📖 Overview
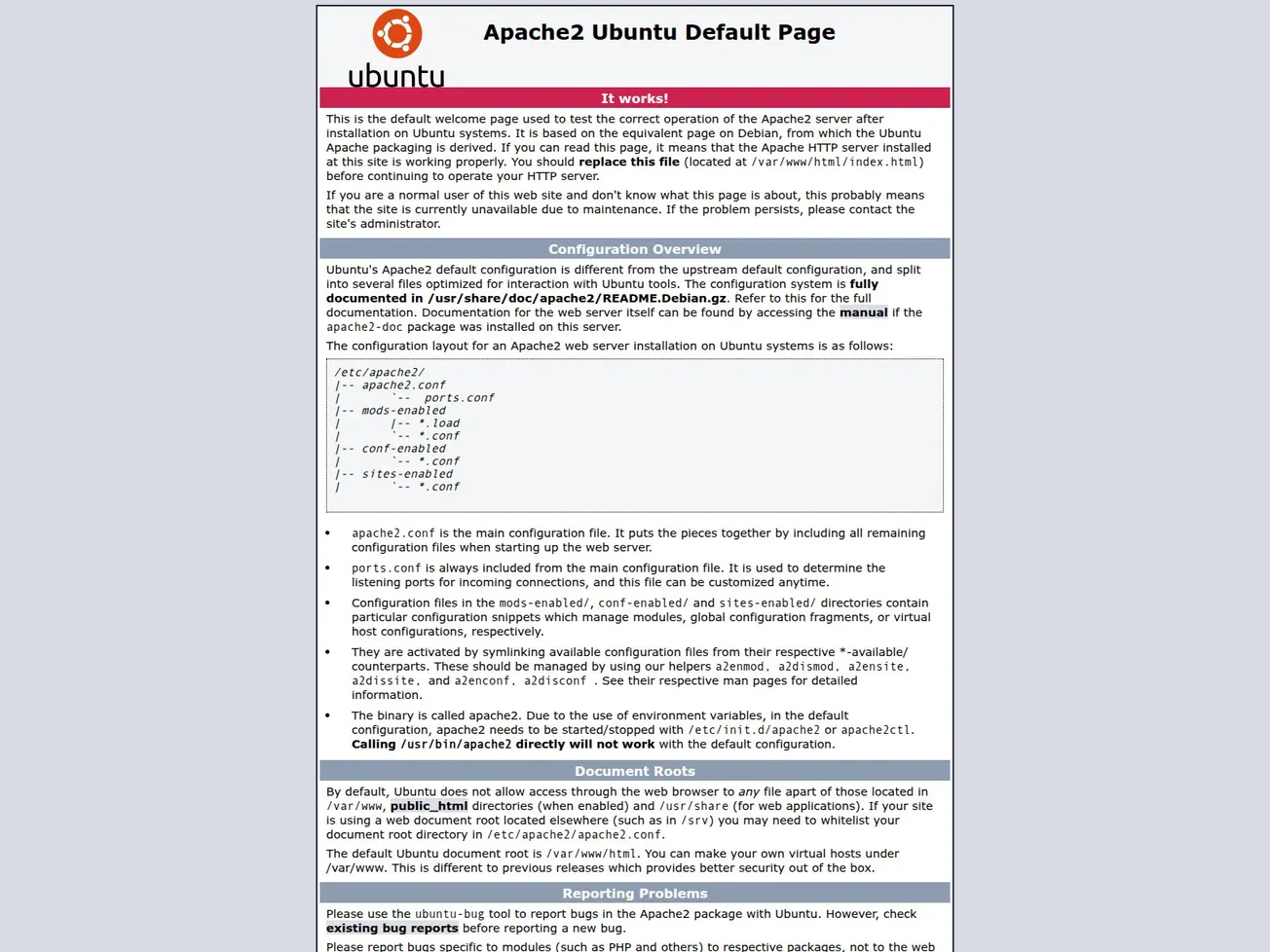
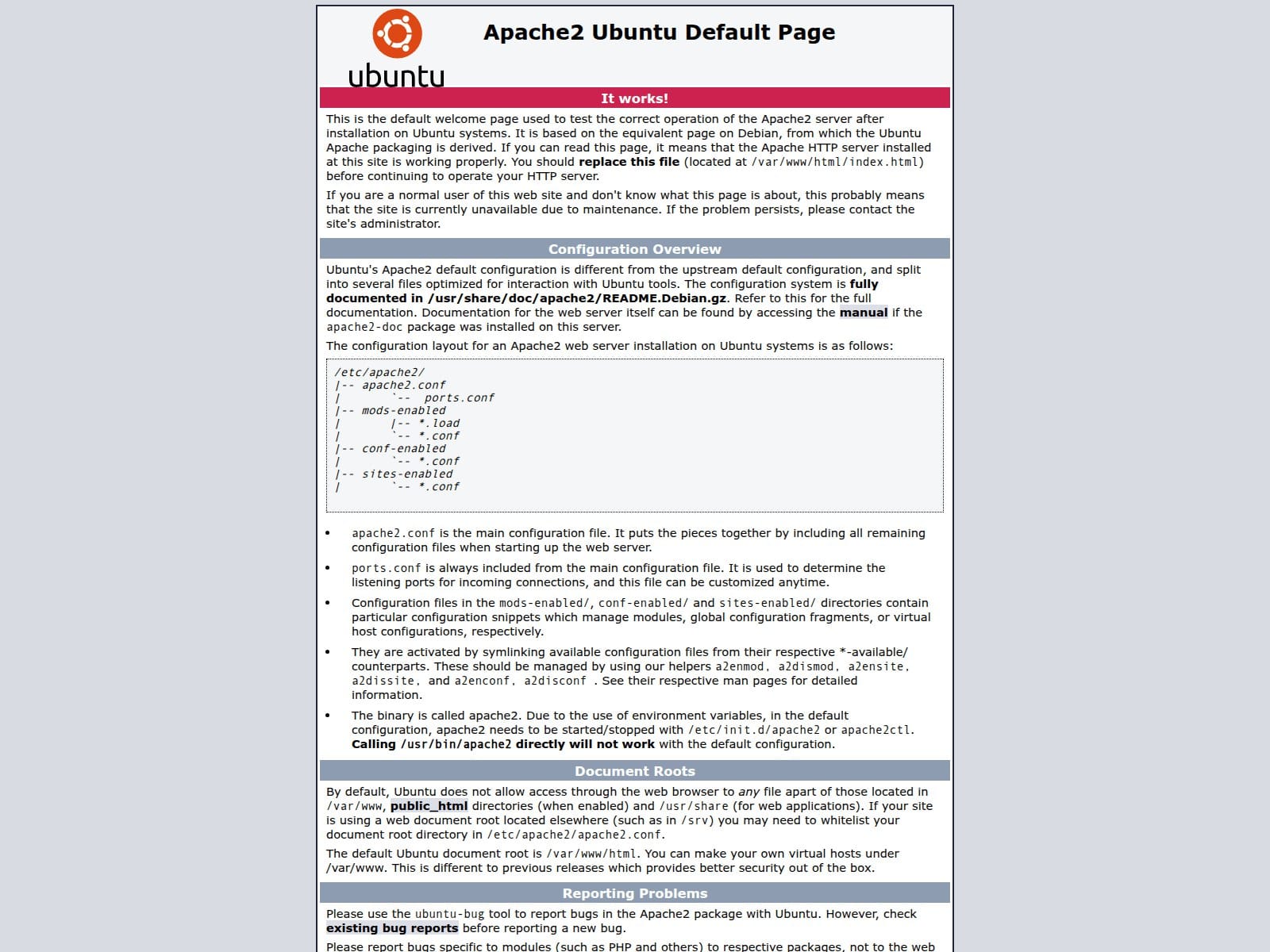
A domain-based indicator has been identified associated with Mirai botnet operations. The infrastructure currently resolves to an IP hosting a default Apache2 Ubuntu landing page, a common sign of a misconfigured or freshly deployed C2 server. Confidence is assessed at 100%.
📌 Key Details
| Field | Information |
|---|---|
| Type | Domain |
| Indicator | animefastflux[.]com |
| Threat Type | Botnet C2 |
| Malware | elf.mirai |
| Confidence | 100% |
| Date | 27 Sep 2025 – 20:20:19 UTC |
| Tags | Mirai |
| Reporter | elfdigest |
🔎 URLScan Result
Verdict Score: 0
Page Title: Apache2 Ubuntu Default Page: It works
Screenshot: https://urlscan.io/screenshots/019877e3-6450-7155-820c-bdb79a6dbee9.png
Result: https://urlscan.io/result/019877e3-6450-7155-820c-bdb79a6dbee9/
📡 Related Intelligence
DNS A Record: 195[.]177[.]94[.]50
Certificate Transparency: https://crt.sh/?q=animefastflux.com
VirusTotal Report: https://www.virustotal.com/gui/domain/animefastflux.com
URLScan Domain Overview: https://urlscan.io/domain/animefastflux.com
DNS Analytics: https://dnslytics.com/domain/animefastflux.com
🛡️ Defensive Guidance
- Block
animefastflux[.]comand its associated IP (195[.]177[.]94[.]50) at DNS, proxy, and endpoint layers. - Monitor for outbound traffic consistent with Mirai C2 beaconing patterns.
- Hunt for IoT devices exhibiting signs of Mirai compromise (e.g., abnormal telnet/SSH traffic).
- Track certificate transparency logs for additional domains tied to Mirai infrastructure.
⚠️ This IOC highlights the continued presence of Mirai botnet C2 servers, often spun up on generic VPS infrastructure with minimal configuration.