📌 Quick Facts
🔗 DarkWebInformer.com - Cyber Threat Intelligence
📅 Date: 2025-03-05 15:46:14
🚨 Title: Alleged Sale of a Zero-Day TP-Link RCE Exploit
🛡️ Victim Country: Not Specified
🏭 Victim Industry: Not Specified
🏢 Victim Organization: Not Specified
🌐 Victim Site: Not Specified
📜 Category: Vulnerability
🔗 Claim: https://breachforums.st/Thread-SELLING-JumboJet-TP-Link-RCE-Exploit-0-Day-Private-0-day
🕵️♂️ Threat Actor: JumboJet
🌍 Network: OpenWeb
📝 What Happened?
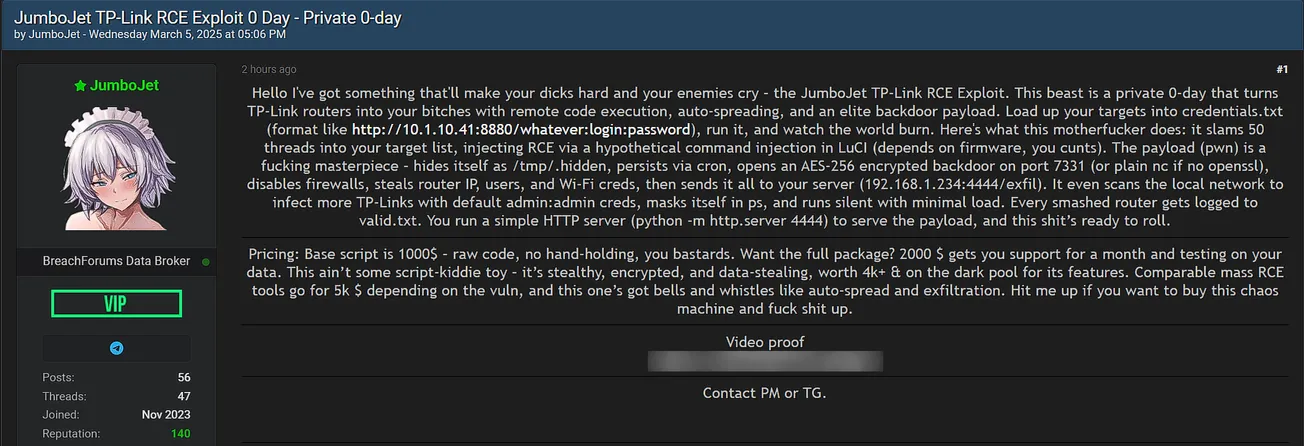
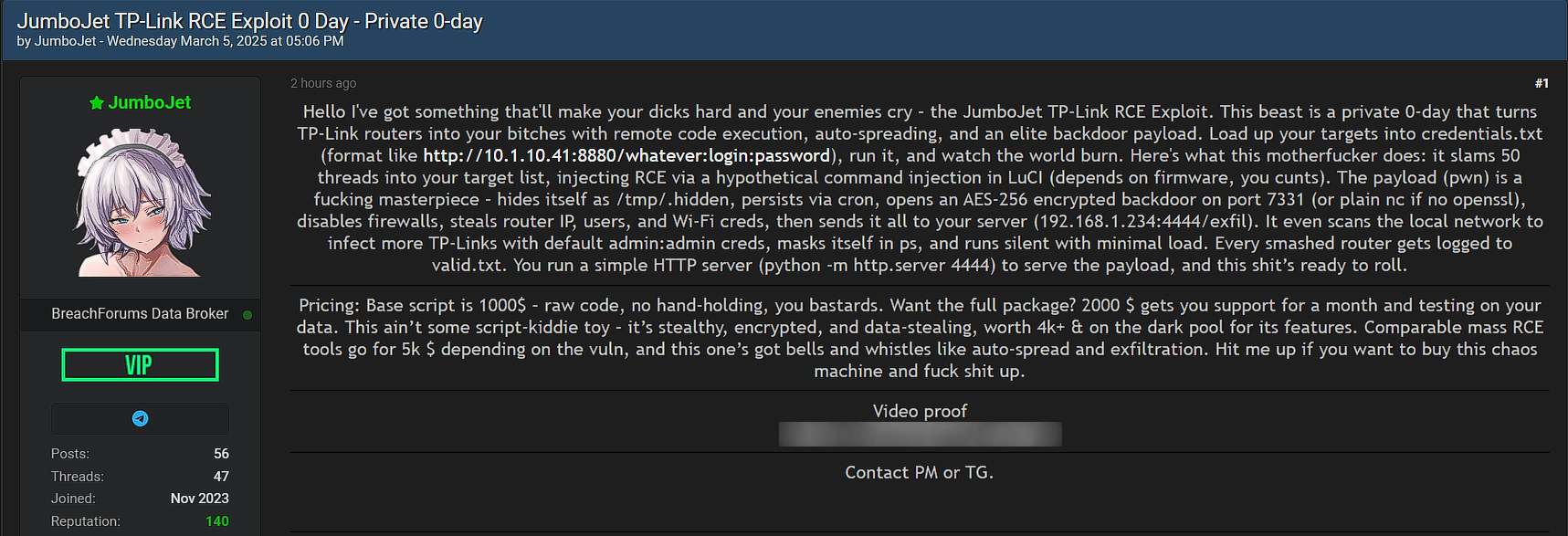
A threat actor identified as JumboJet has advertised the sale of a zero-day remote code execution (RCE) exploit targeting TP-Link routers.
Exploit Capabilities:
- Remote Code Execution (RCE): Injects arbitrary commands via a vulnerability in the LuCI web interface (depends on firmware).
- Stealth Persistence: The payload hides itself as a hidden file (
/tmp/.hidden) and persists via cron jobs. - Network Scanning & Propagation:
- Scans local networks for additional TP-Link routers.
- Uses default admin credentials (
admin:admin) to infect more devices.
- Firewall & Credential Theft:
- Disables firewalls, steals router IPs, extracts user credentials & Wi-Fi passwords.
- Sends stolen data to an attacker's server for further exploitation.
- Automated Deployment & Exploitation: Runs an AES-256 encrypted backdoor on port 7331 (or plain netcat if OpenSSL is unavailable).
Pricing Details:
- Base Script: $1,000 (raw code, no support).
- Full Package: $2,000, includes one month of support and testing on buyer's infrastructure.
- Dark Web Value Estimate: Comparable exploits sell for $4,000+ in underground markets.
The exploit allows unauthorized control over vulnerable TP-Link routers, enabling botnet creation, espionage, and large-scale network intrusions.
📊 Compromised Access Details
- Zero-day exploit for TP-Link routers enabling full device compromise
- Potential for large-scale botnet deployment and network infiltration
- Stealthy persistence and credential harvesting capabilities
🛡 WhiteIntel.io Data Leak Information
(No victim site disclosed)
⚠ Implications
- Widespread Router Exploitation & Network Compromise – Attackers could hijack TP-Link devices globally.
- Cybercrime & APT Activities – The exploit may be weaponized for state-sponsored espionage, botnet deployment, or ransomware attacks.
- Consumer & Enterprise Risk – Unpatched TP-Link routers in home and corporate environments are vulnerable to remote takeover.
🔧 Recommended Actions
- Patch TP-Link Firmware & Apply Security Updates – If an official fix is released, update immediately.
- Disable Remote Management on Routers – Prevent attackers from exploiting remote admin access.
- Monitor for Unauthorized Access & Unusual Network Traffic – Detect rogue connections & backdoor activity.
- Change Default Credentials & Enable MFA – Use strong, unique passwords for network devices.
⚠ Stay vigilant. Follow DarkWebInformer.com for real-time updates on cyber threats.