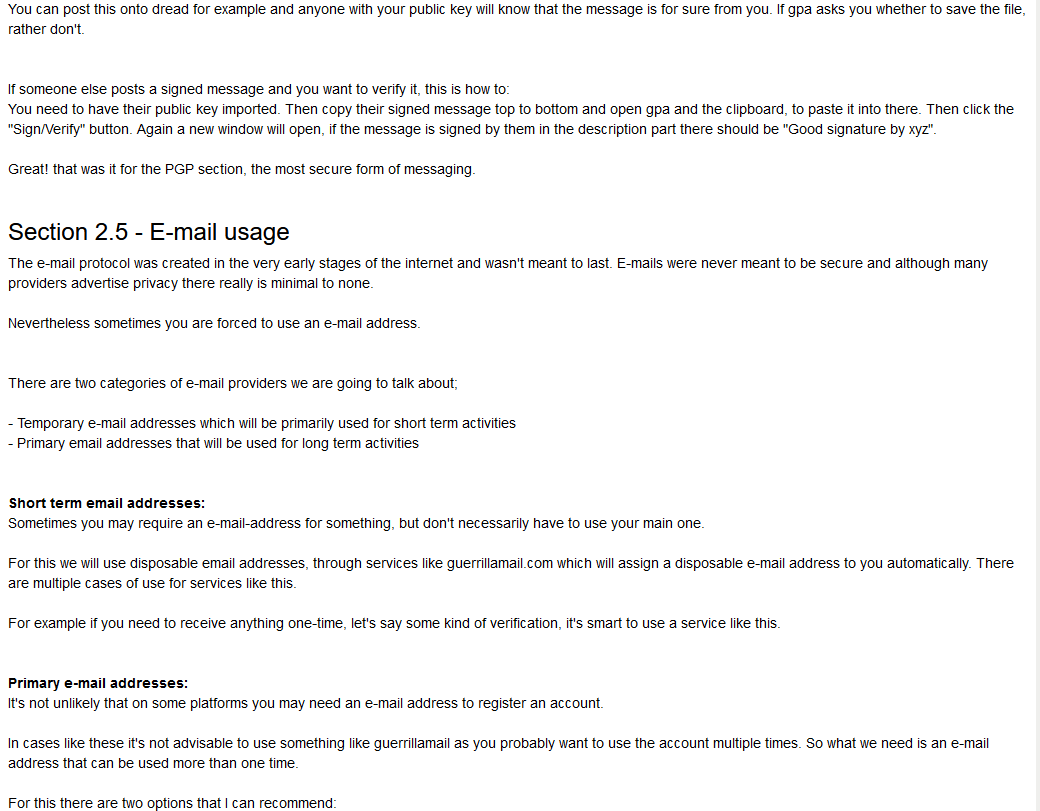
You can post this onto dread for example and anyone with your public key will know that the message is for sure from you. If gpa asks you whether to save the file, rather don't.
If someone else posts a signed message and you want to verify it, this is how to:
You need to have their public key imported. Then copy their signed message top to bottom and open gpa and the clipboard, to paste it into there. Then click the "Sign/Verify" button. Again a new window will open, if the message is signed by them in the description part there should be "Good signature by xyz".
Great! that was it for the PGP section, the most secure form of messaging.
Section 2.5 - E-mail usage
The e-mail protocol was created in the very early stages of the internet and wasn't meant to last. E-mails were never meant to be secure and although many providers advertise privacy there really is minimal to none.
Nevertheless sometimes you are forced to use an e-mail address.
There are two categories of e-mail providers we are going to talk about;
- Temporary e-mail addresses which will be primarily used for short term activities
- Primary email addresses that will be used for long term activities
Short term email addresses:
Sometimes you may require an e-mail-address for something, but don't necessarily have to use your main one.
For this we will use disposable email addresses, through services like guerrillamail.com which will assign a disposable e-mail address to you automatically. There are multiple cases of use for services like this.
For example if you need to receive anything one-time, let's say some kind of verification, it's smart to use a service like this.
Primary e-mail addresses:
It's not unlikely that on some platforms you may need an e-mail address to register an account.
In cases like these it's not advisable to use something like guerrillamail as you probably want to use the account multiple times. So what we need is an e-mail address that can be used more than one time.
For this there are two options that I can recommend:
Tutanota and SecTor
I trust no email provider and wouldn't send any important info with these services without PGP encryption.
It's sort of serves more as a last resort. Even if these providers were leak-free and even when law-enforcement were to request info and they couldn't tell them decrypted contents, your e-mail security still depends upon who you chat with. Let's say you are using a Tutanota account and it's as secure as they say but the individual you are chatting with were to use Gmail, then all correspondence with that person can be considered compromised.
Note:
For now I would try to avoid Proton as there have been some indicators, that it is possible they are a big honeypot.
Still like we said, sometimes you will need to use an e-mail address you can access multiple times. I just want you to know that I wouldn't lay much trust in all of those "super private and secure" e-mail providers and still PGP encrypt anything of importance.
Moreover I recommend you to follow some kind of e-mail strategy similar to this:
E-mail address 1: Marketplace xyz
E-mail address 2: Forum zyx
E-mail address 3: Throwaway if disposable providers were to get flagged
E-mail address 4: PGP correspondence with person D
E-mail address 5: PGP correspondence with person U
Basically try to diversify your e-mail usage as much as possible so if one account were to be compromised, Law Enforcement Agencies would have much less info than if you would manage everything from one account.
I think it's obvious to not use any info related to you for usernames/credentials etc. It's not stupid to use something like 32463278974@e-mail.com. Although procedures like these are far from time efficient it's much better if each process takes ten seconds more rather than being caught and spending some years behind bars.
If I have helped you in any way, or if you'd like to see more in-depth newbie friendly tutorials on important subjects in our community, any XMR contribution you can spare would be appreciated :)
8BF2qMuVi19Mri8pvp8QJdRufDMFWWac9XAjD9fMaz8bg6AHjJmnPczGNqTMLHhZzbZKbmmDGqZKkQgWTBSmwZAgEapPjJB"