📖 Overview
A domain-based indicator has been identified delivering ClearFake JavaScript malware. The domain is flagged for phishing and payload delivery activity and is associated with malicious script injection campaigns designed to trick users into interacting with fraudulent browser updates or phishing pages. Confidence is assessed at 100%.
📌 Key Details
| Field | Information |
|---|---|
| Type | Domain |
| Indicator | q5[.]f-11[.]ru |
| Threat Type | Payload Delivery |
| Malware | js.clearfake |
| Confidence | 100% |
| Date | 18 Sep 2025 – 14:53:02 UTC |
| Tags | ClearFake |
| Reporter | anonymous |
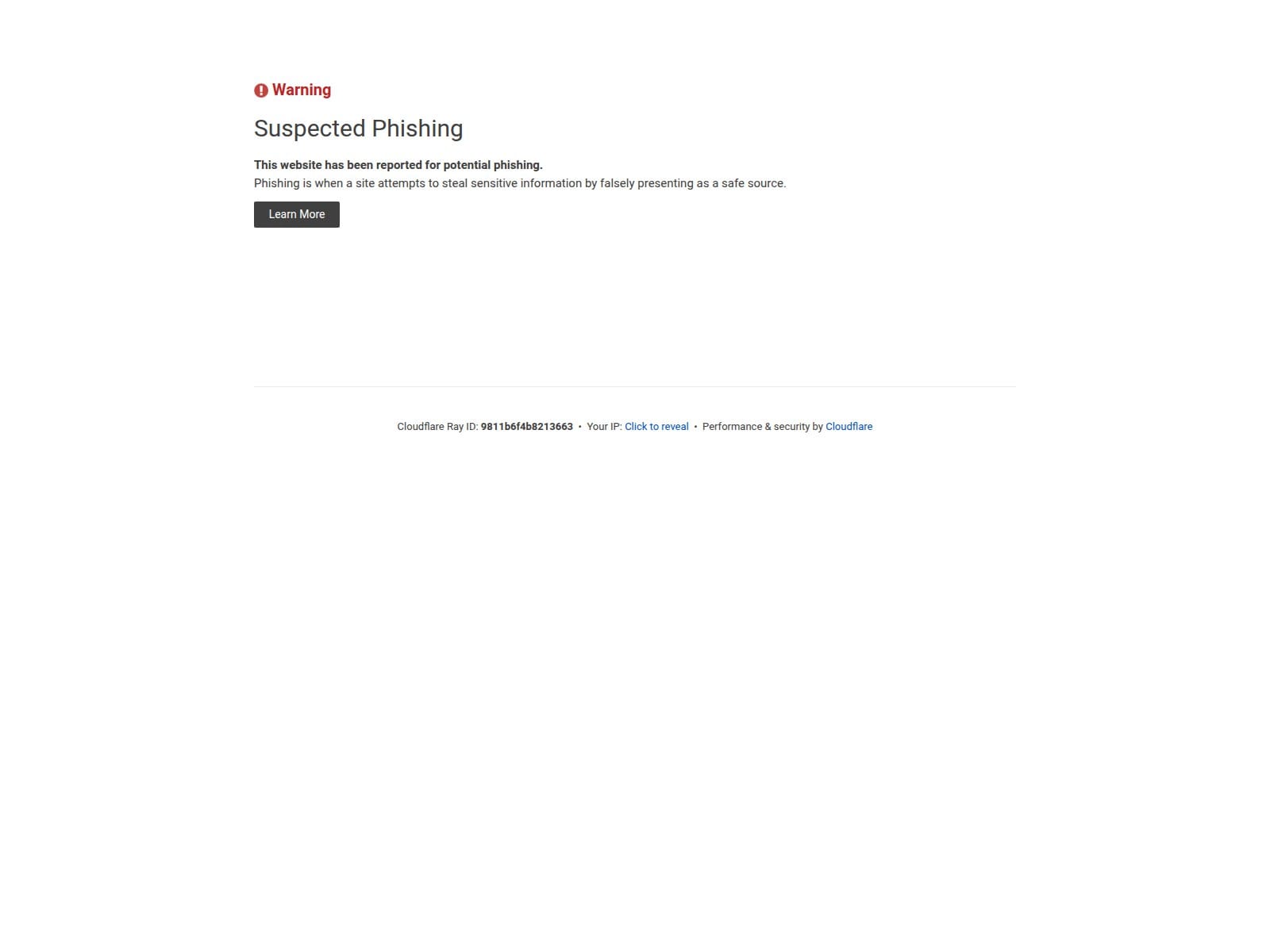
🔎 URLScan Result
Verdict: 100
Page Title: Suspected phishing site | Cloudflare
Screenshot: https://urlscan.io/screenshots/01995d57-9466-731a-9b97-ee1d5155dbcd.png
Result: https://urlscan.io/result/01995d57-9466-731a-9b97-ee1d5155dbcd/
📡 Related Intelligence
WHOIS Record: https://who.is/whois/q5.f-11.ru
VirusTotal Report: https://www.virustotal.com/gui/domain/q5.f-11.ru
🛡️ Defensive Guidance
- Block
q5[.]f-11[.]ruat DNS, proxy, and endpoint levels. - Monitor for injected JavaScript and browser update lures.
- Hunt for ClearFake script activity across web gateways and browser telemetry.
- Educate users about fraudulent browser update prompts as part of awareness training.
⚠️ ClearFake continues to leverage phishing-style delivery with Cloudflare error overlays to trick victims, highlighting the need for layered defenses.









