📖 Overview
A suspicious GitHub-hosted ZIP file has been identified as part of a payload delivery campaign. The file is associated with SmartLoader activity and was submitted to URLHaus. Hosting on GitHub increases trust abuse, allowing malicious actors to distribute malware under the guise of legitimate repositories. Confidence is assessed at 80%.
📌 Key Details
| Field | Information |
|---|---|
| Type | URL |
| Indicator | https://github.com/dungtaplaptrinh/IVMS/releases/download/v1.0/Release.zip |
| Threat Type | Payload Delivery |
| Malware | Unknown |
| Confidence | 80% |
| Date | 07 Oct 2025 – 17:20:02 UTC |
| Tags | SmartLoader, urlhaus, zip |
| Reporter | Pikachu |
| Reference | None |
🔎 URLScan Result
- Verdict Score: 0
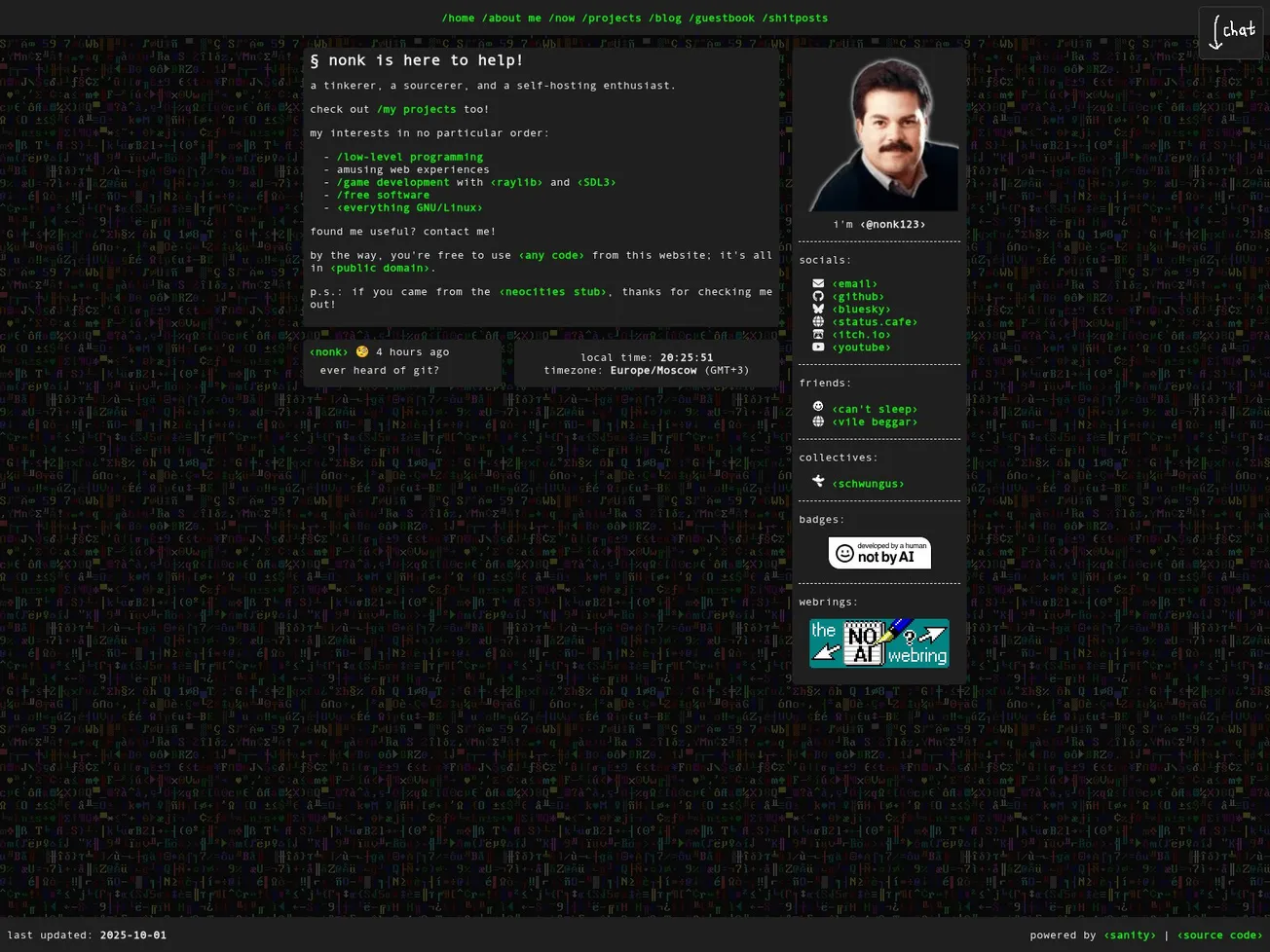
- Page Title: landing page | nonk’s website
- Screenshot: View Screenshot
- Result: Full Scan Report
📡 Related Intelligence
- VirusTotal Report: VirusTotal URL Report
🛡️ Defensive Guidance
- Alert on attempts to download executables or compressed files from GitHub release pages outside of trusted repositories.
- Monitor for SmartLoader infection indicators such as secondary payload downloads and persistence attempts.
- Educate users on the risks of downloading executables from unknown GitHub repositories.
⚠️ This IOC highlights the growing abuse of developer platforms like GitHub to host and deliver malicious payloads, leveraging user trust in popular services to bypass traditional detection.