📖 Overview
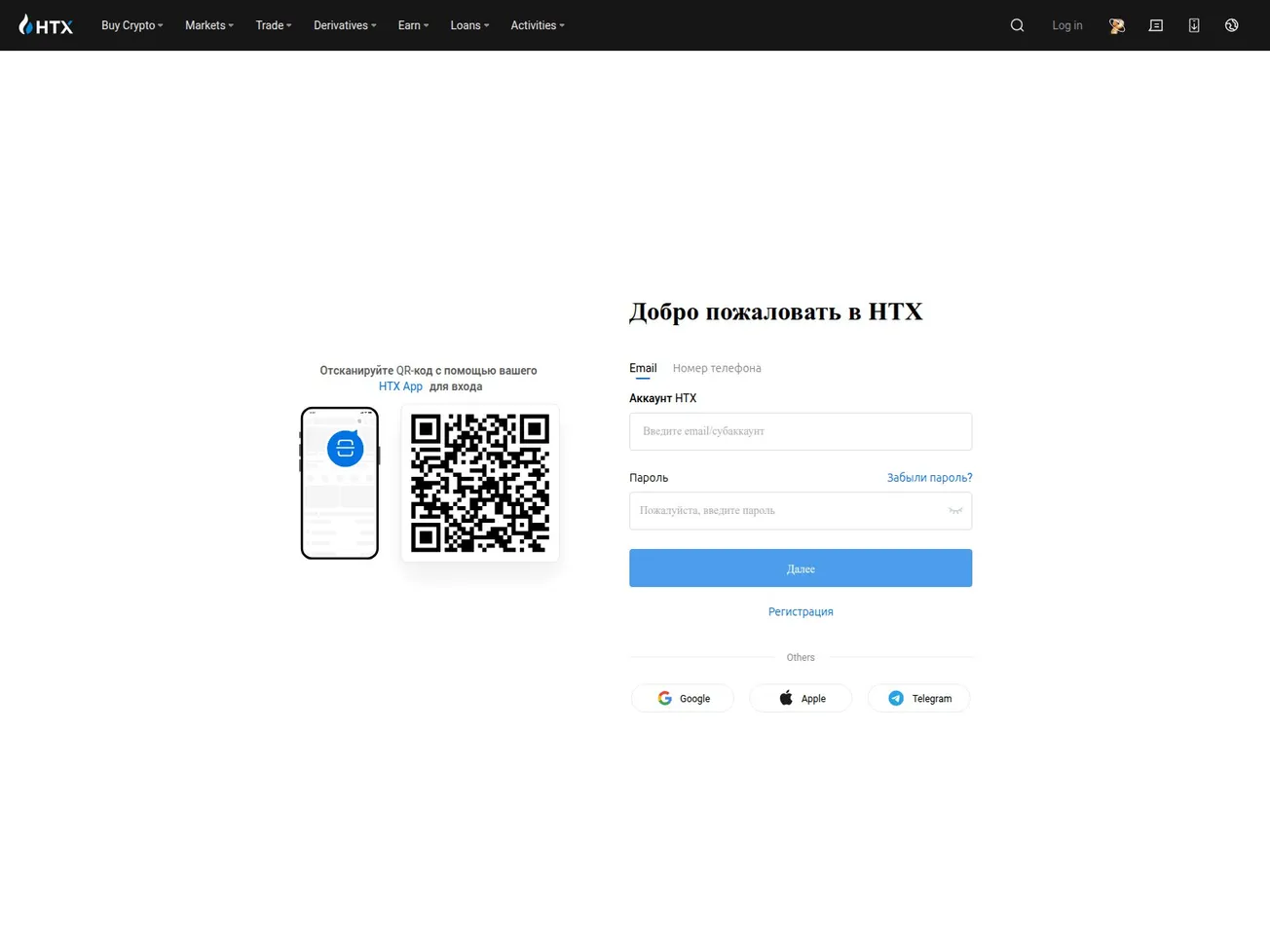
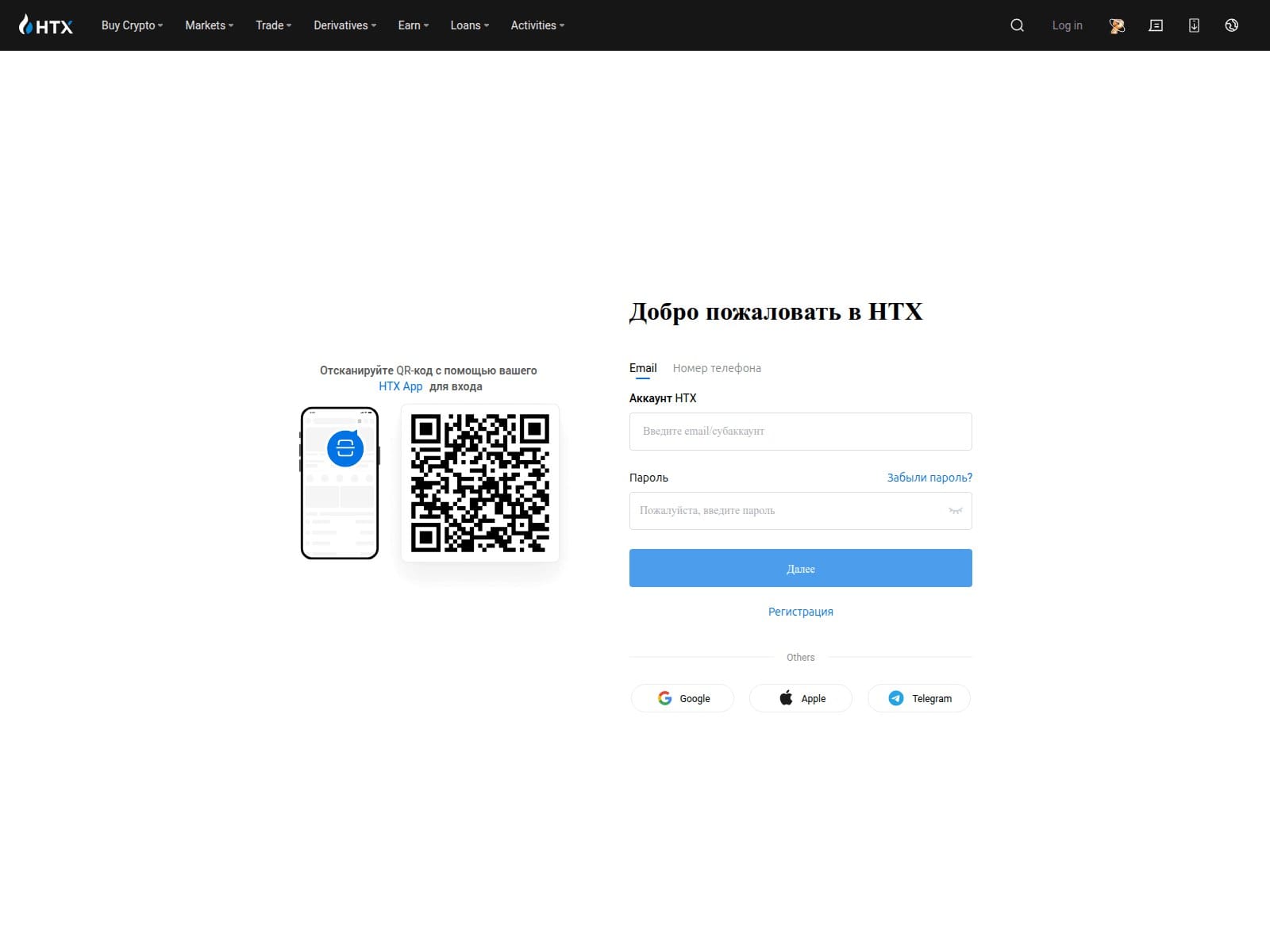
A phishing-style domain mimicking the HTX cryptocurrency exchange login page has been identified. While presenting itself as a legitimate portal, the infrastructure may serve dual purposes, phishing credential harvesting and potential command-and-control (C2) activity. Confidence is assessed at 75%.
📌 Key Details
| Field | Information |
|---|---|
| Type | Domain |
| Indicator | htx-user[.]at |
| Threat Type | Botnet C2 |
| Malware | Unknown |
| Confidence | 75% |
| Date | 06 Oct 2025 – 16:41:32 UTC |
| Tags | domain |
| Reporter | anonymous |
| Reference | None |
🔎 URLScan Result
- Verdict Score: 0
- Page Title: HTX Вход — Авторизация аккаунта | HTX Login & Sign In
- Screenshot: View Screenshot
- Result: Full Scan Report
📡 Domain & Certificate Info
- DNS A Record: 95[.]129[.]234[.]137
- Recent Certificates:
- C=US, O=Let's Encrypt, CN=R12 (Valid: 2025-09-20 → 2025-12-19)
- C=US, O=Let's Encrypt, CN=R12 (Valid: 2025-09-20 → 2025-12-19)
- C=US, O=Let's Encrypt, CN=R13 (Valid: 2025-09-15 → 2025-12-14)
📡 Related Intelligence
- Certificate Transparency: crt.sh Report
- VirusTotal Report: VirusTotal Domain Report
- URLScan Domain Overview: urlscan.io Domain Page
- DNS Analytics: dnslytics.com Report
🛡️ Defensive Guidance
- Block htx-user[.]at and its associated IP (95[.]129[.]234[.]137) at DNS, proxy, and endpoint layers.
- Watch for outbound traffic patterns or login attempts to lookalike cryptocurrency domains.
- Hunt for credentials exfiltrated to suspicious domains masquerading as crypto exchange portals.
- Track certificate transparency logs to detect and pre-emptively block newly registered HTX-themed lookalike domains.
⚠️ This IOC highlights the continued abuse of cryptocurrency branding by threat actors who stage fake login portals to capture credentials or operate C2 channels under the guise of legitimate services.