📖 Overview
A new domain-based indicator has been identified linked to botnet command-and-control infrastructure for apk.hook (HookBot). The domain, hosted under Hetzner (AS24940), is tied to ERMAC v3.0 activity and represents a high-confidence threat to Android devices targeted by banking trojans.
📌 Key Details
| Field | Information |
|---|---|
| Type | Domain |
| Indicator | www.libertydroid-magma[.]top |
| Threat Type | Botnet C2 |
| Malware | apk.hook |
| Confidence | 100% |
| Date | 30 Aug 2025 – 00:01:04 UTC |
| Tags | AS24940, C2, Censys, HETZNER-AS, HookBot |
| Reporter | DonPasci |
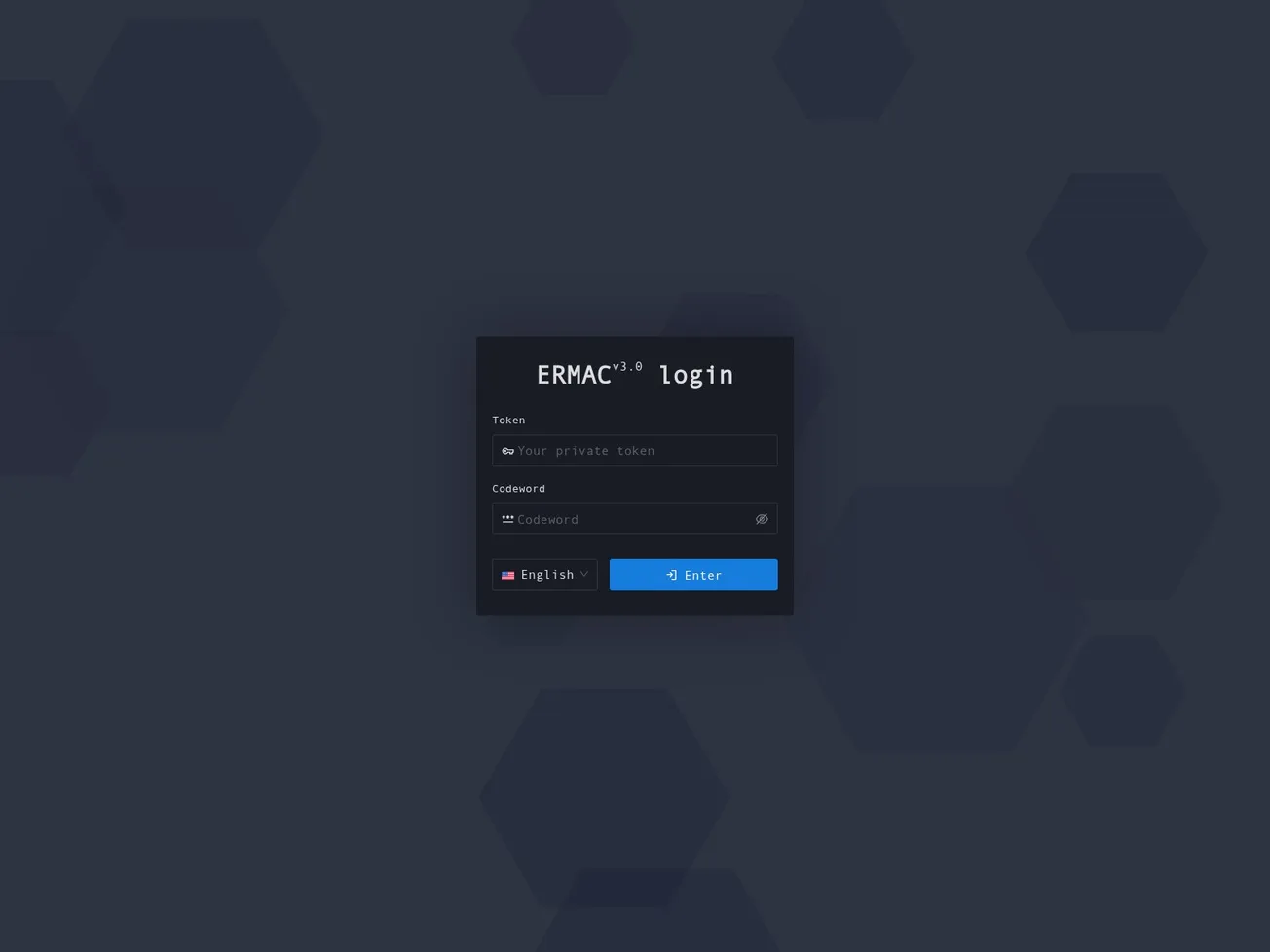
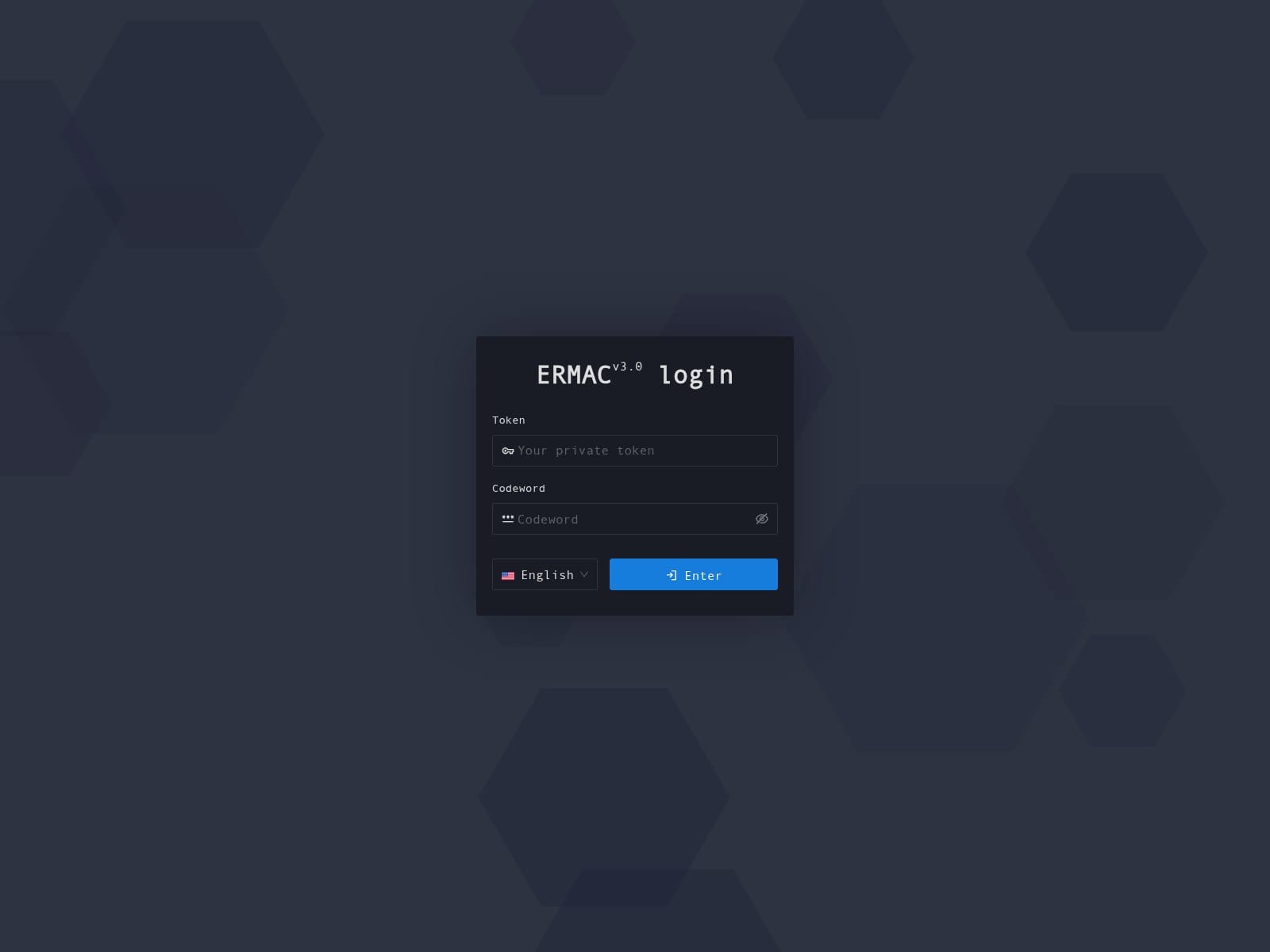
🔎 URLScan Result
- Page Title: ERMAC 3.0 PANEL
- Screenshot: View Screenshot
- Result: View URLScan Report
📡 Related Intelligence
- WHOIS Record: WHOIS Lookup
- VirusTotal Report: VirusTotal Domain Report
- Censys Reference: Censys Search
🛡️ Defensive Guidance
- Block
www.libertydroid-magma[.]topat DNS, proxy, and endpoint levels. - Monitor for outbound traffic to Hetzner-hosted infrastructure (AS24940).
- Hunt for apk.hook artifacts on mobile endpoints (APK sideload traces, suspicious accessibility service abuse).
- Review mobile MDM and firewall logs for attempts to connect to ERMAC 3.0 C2 panels.