📖 Overview
A malicious FakeCaptcha payload delivery was identified on a compromised webpage hosted at analyticscampus.com. The site masquerades as a legitimate technology article discussing a self-propagating Visual Studio Code worm, but instead presents a deceptive verification prompt instructing users to execute commands on macOS systems. This pattern is consistent with FakeCaptcha social engineering campaigns designed to trick users into executing remote payloads or granting command-line access. Confidence is assessed at 50%.
📌 Key Details
| Field | Information |
|---|---|
| Type | URL |
| Indicator | https://analyticscampus[.]com/self-propagating-worm-present-in-marketplaces-for-visible-studio-code-extensions/ |
| Threat Type | Payload Delivery |
| Malware | Unknown (FakeCaptcha Framework) |
| Confidence | 50% |
| Date | 31 Oct 2025 – 13:10:11 UTC |
| Tags | FakeCaptcha |
| Reporter | juroots |
| Reference | None |
🔎 URLScan Result
- Verdict Score: 0
- Page Title: Self-propagating worm present in marketplaces for Visible Studio Code extensions - Analytics Campus
- Screenshot: View Screenshot
- Result: Full Scan Report
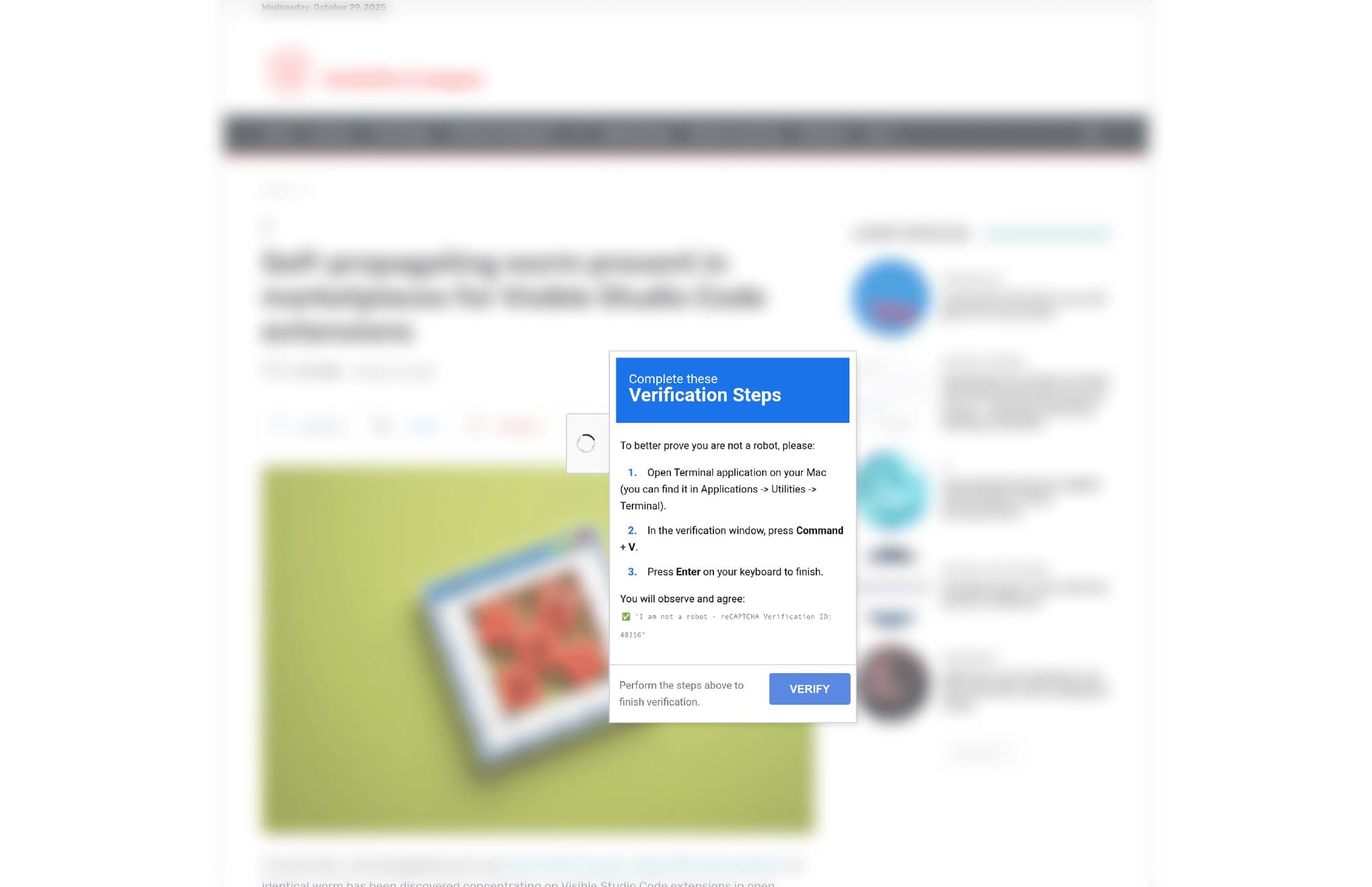
📡 Related Intelligence
- VirusTotal Report: VT URL Analysis
🛡️ Defensive Guidance
- Block or quarantine access to analyticscampus[.]com pending verification of compromise.
- Educate users on FakeCaptcha behavior — any “verify you’re human” prompt instructing users to execute commands in a terminal is malicious.
- Monitor DNS, proxy, and endpoint logs for access attempts to the above domain and associated URLs.
- Consider implementing browser isolation or enhanced inspection on lesser-known technology news and code-sharing sites, which are frequently hijacked for payload delivery.
⚠️ This IOC underscores the continuing evolution of FakeCaptcha techniques, where adversaries leverage legitimate-looking tech articles and tutorials to distribute malicious verification prompts targeting macOS and Windows users alike.