Unlock Exclusive Cyber Threat Intelligence
Powered by DarkWebInformer.com
Foundational access to breach intelligence. Track breaches, leaks, and threats in real time with high quality screenshots and concise expert summaries.
Continuously updated breach reports and threat summaries.
Daily breach, leak, and DDoS alerts.
Live tracking with JSON export.
Direct access to claims and posts.
Concise summaries of DDoS, defacements, and breaches.
Verified index of dark web sites and services.
Live status of 500+ sites.
Integrated checks inside breach posts.
Uncompressed, watermark free evidence.
Browser alerts for tracked terms.
API Access for Researchers & Security Teams
SOC teams, researchers, and security professionals can integrate Dark Web Informer's threat intelligence directly into their workflows via API. Access real-time breach data, threat feeds, and monitoring capabilities programmatically.
Learn About API AccessDisclaimer
This breach alert includes material that may contain personally identifiable information (PII) gathered strictly from publicly available sources. All information is provided solely for cybersecurity awareness and threat intelligence purposes.
French Management School CRM Database Offered for Sale Following VPS Compromise
Quick Facts
Incident Overview
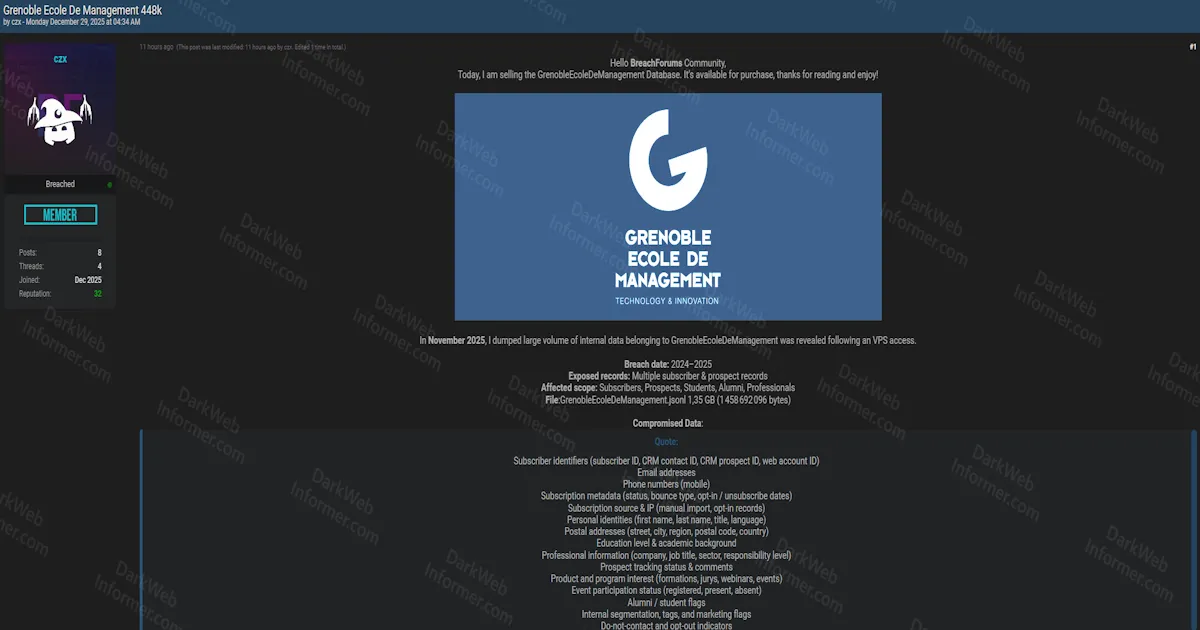
A threat actor going by "czx" has posted a database for sale that allegedly contains 448,000 records from Grenoble Ecole de Management, one of France's prominent business schools. The December 29, 2025 listing on BreachForums claims the breach happened back in November 2025 after the attacker gained access through a compromised VPS server.
The leaked database appears to be a comprehensive CRM export spanning data from 2024 through 2026, weighing in at 1.35GB with over 1.4 million rows of data. What's particularly notable here is the breadth of information exposed—this isn't just basic contact details. The database reportedly includes everything from subscription tracking and marketing segmentation to detailed academic backgrounds and professional profiles of both current subscribers and prospective students.
The threat actor has made the data available through PixelDrain with a sample dataset posted on Rentry, and they've included database selectors showing exactly what fields are contained in the leak. For a business school that depends on recruiting students globally and maintaining relationships with professionals, this kind of exposure could enable highly targeted phishing campaigns and social engineering attacks against their community.