📖 Overview
A domain-based indicator has been identified that mimics the DODOEX decentralized exchange interface. The infrastructure is associated with potential botnet command-and-control (C2) operations, using a convincing crypto-trading front. Confidence is assessed at 100%.
📌 Key Details
| Field | Information |
|---|---|
| Type | Domain |
| Indicator | app.dodloxex[.]com |
| Threat Type | Botnet C2 |
| Malware | Unknown |
| Confidence | 100% |
| Date | 28 Sep 2025 – 16:15:37 UTC |
| Tags | c2 |
| Reporter | Pamparam |
| Reference | None |
🔎 URLScan Result
- Verdict Score: 0
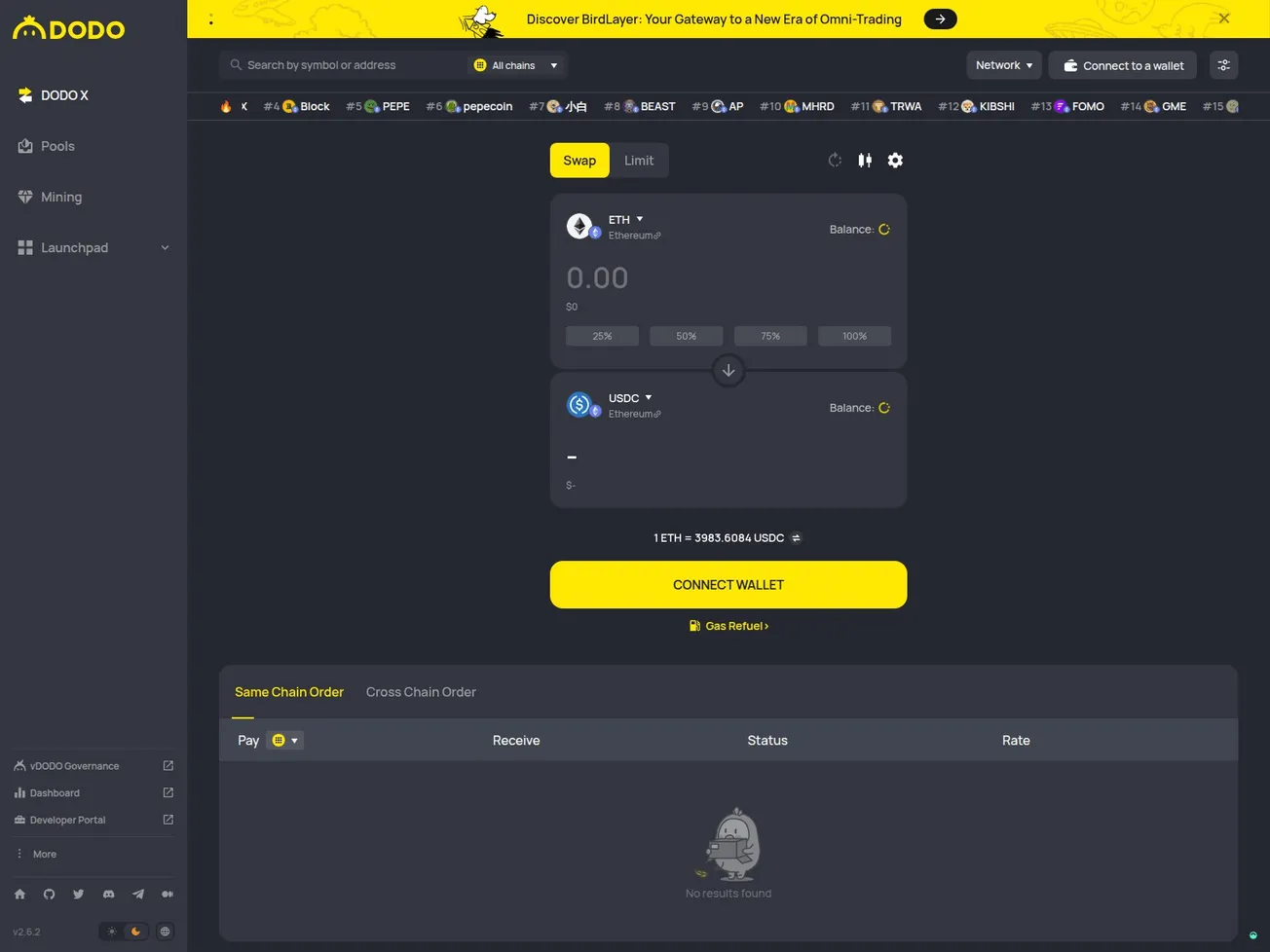
- Page Title: Swap 1-ETH to 1-USDC at 3,983.6084 with DODOEX
- Screenshot: View Screenshot
- Result: Full Scan Report
📡 Domain & Certificate Info
- DNS A Records: 104[.]21[.]11[.]130, 172[.]67[.]149[.]60
- DNS AAAA Records: 2606:4700:3034::6815:b82, 2606:4700:3030::ac43:953c
- Recent Certificates:
- C=US, O=Let's Encrypt, CN=R13 (Valid: 2025-08-27 → 2025-11-25)
- C=US, O=Let's Encrypt, CN=R13 (Valid: 2025-08-27 → 2025-11-25)
📡 Related Intelligence
- Certificate Transparency: crt.sh Report
- VirusTotal Report: VirusTotal Domain Report
- URLScan Domain Overview: urlscan.io Domain Page
- DNS Analytics: dnslytics.com Report
🛡️ Defensive Guidance
- Block app.dodloxex[.]com and its associated IP addresses at DNS, proxy, and endpoint levels.
- Watch for outbound traffic attempting to beacon or interact with DODOEX-themed fake domains.
- Alert on user activity involving suspicious crypto swap interfaces outside known trusted exchanges.
- Track certificate transparency logs for additional domains impersonating cryptocurrency services.
⚠️ This IOC highlights the use of crypto-exchange lookalike pages as camouflage for malicious C2 infrastructure. Such setups are often used to lure victims into interacting with a familiar interface while backend traffic is leveraged for command-and-control purposes.