📖 Overview
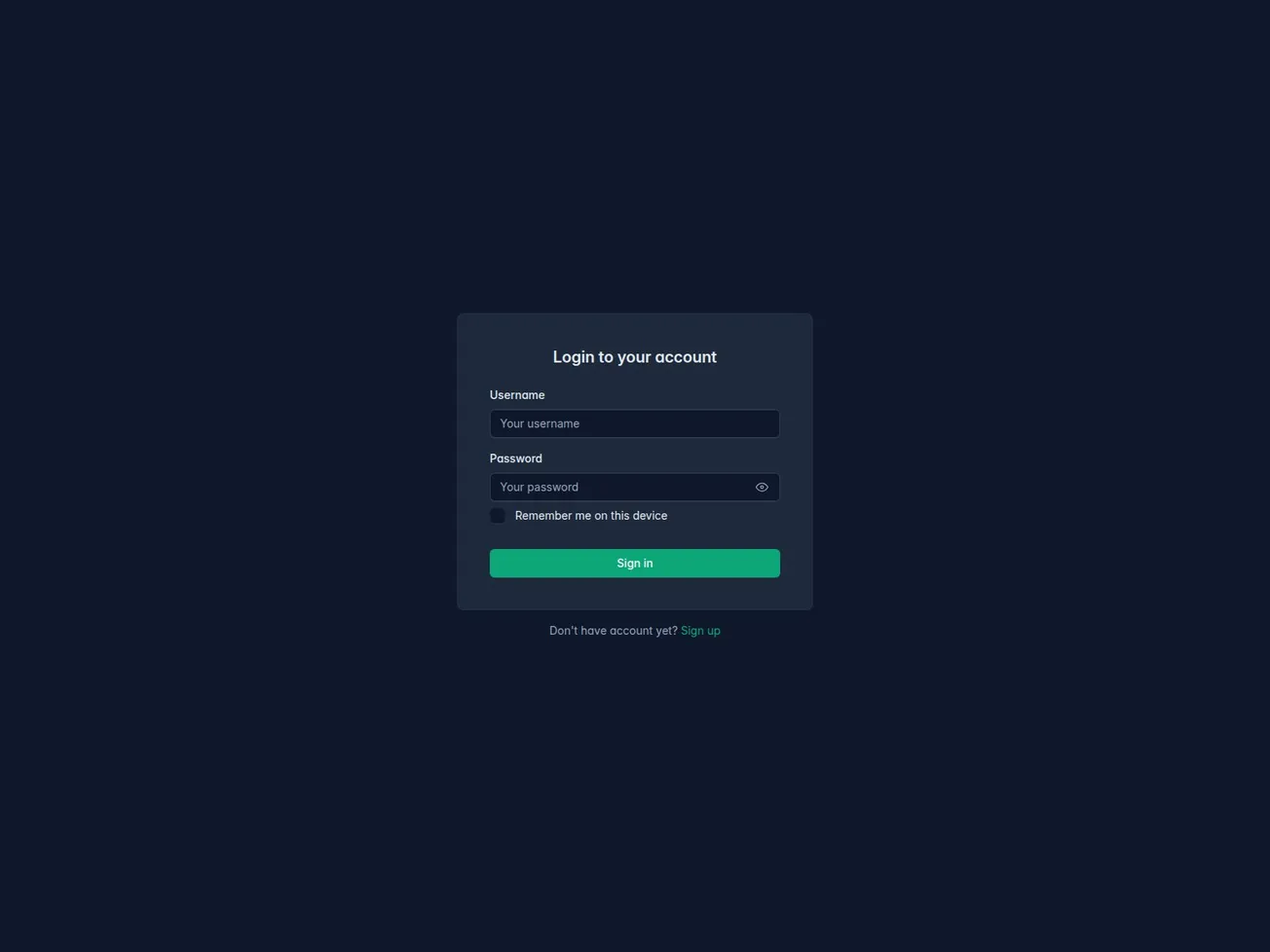
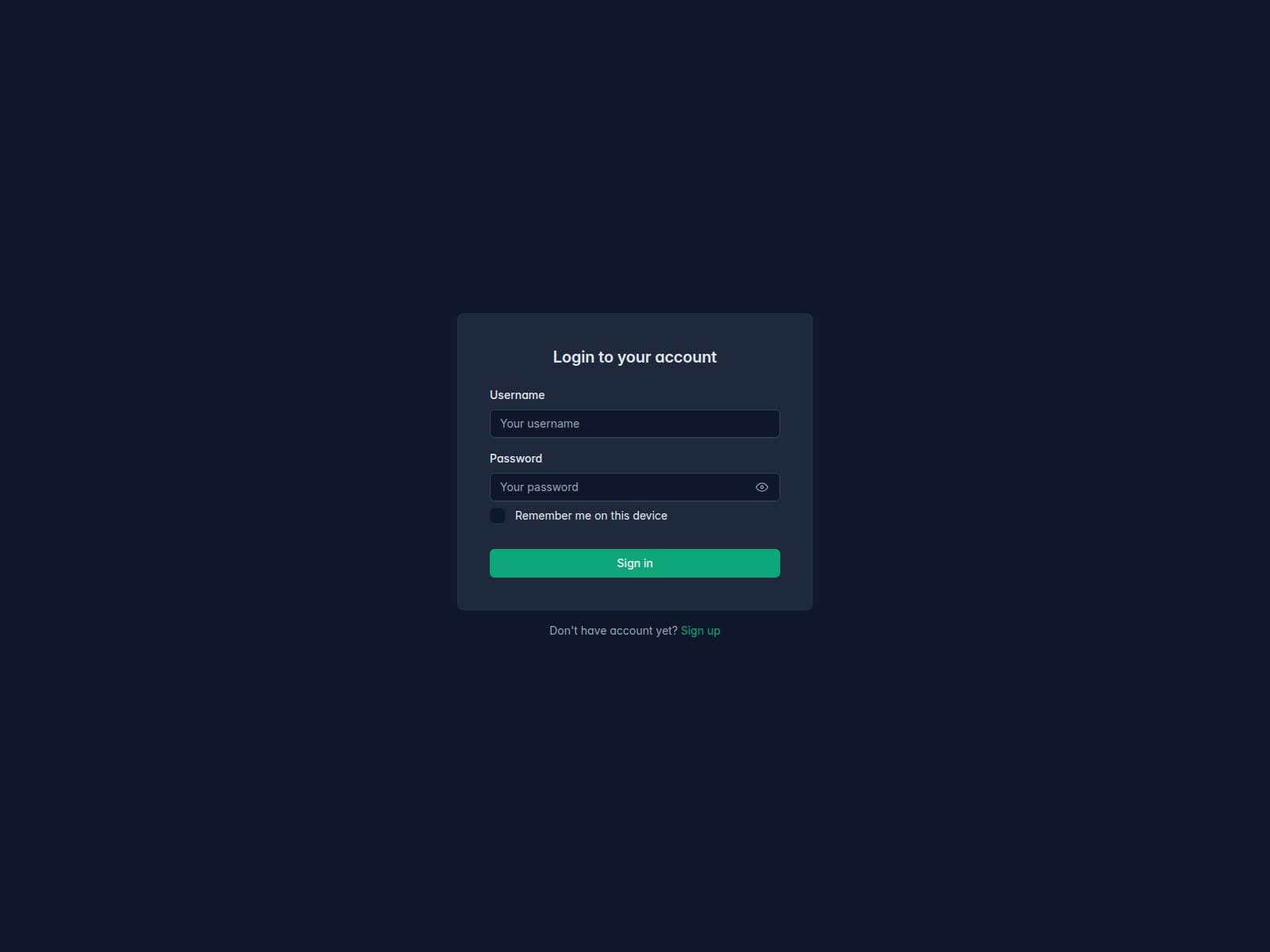
A domain-based indicator tied to command-and-control infrastructure for AuraStealer has been identified. The domain poses a high-confidence threat and disguises itself with a generic login page to support malicious C2 operations.
📌 Key Details
| Field | Information |
|---|---|
| Type | Domain |
| Indicator | softytoys[.]shop |
| Threat Type | Botnet C2 |
| Malware | unknown_stealer (AuraStealer) |
| Confidence | 100% |
| Date | 30 Aug 2025 – 14:44:14 UTC |
| Tags | AuraStealer |
| Reporter | abuse_ch |
🔎 URLScan Result
Page Title: Sign in
Screenshot: https://urlscan.io/screenshots/0198cb96-bce3-73ee-a9b3-8400d5a011dd.png
Result: https://urlscan.io/result/0198cb96-bce3-73ee-a9b3-8400d5a011dd/
📡 Related Intelligence
WHOIS Record: https://who.is/whois/softytoys.shop
VirusTotal Report: https://www.virustotal.com/gui/domain/softytoys.shop
Reference: https://foresiet.com/blog/aura-stealer-malware-analysis/
🛡️ Defensive Guidance
- Block
softytoys[.]shopat DNS, proxy, and endpoint layers. - Monitor for C2 callbacks and credential theft tied to AuraStealer.
- Hunt for persistence artifacts and stealer-related payloads on endpoints.
- Review DNS, proxy, and firewall logs for traffic to the domain.