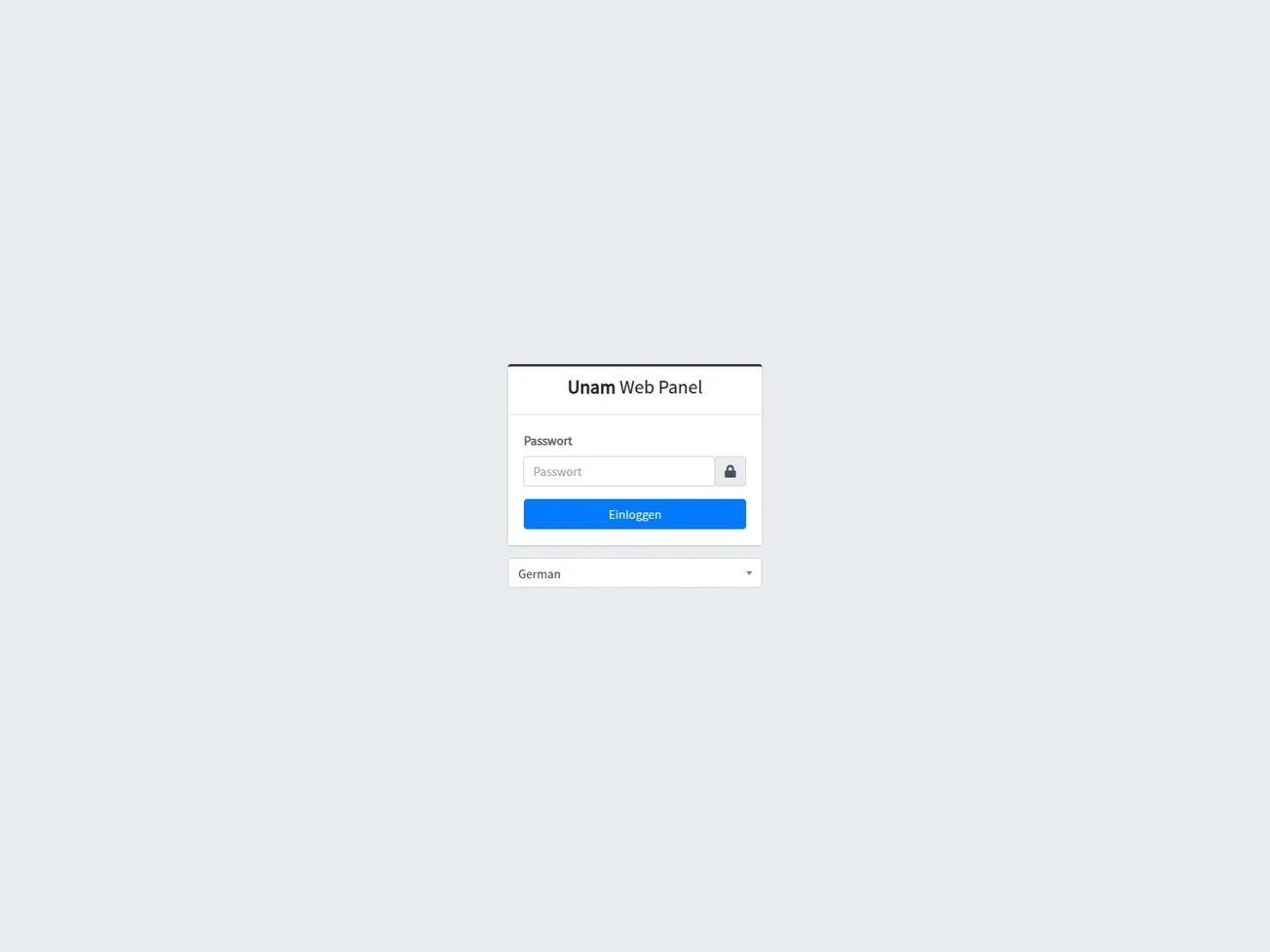
📖 Overview
A domain-based indicator has been identified hosting a Unam Web Panel login interface, commonly leveraged for botnet and malware C2 operations. The infrastructure is hosted by Namecheap (AS22612) and is associated with remote administration and credential theft activity. Confidence is assessed at 100%.
📌 Key Details
| Field | Information |
|---|---|
| Type | Domain |
| Indicator | outsystem[.]online |
| Threat Type | Botnet C2 |
| Malware | unknown |
| Confidence | 100% |
| Date | 21 Sep 2025 – 16:01:21 UTC |
| Tags | AS22612, C2, Censys, NAMECHEAP-NET, Panel, UNAM |
| Reporter | DonPasci |
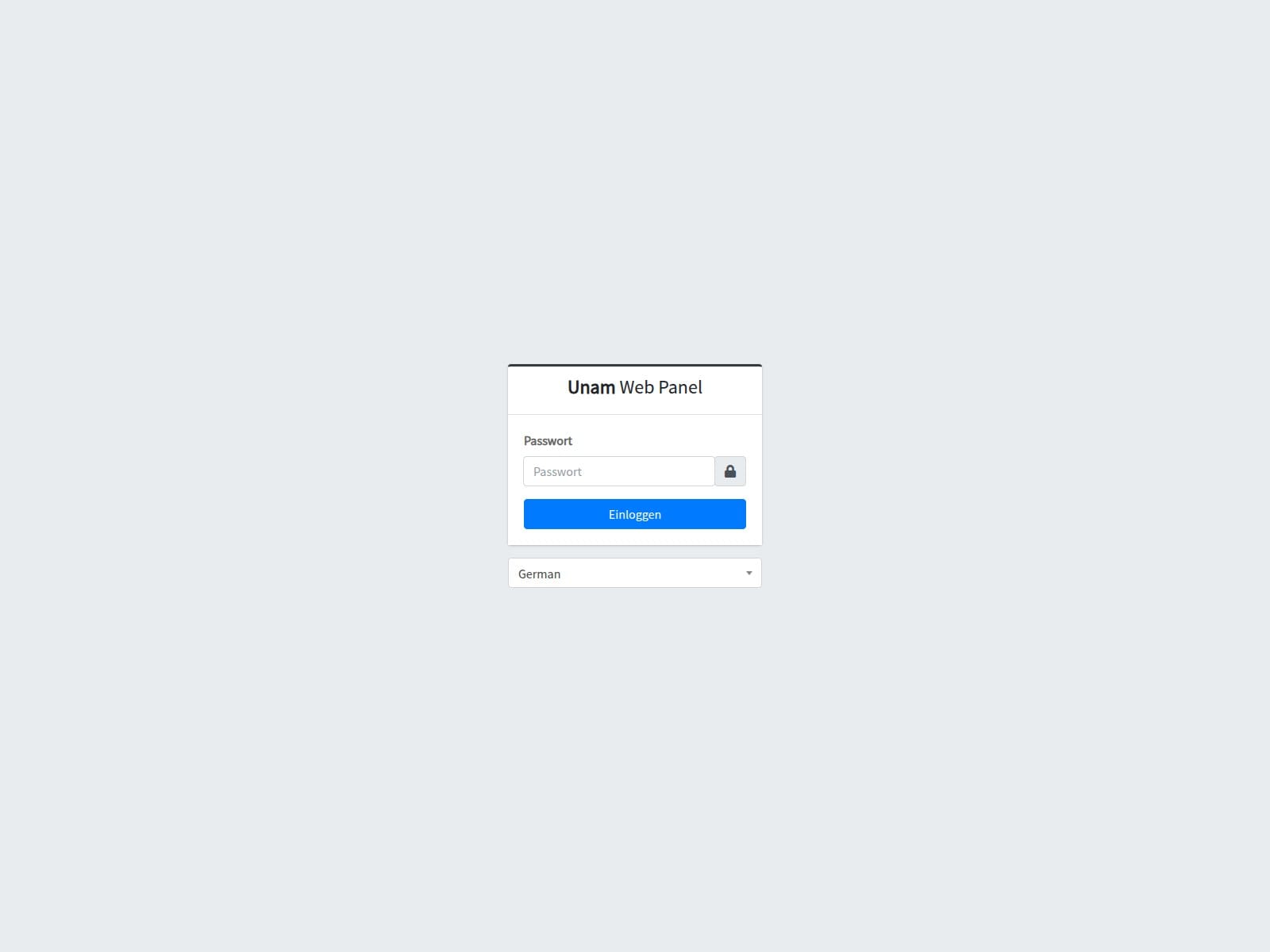
🔎 URLScan Result
Page Title: Unam Web Panel — Einloggen
Screenshot: https://urlscan.io/screenshots/019952fd-aba8-76cc-a8f6-a7321b2687e6.png
Result: https://urlscan.io/result/019952fd-aba8-76cc-a8f6-a7321b2687e6/
📡 Related Intelligence
WHOIS Record: https://who.is/whois/outsystem.online
VirusTotal Report: https://www.virustotal.com/gui/domain/outsystem.online
Reference: https://search.censys.io/hosts/198.54.115.227+outsystem.online
🛡️ Defensive Guidance
- Block
outsystem[.]onlineat DNS, proxy, and endpoint levels. - Monitor for HTTP traffic attempting to authenticate to Unam Web Panel paths.
- Hunt for related botnet artifacts and potential credential theft telemetry.
- Engage with Namecheap abuse channels for takedown coordination.
⚠️ The exposure of a Unam Web Panel instance strongly suggests active botnet management infrastructure. Immediate blocking and monitoring is recommended.