📖 Overview
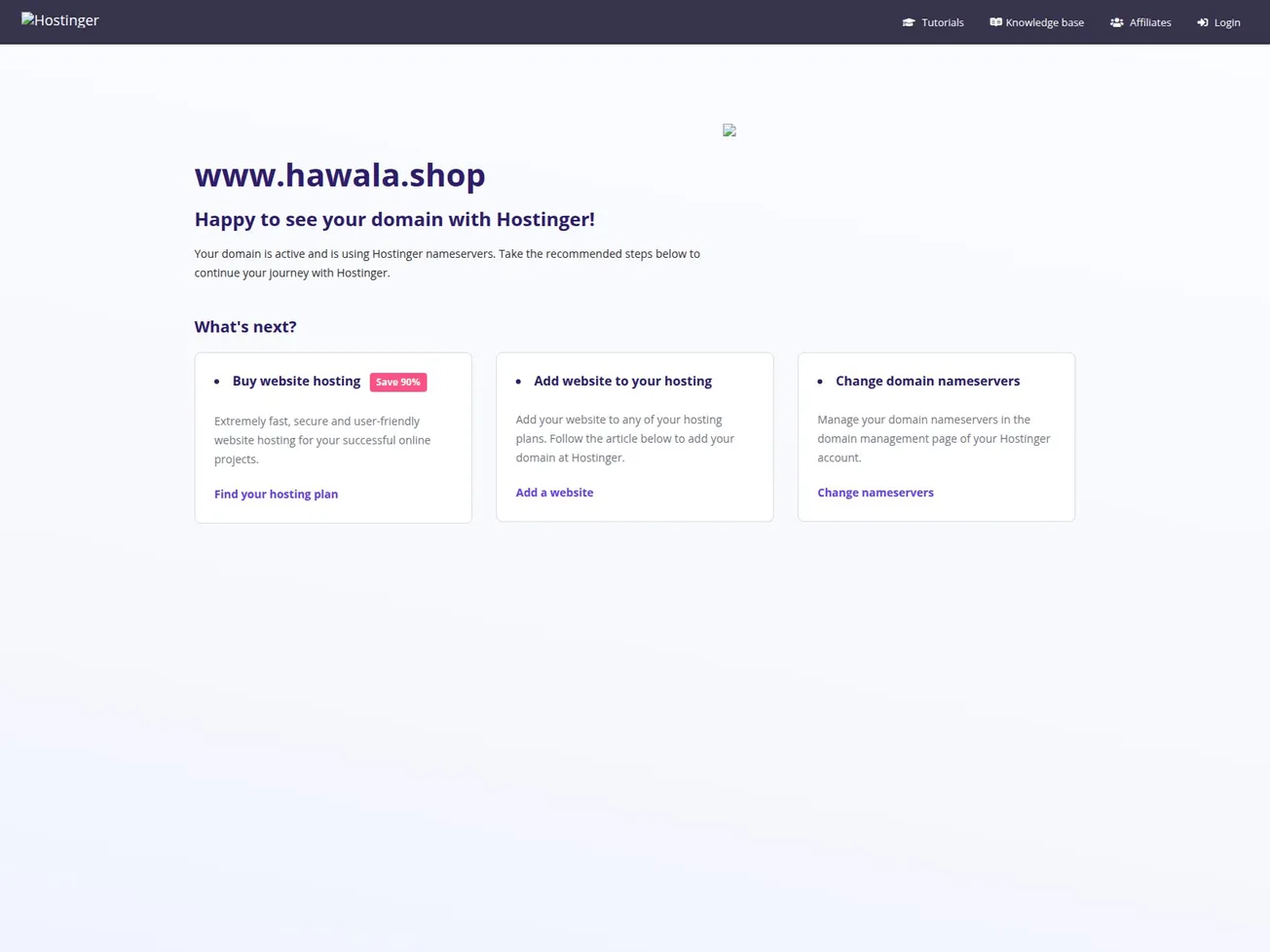
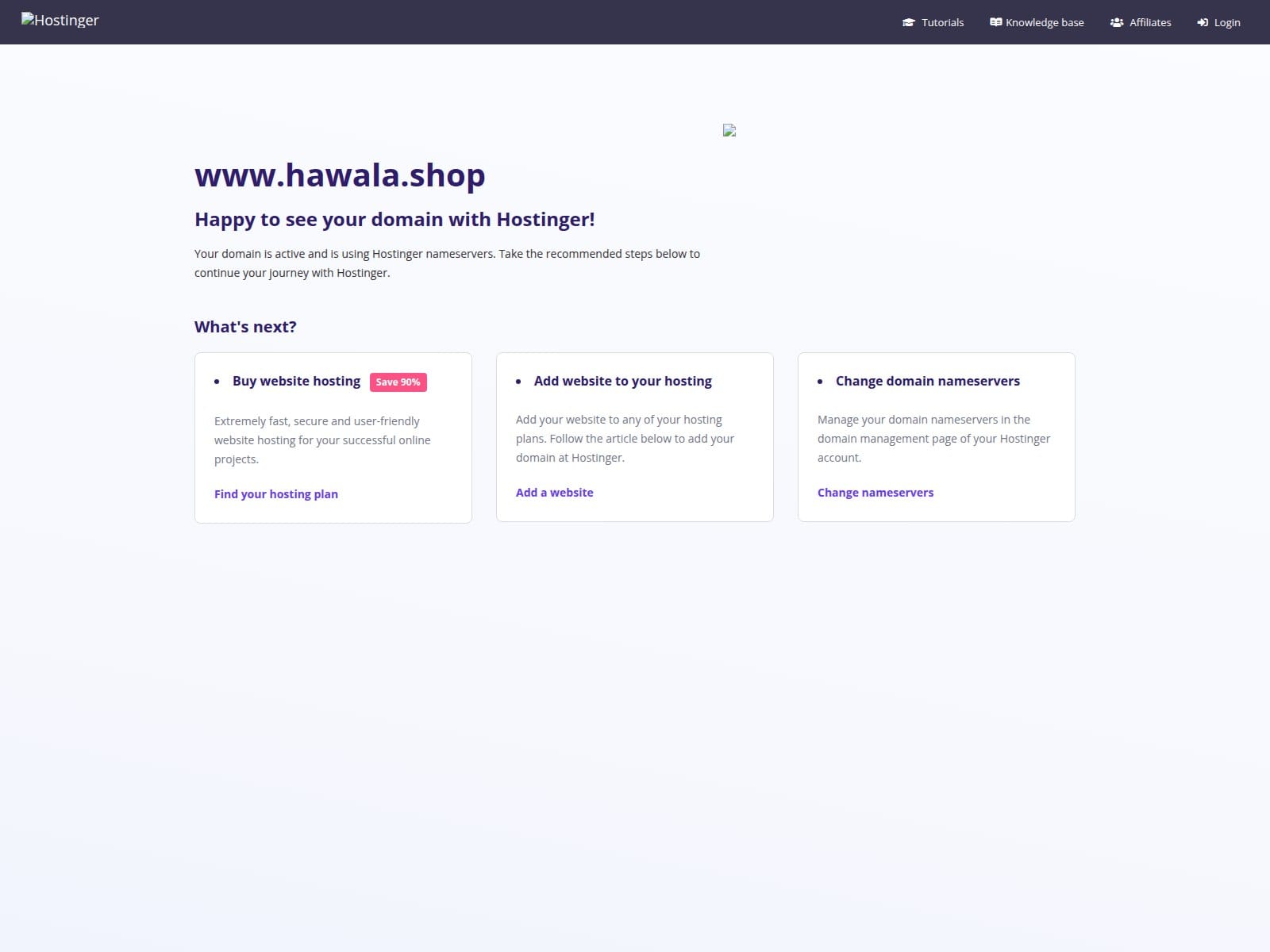
A domain has been identified as potential infrastructure supporting the Formbook stealer malware family. While the domain currently appears as a parked page on Hostinger’s DNS system, certificate records and passive DNS suggest prior use for malicious activity. Confidence in the attribution is assessed at 50%.
📌 Key Details
| Field | Information |
|---|---|
| Type | Domain |
| Indicator | www.hawala[.]shop |
| Threat Type | Botnet C2 |
| Malware | win.formbook |
| Confidence | 50% |
| Date | 03 Oct 2025 – 14:22:32 UTC |
| Tags | c2, Formbook |
| Reporter | juroots |
| Reference | None |
🔎 URLScan Result
- Verdict Score: 0
- Page Title: Parked Domain name on Hostinger DNS system
- Screenshot: View Screenshot
- Result: Full Scan Report
📡 Domain & Certificate Info
- DNS A Record: 84[.]32[.]84[.]32
- DNS AAAA Record: hawala.shop
- MX Record: hawala.shop
- Recent Certificates:
- C=US, O=Let's Encrypt, CN=R10 (Valid: 2025-04-15 → 2025-07-14)
- C=US, O=Let's Encrypt, CN=R10 (Valid: 2025-04-15 → 2025-07-14)
- C=US, O=Let's Encrypt, CN=R3 (Valid: 2023-06-16 → 2023-09-14)
📡 Related Intelligence
- Certificate Transparency: crt.sh Report
- VirusTotal Report: VirusTotal Domain Report
- URLScan Domain Overview: urlscan.io Domain Page
- DNS Analytics: dnslytics.com Report
🛡️ Defensive Guidance
- Block www.hawala[.]shop and its associated IP (84[.]32[.]84[.]32) at DNS, proxy, and endpoint levels.
- Monitor for traffic patterns associated with Formbook stealer, including suspicious POST requests or credential exfiltration attempts.
- Add Formbook-related domains to SIEM or threat hunting dashboards for proactive detection.
- Leverage certificate transparency monitoring to identify new infrastructure registered for Formbook campaigns.
⚠️ This IOC highlights the reuse of commodity domains and cheap hosting setups to stage or disguise Formbook C2 infrastructure, often hiding behind parked pages when not actively engaged in operations.