Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
API Access for Researchers & Security Teams
SOC teams, researchers, and security professionals can integrate Dark Web Informer's threat intelligence directly into their workflows via API. Access real-time breach data, threat feeds, and monitoring capabilities programmatically.
Learn About API AccessDisclaimer
This breach alert includes material that may contain personally identifiable information (PII) gathered strictly from publicly available sources. All information is provided solely for cybersecurity awareness and threat intelligence purposes.
French Government Ministry Breach Exposes Internal Systems and Department Data
Quick Facts
Incident Overview
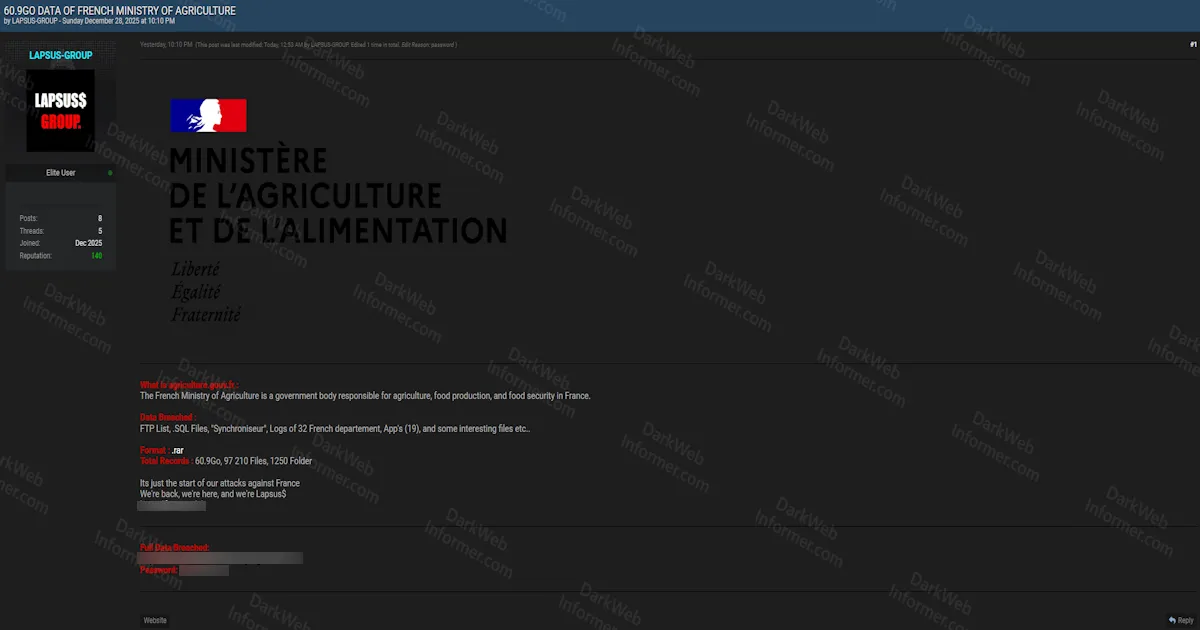
A threat group operating under the name "LAPSUS$ GROUP" has published what they claim is approximately 60.9GB of data stolen from France's Ministry of Agriculture and Food Sovereignty. The leak was posted to BreachForums on December 29, 2025, with the threat actors stating this is "just the start of our attacks against France."
The ministry, which oversees agriculture policy, food production, and food security across France, appears to have suffered a significant compromise of its internal systems. According to the breach post, the leaked archive contains a mix of FTP server credentials, SQL databases, application logs, and files spanning 32 French departments. The threat actors have made the data available through a direct IP address download protected by a password.
What makes this incident particularly concerning is the breadth of the compromise. The leaked data package reportedly contains 97,210 files organized across 1,250 folders, suggesting extensive access to the ministry's infrastructure. The threat actors specifically highlight several categories of compromised data in their post, painting a picture of deep system penetration rather than a surface-level breach.