📖 Overview
A URL-based indicator has been identified tied to NetSupport Manager RAT distribution. The malicious script is hosted on a compromised website belonging to a legitimate nonprofit organization, demonstrating the SmartApeSG campaign’s continued abuse of trusted infrastructure to deliver remote access tools.
📌 Key Details
| Field | Information |
|---|---|
| Type | URL |
| Indicator | aftermaths-attraction[.]com/ajax/pixi.min.js |
| Threat Type | Payload Delivery |
| Malware | win.netsupportmanager_rat |
| Confidence | 100% |
| Date | 10 Sep 2025 – 15:34:52 UTC |
| Tags | SmartApeSG |
| Reporter | monitorsg |
🔎 URLScan Result
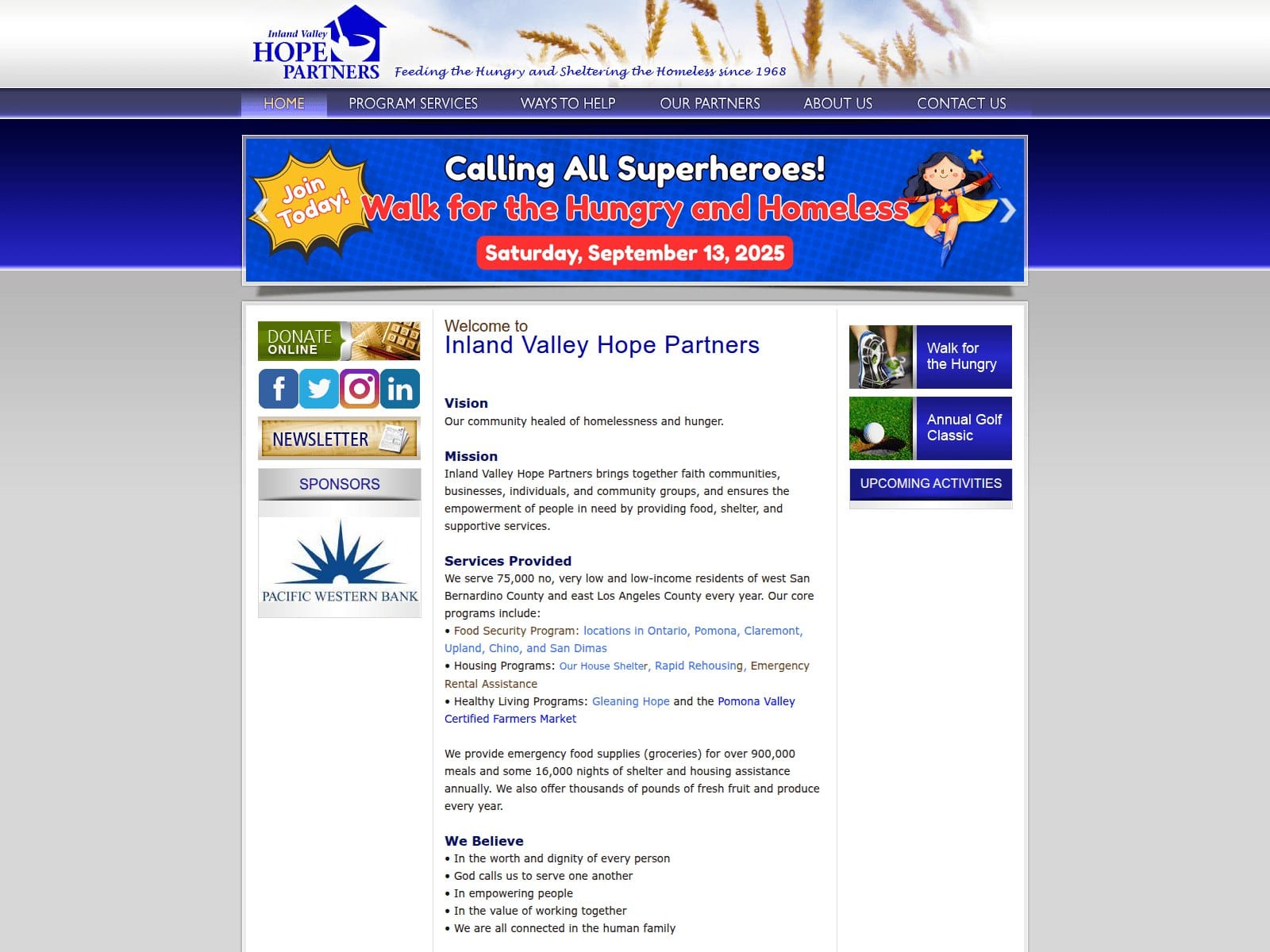
Page Title: Inland Valley Hope Partners
Screenshot: https://urlscan.io/screenshots/0199343b-b344-73eb-a40b-38bfc012958f.png
Result: https://urlscan.io/result/0199343b-b344-73eb-a40b-38bfc012958f/
📡 Related Intelligence
VirusTotal Report: https://www.virustotal.com/gui/url/e0f8548d3da4f0451dbe01fac1b21dba854163145283bfca296cf30e3afcc3a9
Reference: https://infosec.exchange/@monitorsg/115180731792855034
🛡️ Defensive Guidance
- Block
aftermaths-attraction[.]comand its hosted payloads at DNS, proxy, and endpoint layers. - Monitor for unauthorized script loads (
pixi.min.js) from non-standard domains. - Hunt for NetSupport RAT persistence mechanisms across endpoints.
- Review DNS and proxy logs for suspicious requests tied to this campaign.
⚠️ This IOC highlights the compromise of legitimate nonprofit infrastructure to host malicious payloads, increasing the likelihood of successful delivery against unsuspecting targets.









