📖 Overview
A JavaScript payload associated with the Kongtuke malware family has been discovered hosted on a compromised domain masquerading as a restaurant website. The malicious script is delivered via js.php, a common filename used in JavaScript injection attacks, and is believed to be part of a broader payload delivery campaign. Confidence is assessed at 100%.
📌 Key Details
| Field | Information |
|---|---|
| Type | URL |
| Indicator | https://prixmatech[.]com/js.php |
| Threat Type | Payload Delivery |
| Malware | js.kongtuke |
| Confidence | 100% |
| Date | 14 Oct 2025 – 18:19:55 UTC |
| Tags | Kongtuke |
| Reporter | monitorsg |
| Reference | None |
🔎 URLScan Result
- Verdict Score: 0
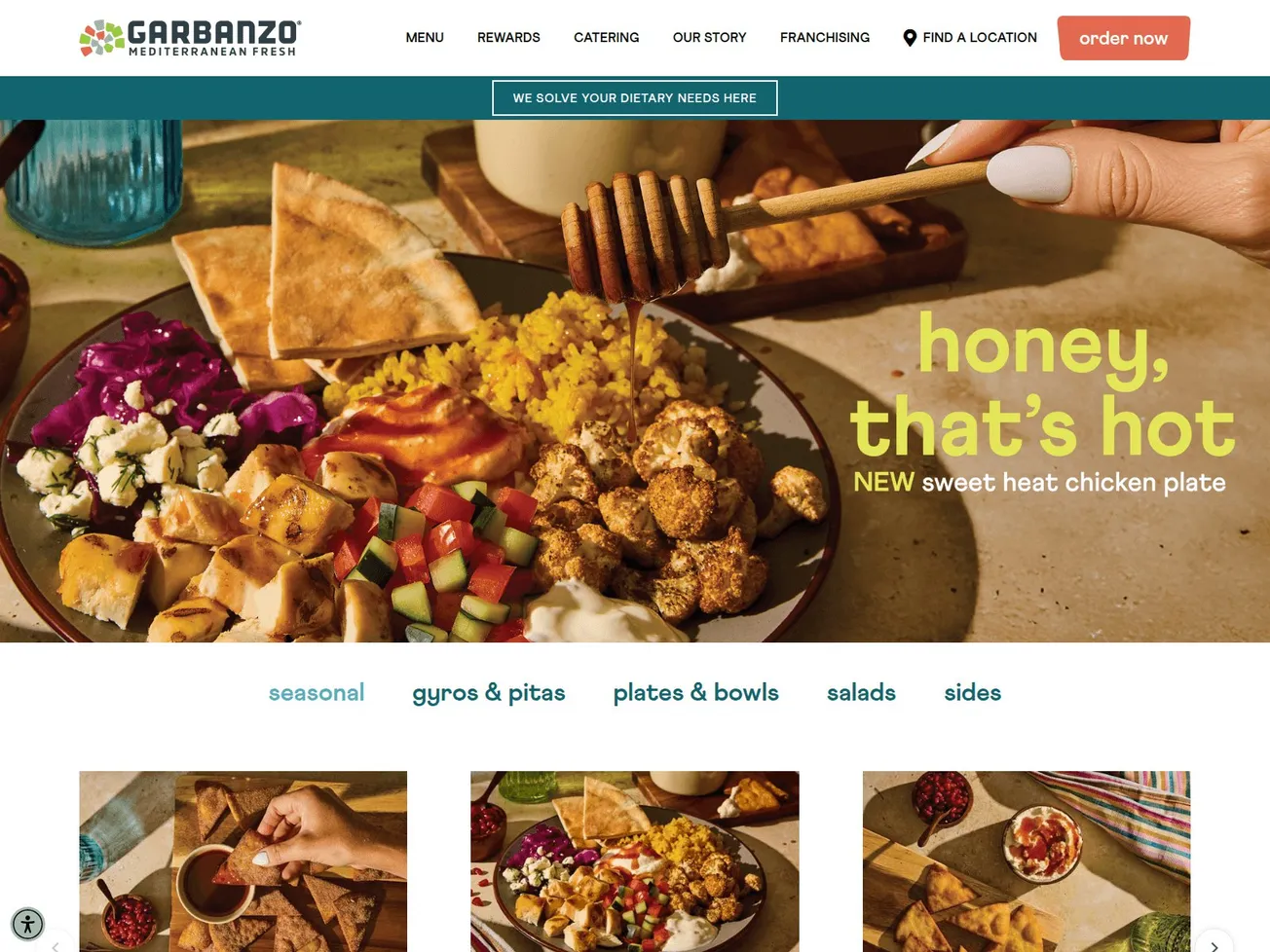
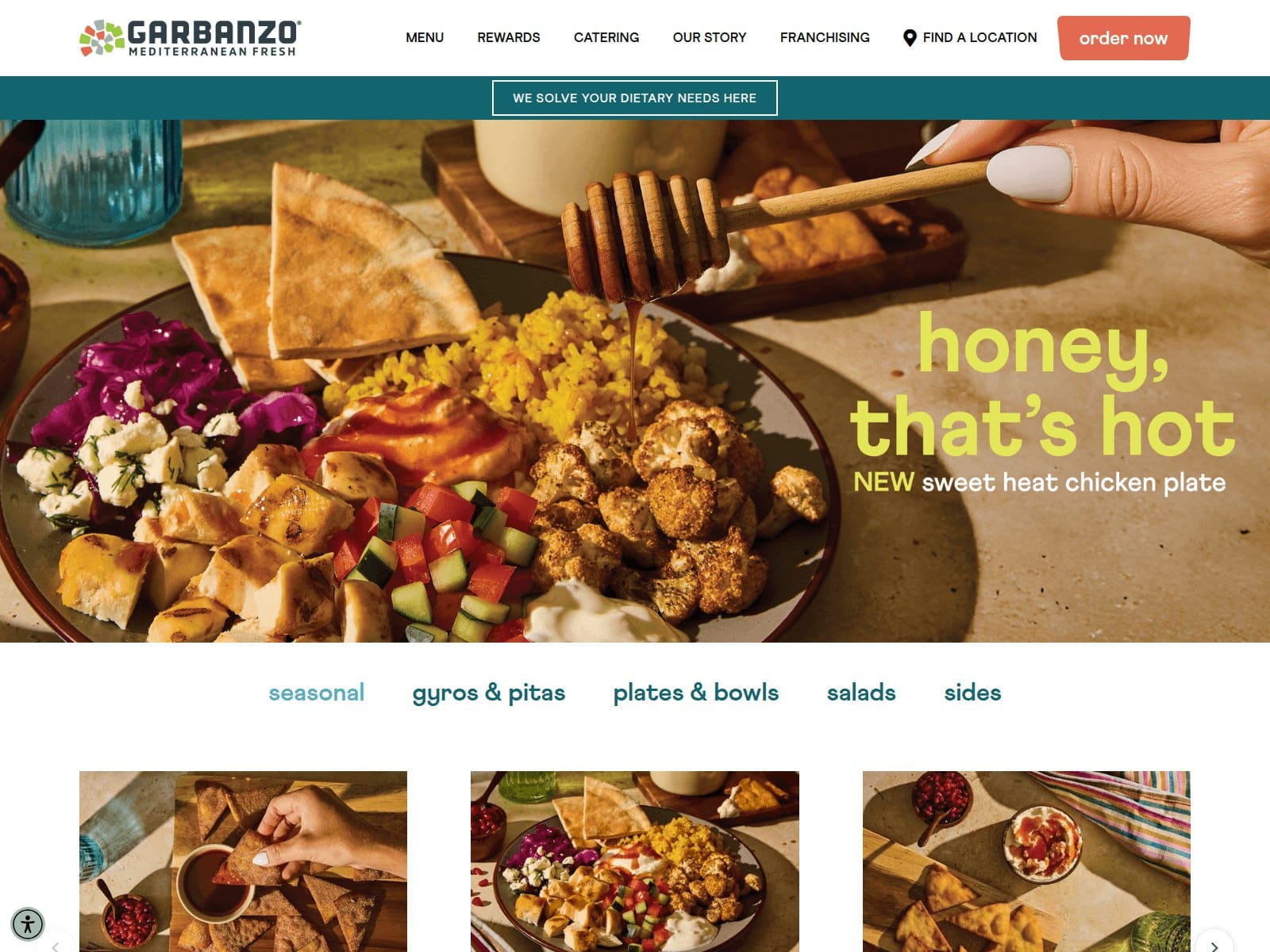
- Page Title: Garbanzo Mediterranean Restaurant Near Me | Pita, Salad, Gyro, Bowls
- Screenshot: View Screenshot
- Result: Full Scan Report
📡 Related Intelligence
- VirusTotal Report: VirusTotal URL Report
🛡️ Defensive Guidance
- Block access to prixmatech[.]com and any requests to /js.php endpoints across DNS, proxy, and web gateways.
- Inspect web server logs for any evidence of injected JavaScript payloads or external script loading from suspicious domains.
- Monitor for execution of scripts or network calls tied to Kongtuke signatures.
- Deploy content security policies (CSP) to limit JavaScript execution from untrusted origins.
⚠️ This IOC highlights the use of legitimate-looking commercial websites as decoy fronts for distributing JavaScript-based malware like Kongtuke, which often targets users through embedded scripts or drive-by infection techniques.