📖 Overview
An API endpoint has been flagged that is associated with the Lumma information stealer malware family. The infrastructure is fronted by Cloudflare and currently requires human verification to proceed, but is believed to function as a command-and-control (C2) channel for Lumma. Confidence is assessed at 75%.
📌 Key Details
| Field | Information |
|---|---|
| Type | URL |
| Indicator | https://agentgrabber[.]com/api |
| Threat Type | Botnet C2 |
| Malware | win.lumma |
| Confidence | 75% |
| Date | 01 Oct 2025 – 17:31:21 UTC |
| Tags | c2, Lumma, stealer |
| Reporter | ninjacatcher |
| Reference | None |
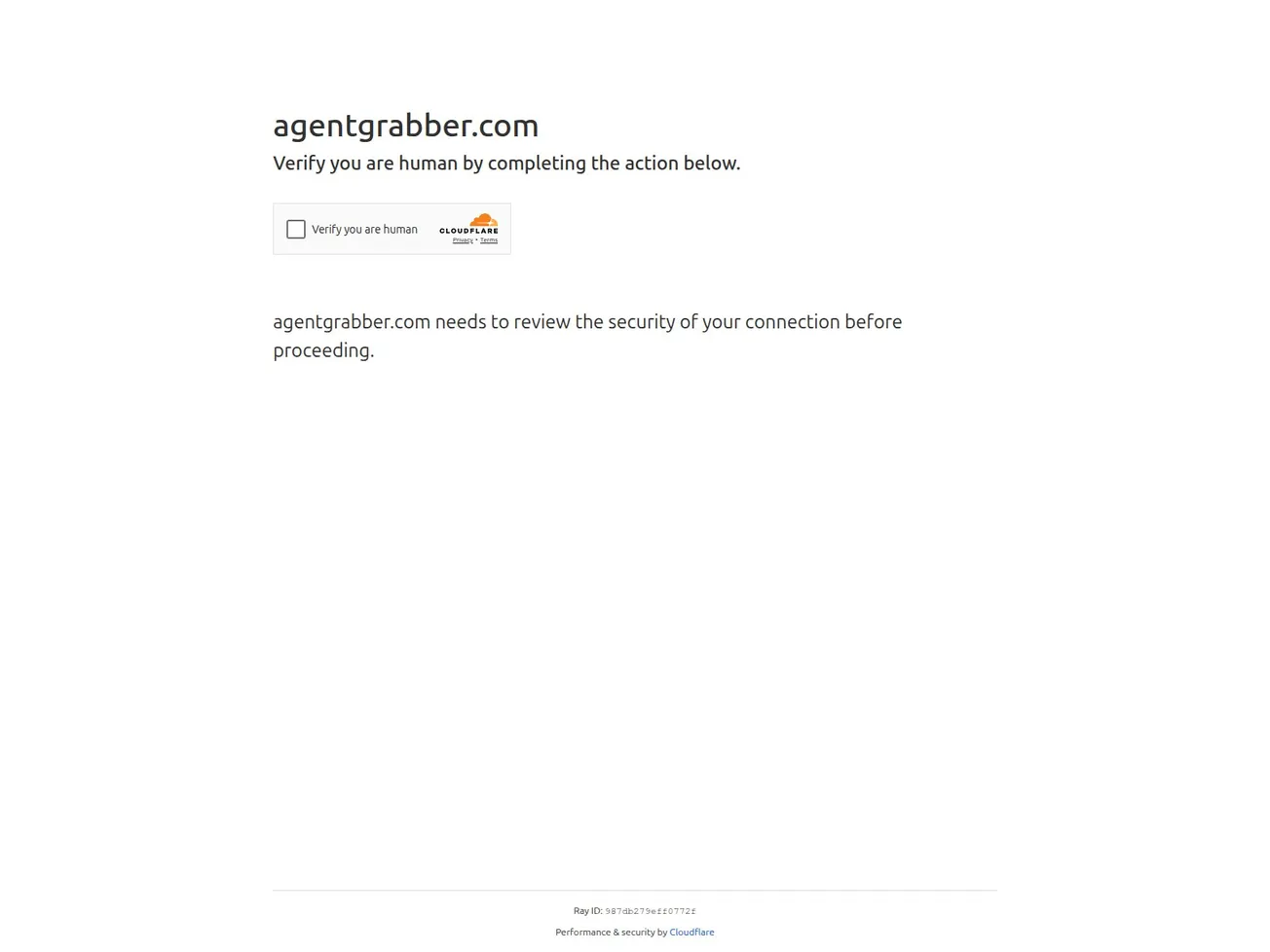
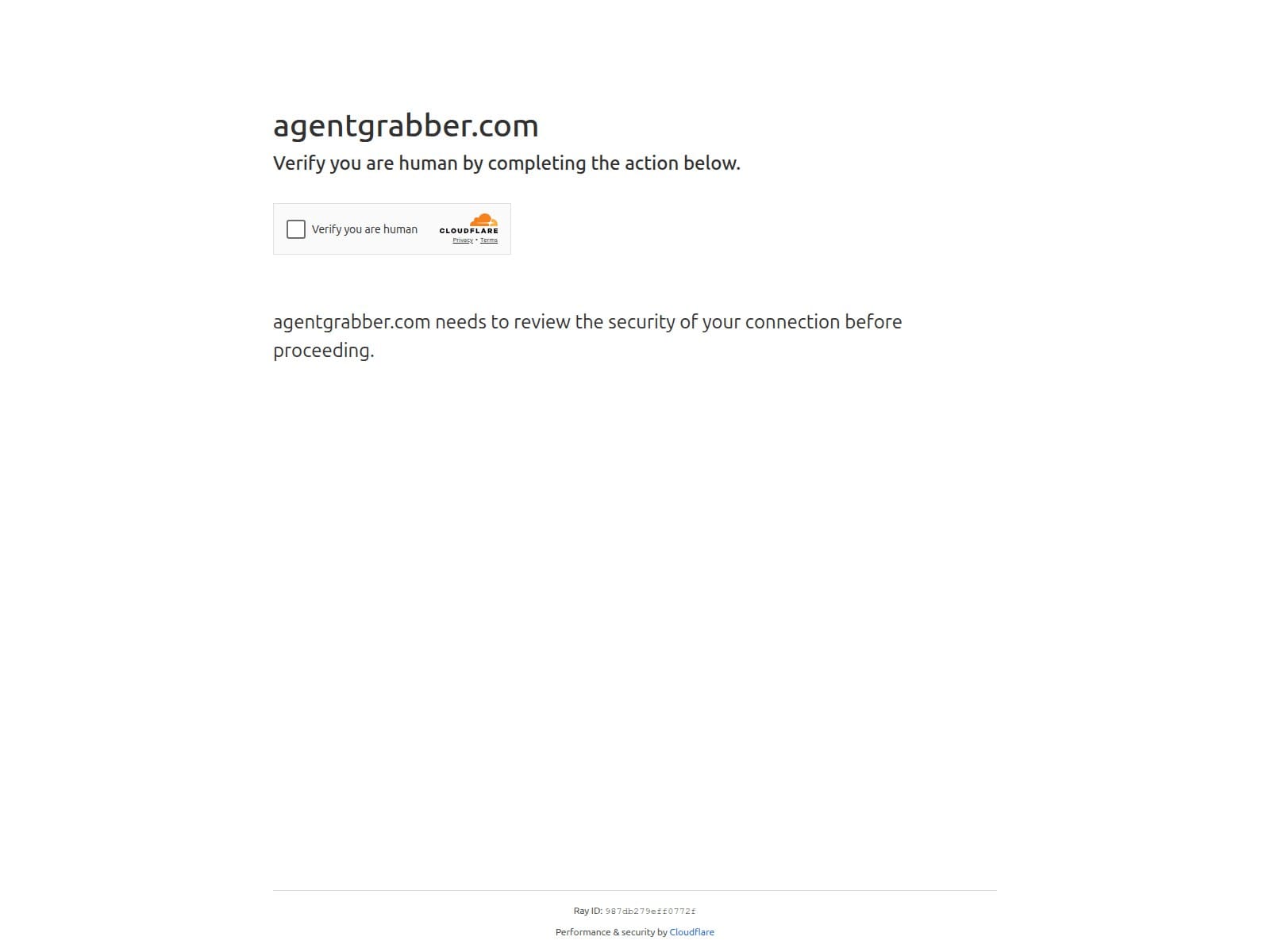
🔎 URLScan Result
- Verdict Score: 0
- Page Title: Just a moment…
- Screenshot: View Screenshot
- Result: Full Scan Report
📡 Related Intelligence
- VirusTotal Report: VirusTotal URL Report
🛡️ Defensive Guidance
- Block agentgrabber[.]com and its API endpoint at DNS, proxy, and firewall layers.
- Monitor for HTTP(S) traffic directed at this domain, particularly API request patterns indicative of C2 activity.
- Hunt for compromised endpoints communicating with the Lumma stealer C2 framework.
- Consider placing detection rules for outbound requests containing
/apion suspicious domains tied to Lumma operations.
⚠️ This IOC highlights the continued evolution of Lumma stealer infrastructure, which frequently leverages Cloudflare or other protective services to obscure malicious endpoints from analysis.