📖 Overview
An IP-based indicator has been identified hosting a Supershell v2.0.0 panel, a remote access and botnet management framework. The panel is exposed over HTTP on a non-standard port, suggesting use for C2 operations. This infrastructure is hosted within DigitalOcean (AS14061). Confidence is assessed at 100%.
📌 Key Details
| Field | Information |
|---|---|
| Type | URL |
| Indicator | 178[.]128[.]219[.]58:8888/supershell/login/ |
| Threat Type | Botnet C2 |
| Malware | unknown |
| Confidence | 100% |
| Date | 14 Sep 2025 – 10:00:03 UTC |
| Tags | AS14061, DigitalOcean LLC, Supershell |
| Reporter | antiphishorg |
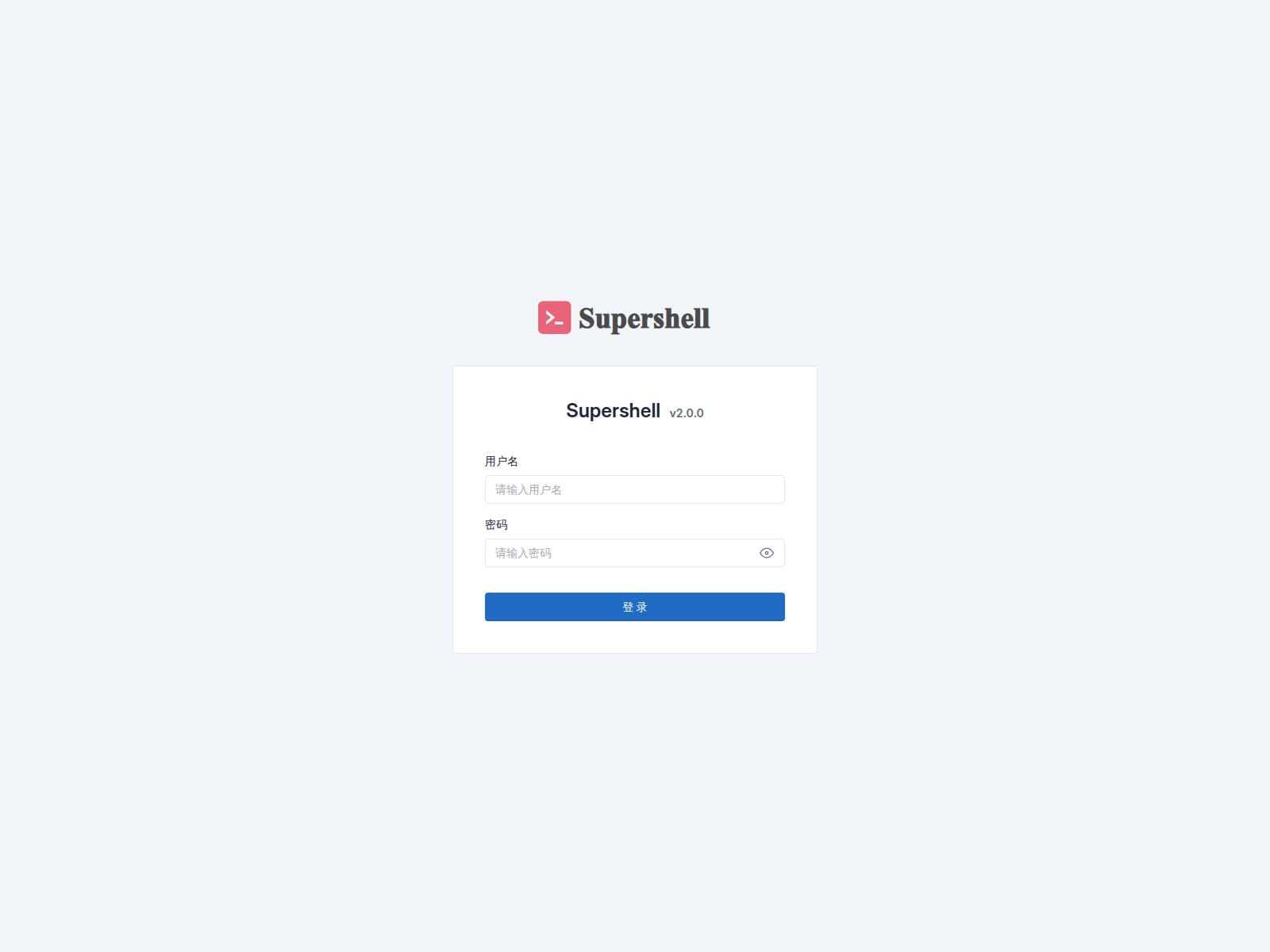
🔎 URLScan Result
Page Title: Supershell – 登录
Screenshot: https://urlscan.io/screenshots/019947a6-67c2-707e-a40f-4909a4057050.png
Result: https://urlscan.io/result/019947a6-67c2-707e-a40f-4909a4057050/
📡 Related Intelligence
VirusTotal Report: https://www.virustotal.com/gui/url/fce5543e043e52e70fc816b28948c4f518fbb32979f79066bbaa0a8f5cbf14c4
🛡️ Defensive Guidance
- Block
178[.]128[.]219[.]58:8888at network and endpoint levels. - Monitor for HTTP requests to
/supershell/login/. - Hunt for Supershell artifacts or suspicious reverse shell behavior.
- Engage with hosting provider abuse channels (DigitalOcean LLC) for takedown.
⚠️ The use of Supershell indicates organized C2 management capabilities. Immediate blocking and investigation of related infrastructure is recommended.









