📖 Overview
A command-and-control (C2) endpoint leveraging Ngrok tunneling infrastructure has been identified in association with Quasar RAT operations. The domain 10.tcp.eu.ngrok.io was observed resolving to an AWS-hosted IP address. While the Ngrok tunnel is currently inactive and displays an error page, this infrastructure is often used by threat actors for temporary or disposable C2 endpoints. Confidence is assessed at 100%.
📌 Key Details
| Field | Information |
|---|---|
| Type | Domain |
| Indicator | 10.tcp.eu.ngrok[.]io |
| Threat Type | Botnet C2 |
| Malware | win.quasar_rat |
| Confidence | 100% |
| Date | 28 Oct 2025 – 18:01:15 UTC |
| Tags | c2, domain, quasar, RAT, triage |
| Reporter | DonPasci |
| Reference | Triage Sandbox Report |
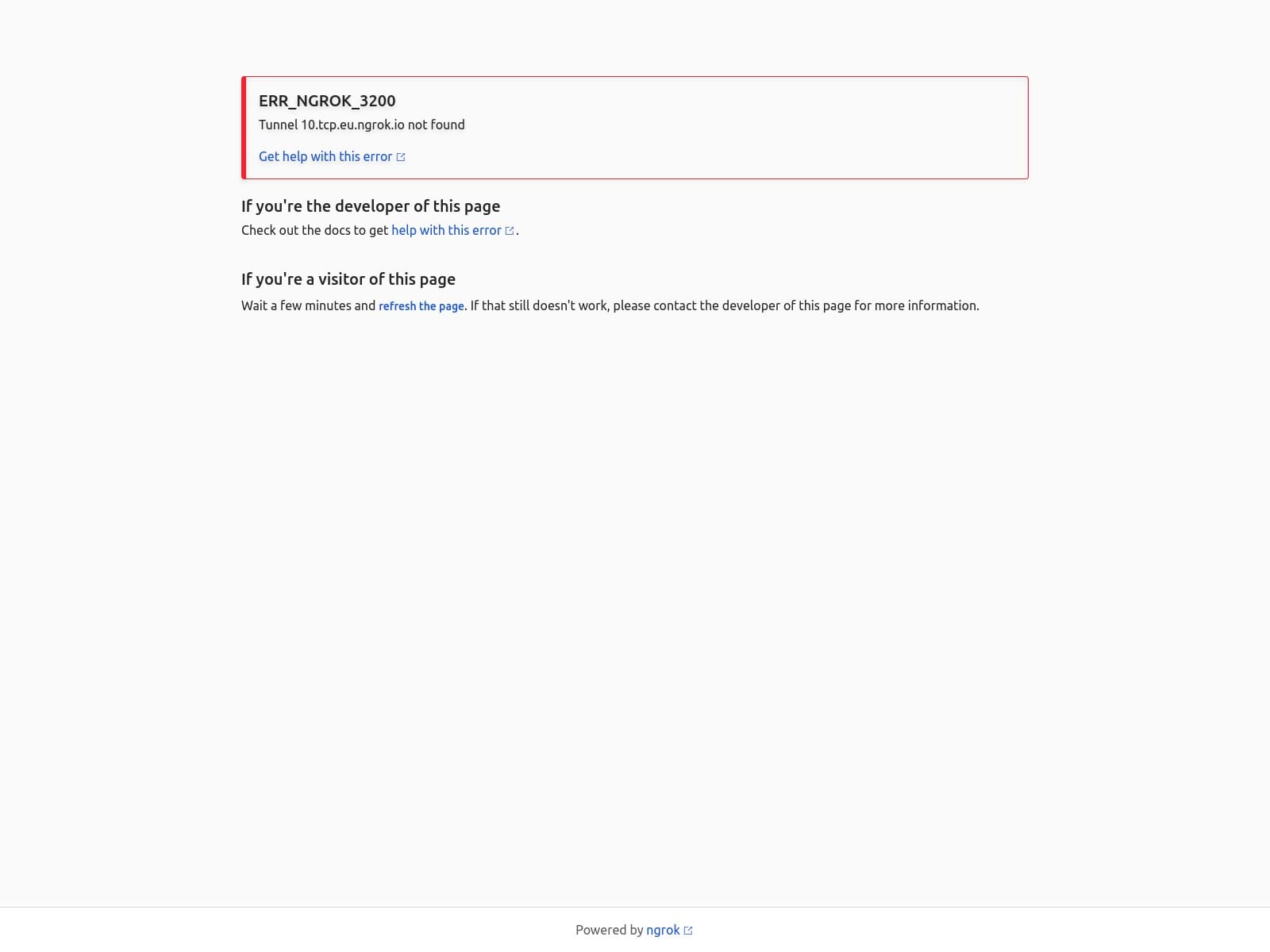
🔎 URLScan Result
- Verdict Score: 0
- Page Title: ERR_NGROK_3200 – Tunnel 10.tcp.eu.ngrok.io not found
- Screenshot: View Screenshot
- Result: Full Scan Report
📡 Domain & Certificate Info
- DNS A Record: 18[.]195[.]122[.]13
📡 Related Intelligence
- Certificate Transparency: crt.sh Report
- VirusTotal Report: VirusTotal Domain Report
- URLScan Domain Overview: urlscan.io Domain Page
- DNS Analytics: dnslytics.com Report
🛡️ Defensive Guidance
- Block 10.tcp.eu.ngrok[.]io and related Ngrok subdomains in perimeter and endpoint security policies.
- Monitor for Quasar RAT indicators, such as outbound TCP connections to Ngrok tunnels or unusual persistence activity (registry edits, WMI subscriptions).
- Detect and block Ngrok tunnels used in non-development environments to prevent misuse for covert remote access.
- Audit outbound connections to AWS IP ranges hosting transient C2 endpoints.
⚠️ This IOC highlights the increasing abuse of Ngrok tunneling services by remote access trojans like Quasar RAT, enabling threat actors to establish short-lived, encrypted C2 channels that easily bypass traditional perimeter defenses.