📖 Overview
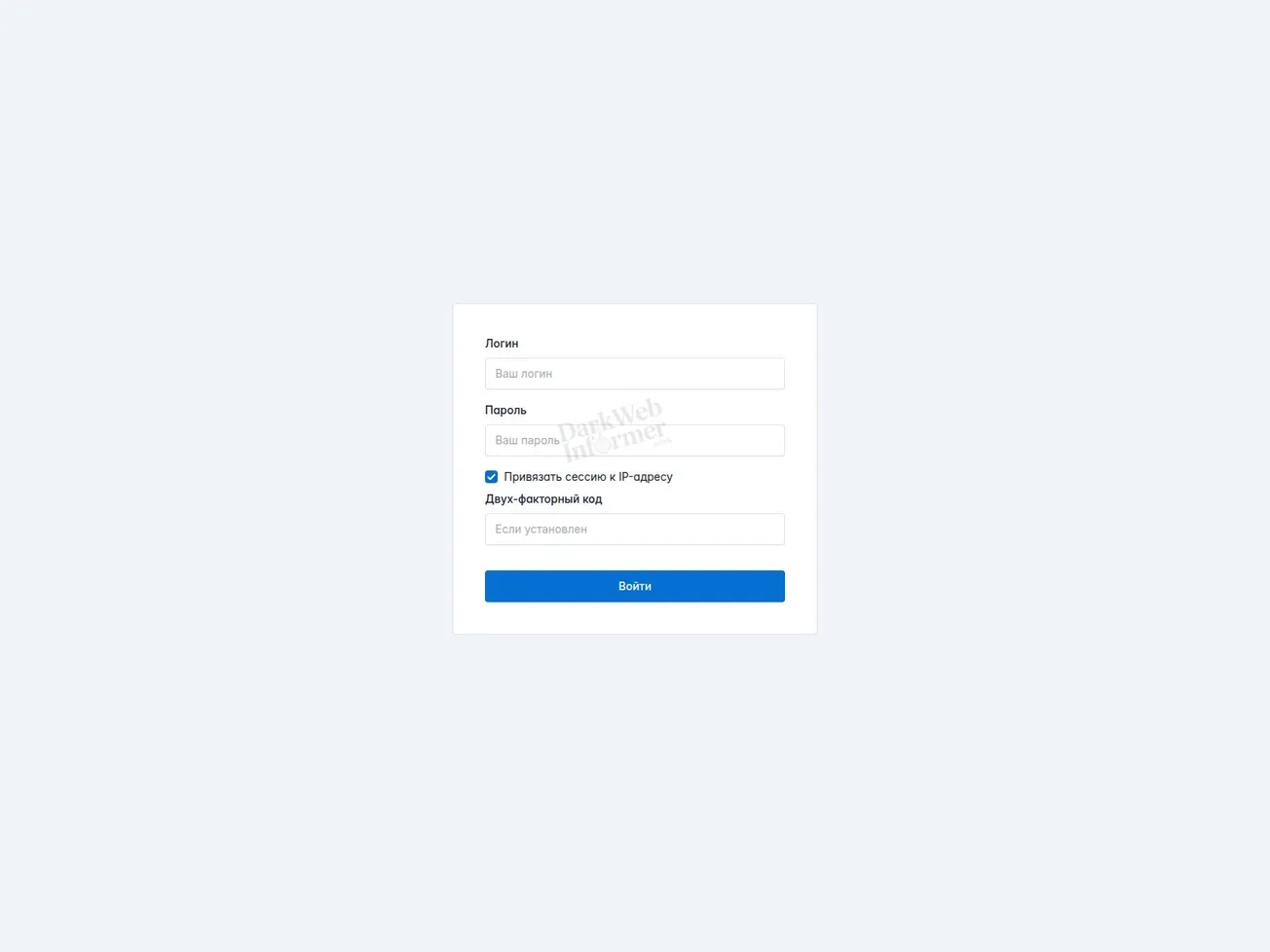
A URL-based indicator has been identified hosting a login panel associated with Lumma Stealer C2 operations. The site presents a credential input form with optional two-factor code support, which is typical for botnet administration portals. Confidence is assessed at 50%, indicating a potential but not yet fully confirmed Lumma C2 instance.
📌 Key Details
| Field | Information |
|---|---|
| Type | URL |
| Indicator | mikhail-bulgakov[.]su/login |
| Threat Type | Botnet C2 |
| Malware | win.lumma |
| Confidence | 50% |
| Date | 16 Sep 2025 – 05:29:46 UTC |
| Tags | C2, Lumma, URLscan |
| Reporter | juroots |
🔎 URLScan Result
Page Title: Вход
Screenshot: https://urlscan.io/screenshots/0199514b-5601-704a-a115-aed83d36d5ee.png
Result: https://urlscan.io/result/0199514b-5601-704a-a115-aed83d36d5ee/
📡 Related Intelligence
VirusTotal Report: https://www.virustotal.com/gui/url/ddd8a3a4dbb465ee338cbda040e254b0eba05fa3802f736c07077b9e39160d4f
Reference: https://urlscan.io/result/01995100-1c34-76d8-adc6-771f837c024c
🛡️ Defensive Guidance
- Block
mikhail-bulgakov[.]suat DNS, proxy, and endpoint layers. - Monitor for HTTP/S traffic attempting to authenticate to
/login. - Hunt for Lumma Stealer IOCs in endpoint logs and memory artifacts.
- Review telemetry for connections to domains mimicking literary or cultural references (a tactic observed in some C2 setups).
⚠️ Confidence is moderate (50%), meaning this IOC should be added to watchlists and monitored closely until more evidence validates its C2 role.