📖 Overview
An IOC has been flagged involving the abuse of the official Telegram Bot API as a command-and-control (C2) channel for the XWorm malware family. This method leverages Telegram infrastructure to evade detection by blending malicious traffic with legitimate encrypted communications. Confidence is assessed at 50%.
📌 Key Details
| Field | Information |
|---|---|
| Type | URL |
| Indicator | https://api.telegram[.]org/bot8284662503:AAFdH0goSDb-2xyZTOSjhrxMajwjW4nCkfU |
| Threat Type | Botnet C2 |
| Malware | win.xworm |
| Confidence | 50% |
| Date | 02 Oct 2025 – 20:35:50 UTC |
| Tags | None |
| Reporter | j3rich0123 |
| Reference | None |
🔎 URLScan Result
- Verdict Score: 0
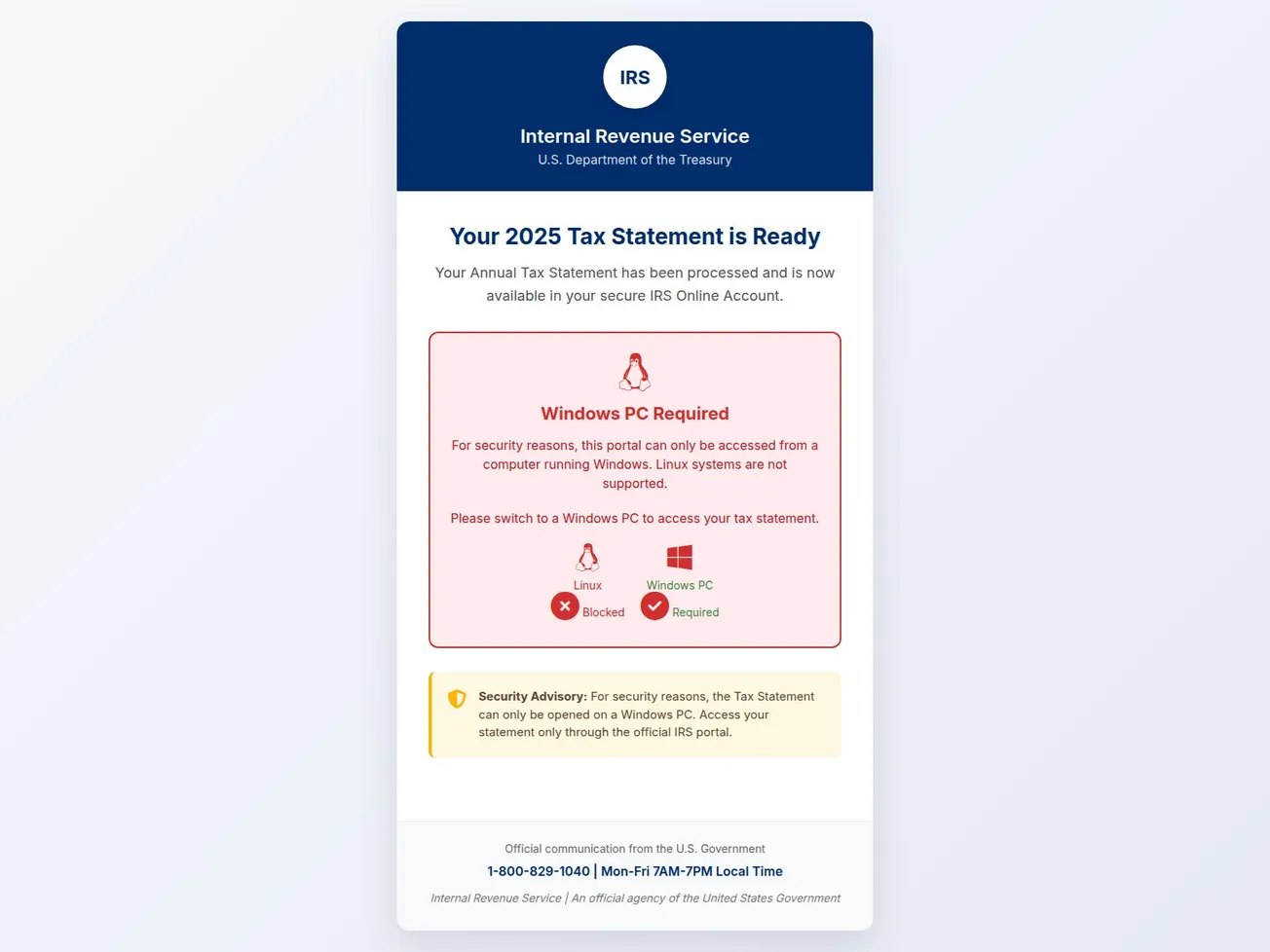
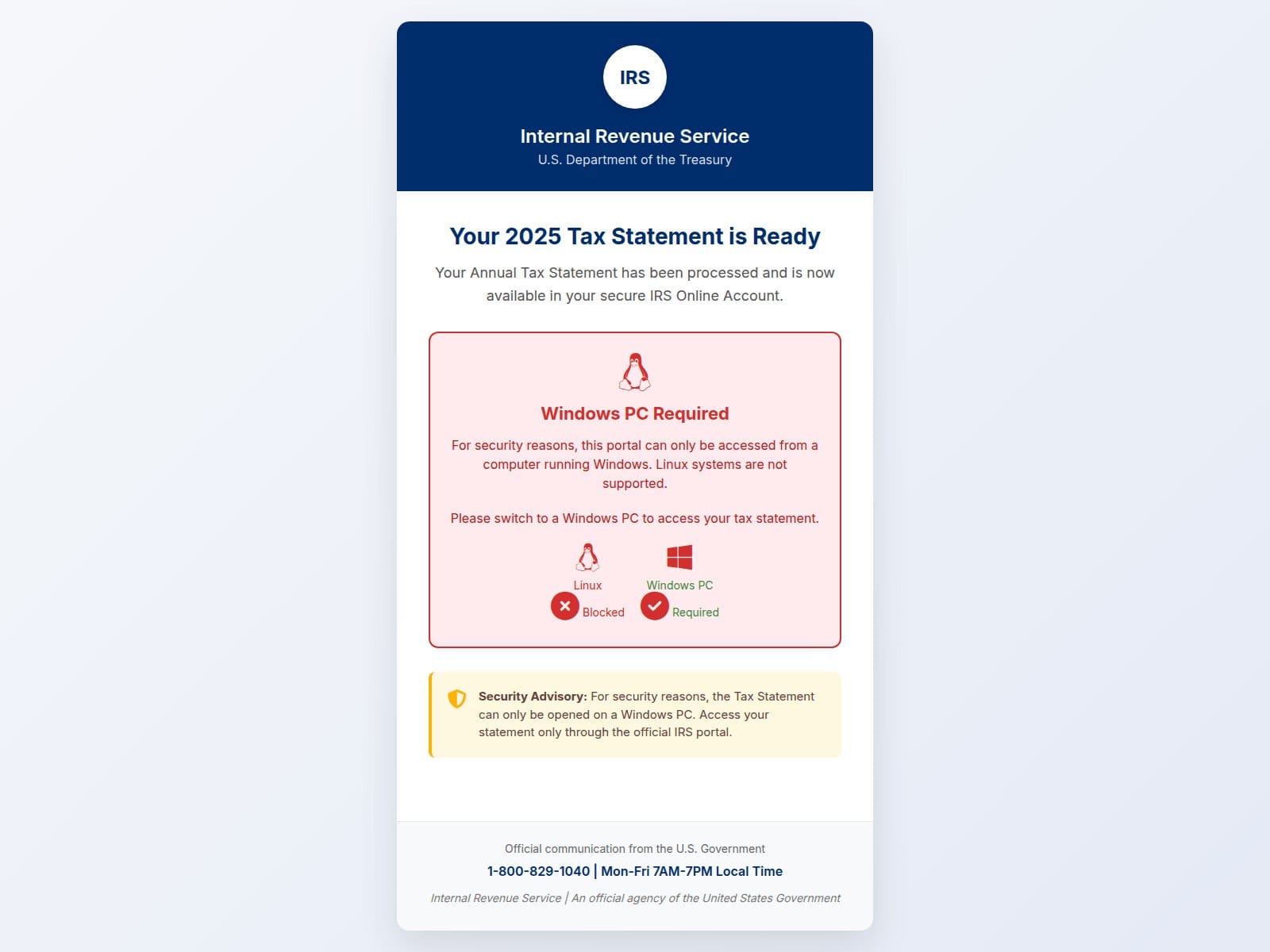
- Page Title: IRS Tax Statement Portal
- Screenshot: View Screenshot
- Result: Full Scan Report
📡 Related Intelligence
- VirusTotal Report: VirusTotal URL Report
🛡️ Defensive Guidance
- Block and alert on unusual connections to Telegram Bot API endpoints originating from enterprise endpoints.
- Monitor for processes invoking https://api.telegram.org/bot* URLs, which may indicate malware beaconing.
- Incorporate YARA or SIEM detection rules targeting XWorm-specific artifacts (persistence mechanisms, registry keys, mutexes).
- Consider layered detection by correlating traffic volume, process lineage, and behavioral patterns involving Telegram communication.
⚠️ This IOC highlights the increasing trend of malware abusing legitimate cloud and messaging APIs (such as Telegram) to hide C2 traffic within otherwise trusted services.