📖 Overview
A domain-based indicator has been identified linked to command-and-control infrastructure for Lumma Stealer. The domain, presenting a Russian-language login portal, is confirmed with high confidence as part of active Lumma C2 operations.
📌 Key Details
| Field | Information |
|---|---|
| Type | Domain |
| Indicator | larpfxs[.]top |
| Threat Type | Botnet C2 |
| Malware | win.lumma |
| Confidence | 100% |
| Date | 31 Aug 2025 – 20:26:53 UTC |
| Tags | c2, domain, Lumma, stealer |
| Reporter | DonPasci |
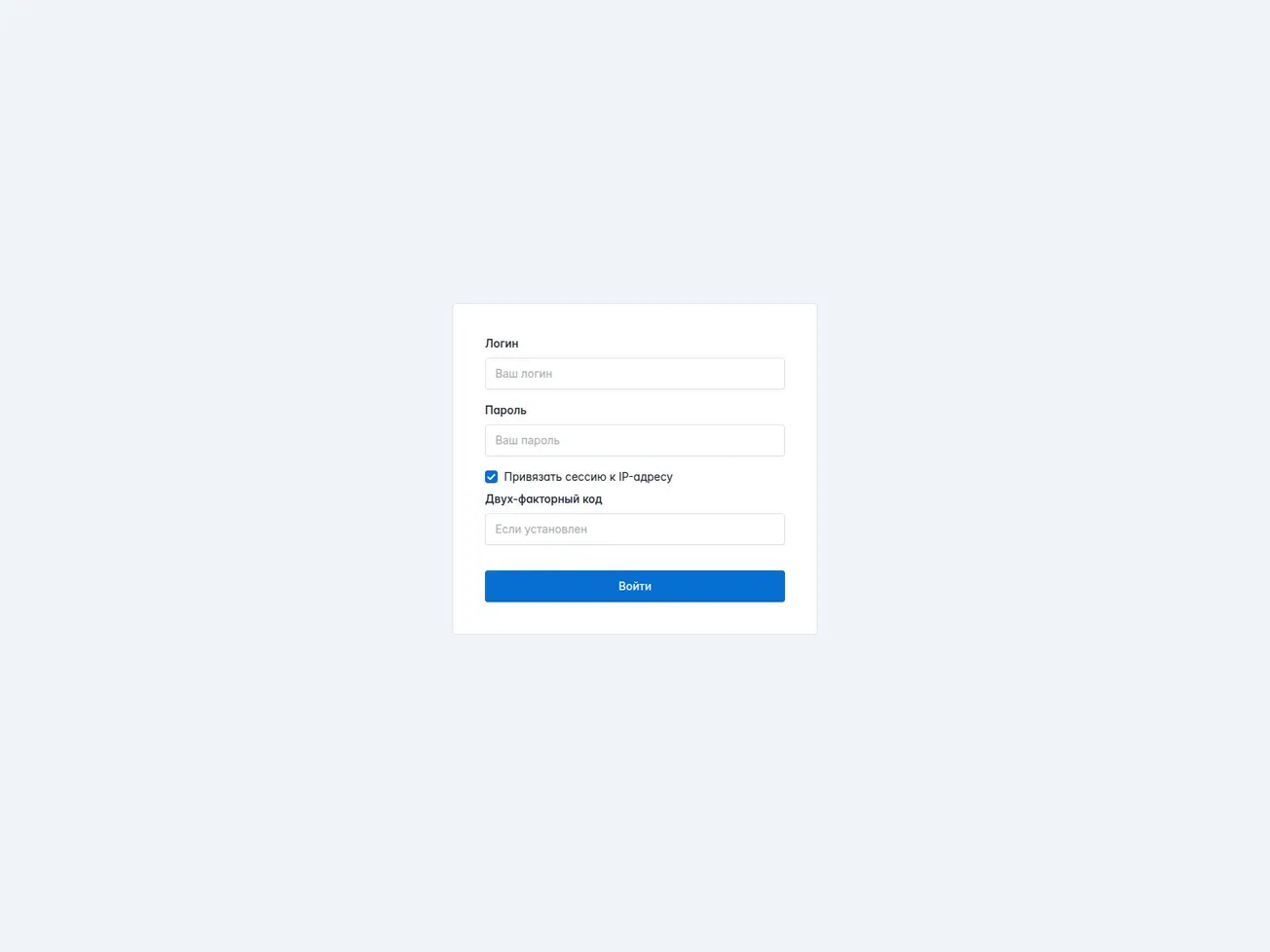
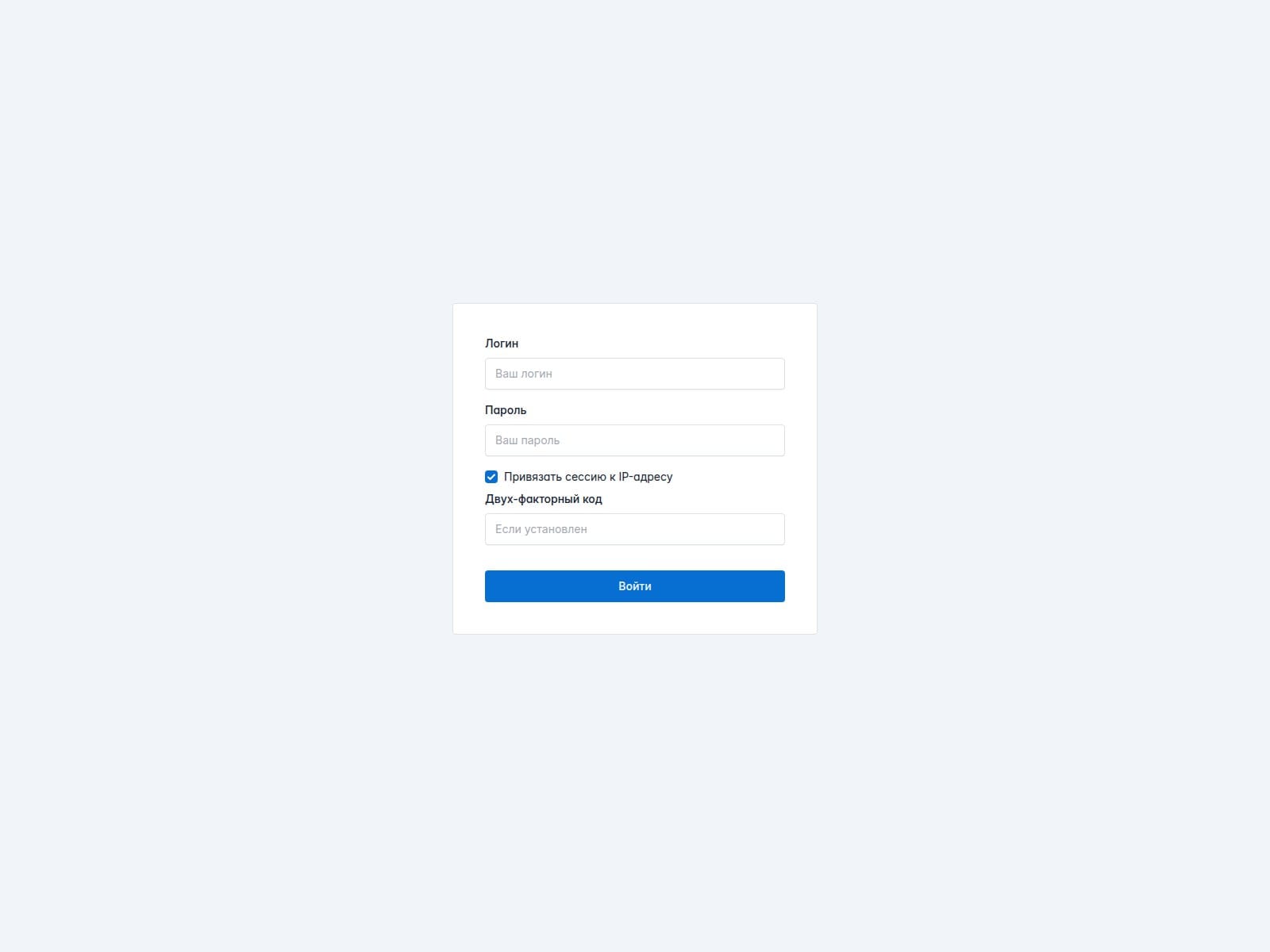
🔎 URLScan Result
Page Title: Вход
Screenshot: https://urlscan.io/screenshots/0198fd5b-0763-7058-8bf4-5a8a755b9cfe.png
Result: https://urlscan.io/result/0198fd5b-0763-7058-8bf4-5a8a755b9cfe/
📡 Related Intelligence
WHOIS Record: https://who.is/whois/larpfxs.top
VirusTotal Report: https://www.virustotal.com/gui/domain/larpfxs.top
🛡️ Defensive Guidance
- Block
larpfxs[.]topat DNS, proxy, and endpoint layers. - Monitor for Lumma Stealer callbacks and credential exfiltration attempts.
- Hunt for stealer payloads and persistence mechanisms in endpoint telemetry.
- Review DNS and proxy logs for suspicious outbound requests to this domain.