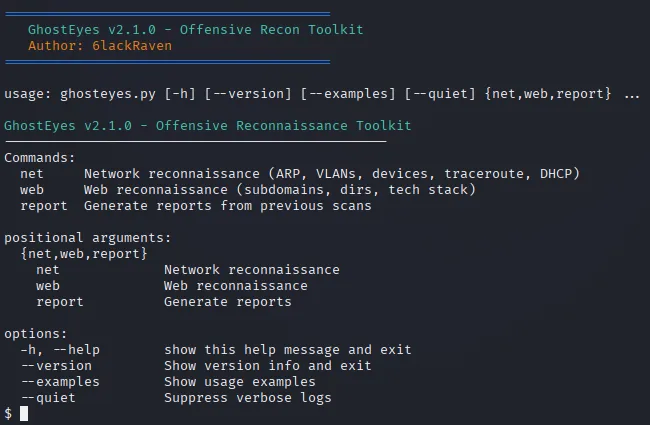
GitHub: https://github.com/6lackRaven/GhostEyes
GhostEyes is an asynchronous-first, modular offensive reconnaissance toolkit built for penetration testers, red team operators, and security researchers. It combines network and web recon capabilities with streamlined report generation — all within a modern, clean codebase.
What’s New in v2.1.0
- Fixed
asyncio.run()nesting issues (no more runtime conflicts) - Colorized CLI output, quiet mode, and customizable output paths
--examplesflag for quick onboarding- Clean structure, ready for future v3 enhancements (plugin system, structured logs, etc.)
Key Features
Network Reconnaissance
- ARP subnet scanning
- VLAN discovery and sampling
- Layer 2 traceroute
- DHCP traffic monitoring
- Real-time device tracking
Web Reconnaissance
- Subdomain brute-force
- Directory brute-force
- Technology stack detection
Reporting
- Generate reports in TXT, JSON, HTML, and CSV formats
- Supports multiple output types from previous scans
CLI User Experience
- Support for
--version,--examples,--quiet,--output - Colorized terminal output
- Single
asyncio.run()ensures compatibility with async workflows
Installation
bashCopyEditgit clone https://github.com/6lackRaven/GhostEyes.gitcd GhostEyes
pip install -r requirements.txt
Python 3.10 or higher is recommended.
Quick Start
bashCopyEdit# Show help
python ghosteyes.py -h# Show version
python ghosteyes.py --version# View example usage
python ghosteyes.py --examples
Command Overview
net — Network Reconnaissance
bashCopyEditpython ghosteyes.py net -i [--scan CIDR | --vlan | --track | --trace IP | --dhcp] [--duration N] [--output FILE]
| Option | Description |
|---|---|
-i, --interface | Specify network interface (default: eth0) |
-s, --scan | ARP scan a subnet (e.g., 192.168.1.0/24) |
-v, --vlan | Discover VLANs |
-t, --track | Track live devices |
-r, --trace | Layer 2 traceroute to a target IP |
-d, --dhcp | Capture DHCP traffic |
--duration | Duration (seconds) for vlan, track, or dhcp |
--output | Output file path (default: scan_net.json) |
Examples:
bashCopyEdit# ARP scan
python ghosteyes.py net -i eth0 --scan 192.168.1.0/24 --output my_scan.json# VLAN discovery
python ghosteyes.py net -i eth0 --vlan --duration 120# Device tracking
python ghosteyes.py net -i wlan0 --track --duration 60 --quiet
web — Web Reconnaissance
bashCopyEditpython ghosteyes.py web -u https://example.com [OPTIONS]
| Option | Description |
|---|---|
-u, --url | Target URL (required) |
-s, --subdomains | Subdomain brute-force wordlist |
-b, --bruteforce | Directory brute-force wordlist |
-T, --tech | Detect web technology stack |
-w, --workers | Number of concurrent workers (default: 50) |
--output | Output file (default: scan_web.json) |
Examples:
bashCopyEdit# Subdomain scan with tech detection
python ghosteyes.py web -u https://example.com -s subdomains.txt -T# Directory brute-force
python ghosteyes.py web -u https://example.com -b dirs.txt --quiet
report — Generate Recon Reports
bashCopyEditpython ghosteyes.py report -f scan_net.json -t html json
| Option | Description |
|---|---|
-f, --file | Input file path (must be a JSON scan result) |
-t, --type | Output format(s): txt, json, html, csv, all |
Examples:
bashCopyEdit# Generate HTML and JSON reports
python ghosteyes.py report -f scan_net.json -t html json# Generate all report formats
python ghosteyes.py report -f scan_web.json -t all
Output Files
| Scan Type | Default Output File |
|---|---|
| Network | scan_net.json |
| Web | scan_web.json |
Use --output to customize the filename and path.
Roadmap Toward v3
Planned enhancements include:
- Plugin-based architecture
- Structured logging (JSON with log levels)
- Config file support via
.tomlor.yaml - Improved concurrency with timeouts and cancellation
- Packaging via PyPI (
pip install ghosteyes) - Self-contained binaries and REST API/Web UI interface
Details available in CHANGELOG.md.
Legal Notice
GhostEyes is provided strictly for ethical security research and authorized testing. By using this tool, you agree to:
- Only scan targets you own or are explicitly authorized to test
- Comply with local and international laws (e.g., CFAA, GDPR)
- Accept full responsibility for any actions performed
The authors disclaim liability for misuse or damage caused by this tool.
License
Released under the MIT License.
Contact
- Author: 6lackRaven
- Email: harleystanislas.raven@gmail.com
- Telegram: @Thereal6lackRaven
- Facebook: Harley Stanislas
Contributing
Interested in contributing?
- Fork the repository
- Create a feature branch:
git checkout -b feature/my-feature - Write clean, tested code
- Submit a pull request with a clear description
Follow the existing code style and maintain respectful collaboration.