Linktree Allegedly Scraped, Exposing 19.6 Million User Profiles with Linked Social Media Accounts
🧩 Standalone API Access Now Available
Access high-volume threat-intelligence data, automated ingestion endpoints, ransomware feeds, IOC data, and more.
View API AccessUnlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
Quick Facts
Incident Overview
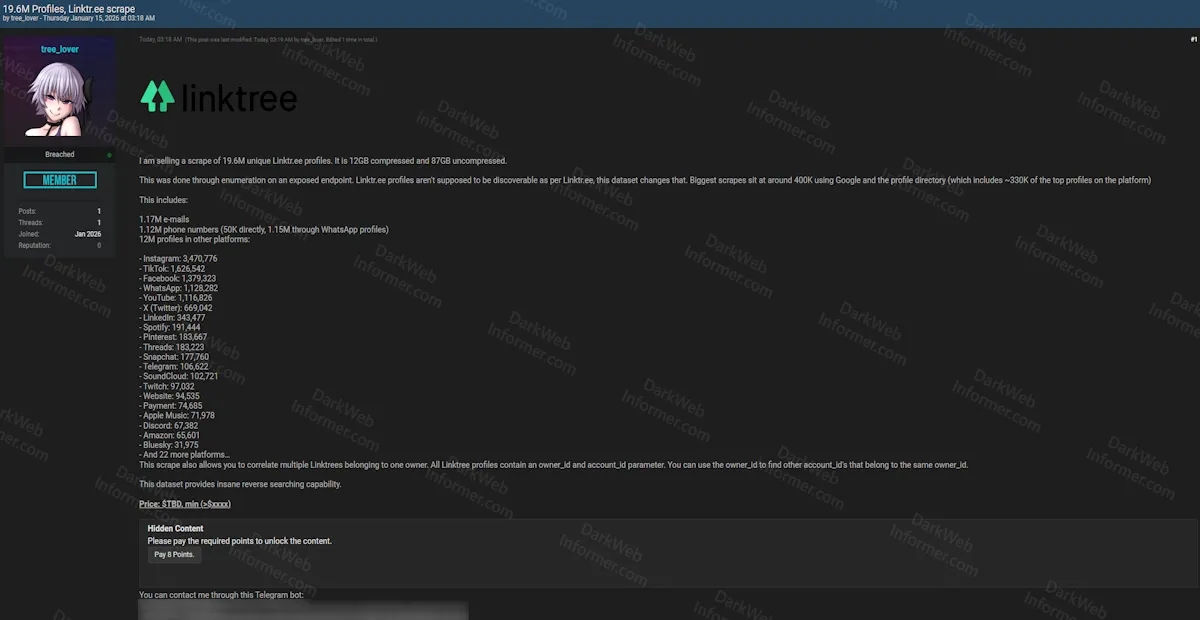
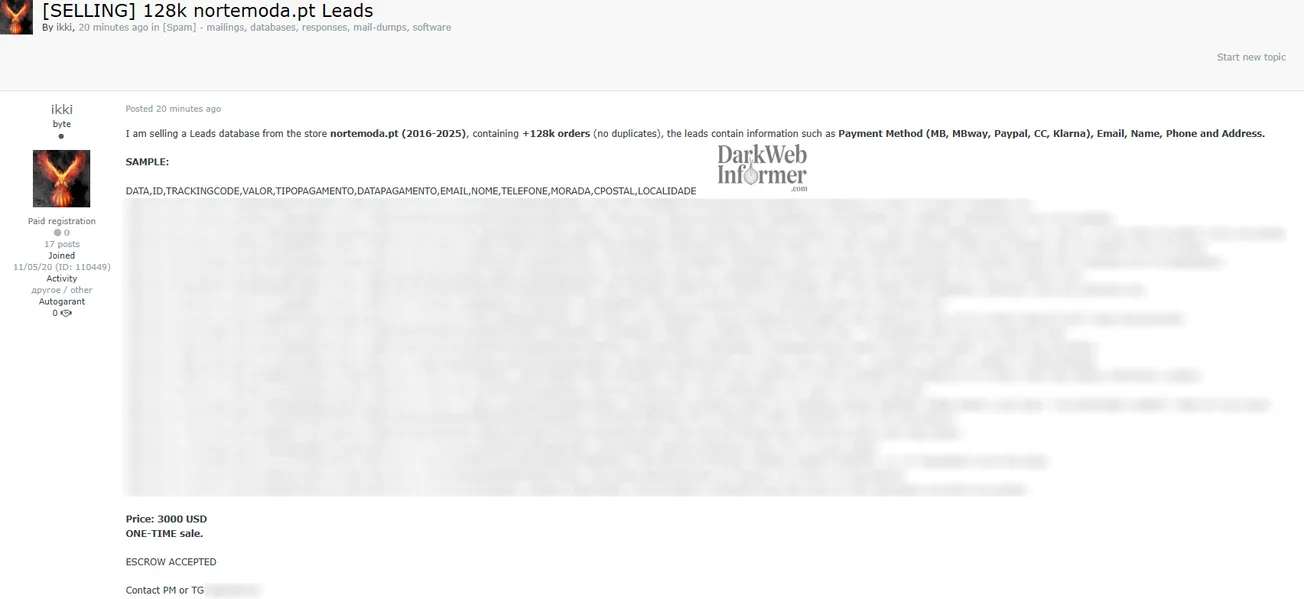
A threat actor operating under the handle "tree_lover" claims to be selling a scrape of 19.6 million unique Linktree (linktr.ee) profiles. According to the post, the dataset is 12GB compressed and 87GB uncompressed. The threat actor states this was achieved through enumeration on an exposed endpoint, noting that Linktree profiles are not supposed to be discoverable. The actor claims the biggest scrapes using Google and the profile directory sit at around 400K, with this dataset including approximately 330K of the top profiles on the platform.
The claimed data includes 1.17 million email addresses, 1.12 million phone numbers (50K directly, 1.15 million through WhatsApp profiles), and 12 million profiles linked to other platforms. The breakdown of linked social media profiles allegedly includes: Instagram (3,470,776), TikTok (1,626,542), Facebook (1,379,323), WhatsApp (1,128,282), YouTube (1,116,826), X/Twitter (669,042), LinkedIn (343,477), Spotify (191,444), Pinterest (183,667), Threads (183,223), Snapchat (177,760), Telegram (106,622), SoundCloud (102,721), Twitch (97,032), Website (94,535), Payment (74,685), Apple Music (71,978), Discord (67,382), Amazon (65,601), Bluesky (31,975), and 22 additional platforms.
The threat actor notes that all Linktree profiles contain an owner_id and account_id parameter, allowing correlation of multiple Linktrees belonging to one owner. The price is listed as TBD with a minimum of over $xxxx. Contact is offered through Telegram and Session.
This post is for subscribers on the Plus, Pro and Elite tiers
SubscribeAlready have an account? Sign In