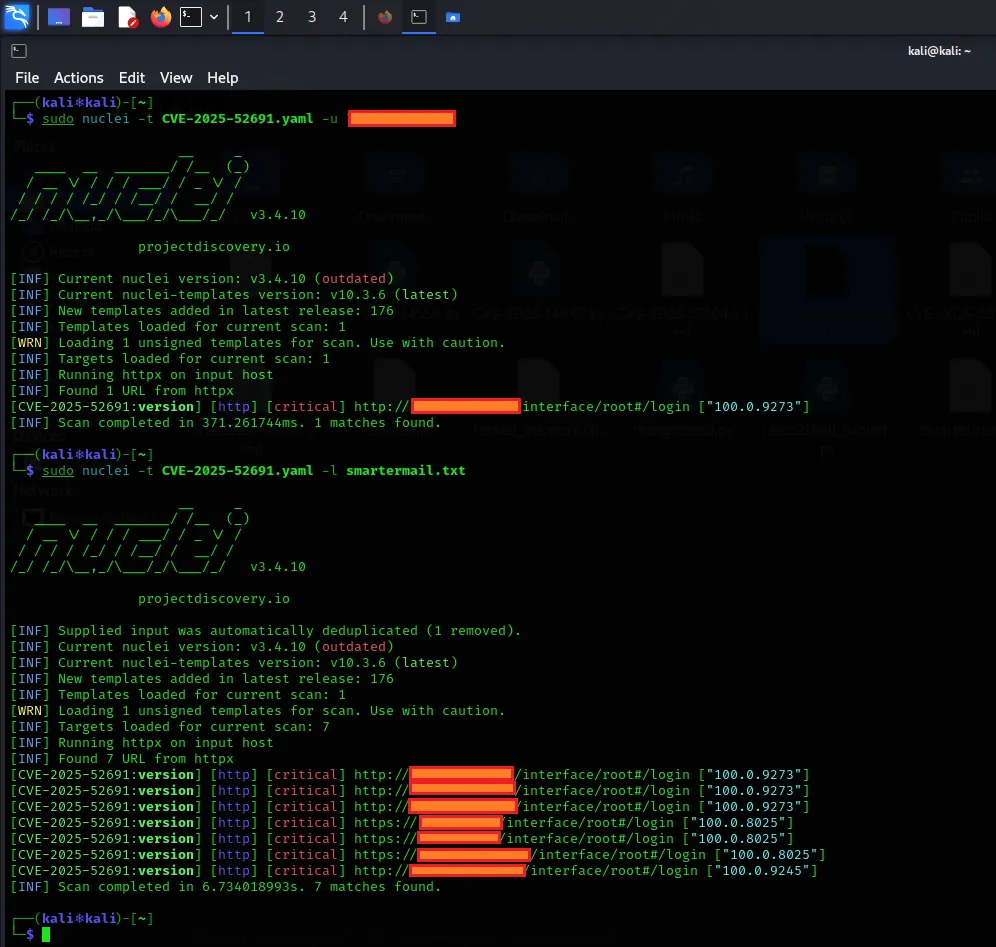
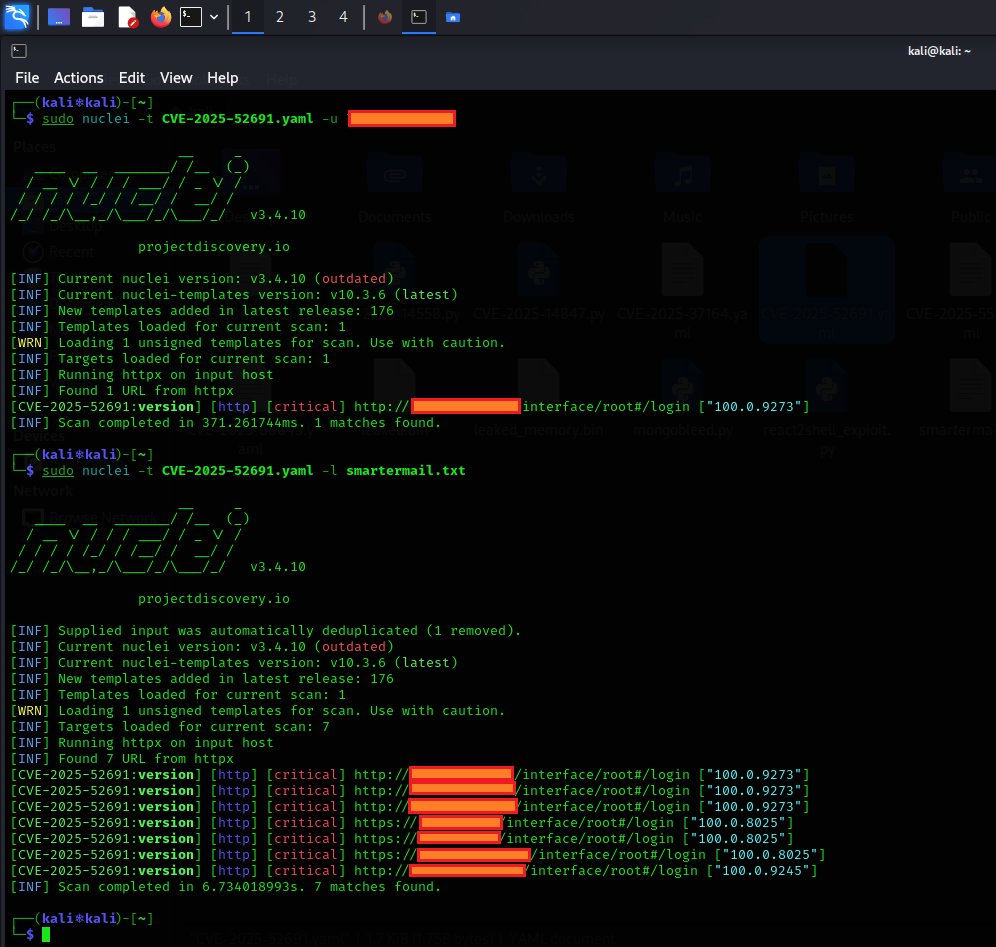
Repository: https://github.com/ninjazan420/CVE-2025-52691-PoC-SmarterMail-authentication-bypass-exploit-WT-2026-0001
A proof-of-concept exploit has been publicly released on GitHub targeting two critical vulnerabilities in SmarterTools SmarterMail. The PoC, published by user "ninjazan420," combines CVE-2025-52691 with the authentication bypass tracked as WT-2026-0001 to achieve pre-authentication remote code execution with SYSTEM privileges.
Vulnerability Overview
The exploit chains two distinct vulnerabilities affecting SmarterMail installations:
CVE-2025-52691 — Pre-Auth Remote Code Execution via File Upload
- CVSS Score: 10.0 (Critical)
- Affected Versions: Build 9406 and earlier; Build 16.3.6989.16341 and earlier
- Fixed Version: Build 9413 and later
This vulnerability was originally researched by watchTowr Labs, who published technical details in their advisory.
WT-2026-0001 — Authentication Bypass via Password Reset
- CVE Status: No CVE-ID assigned
- Affected Versions: Up to Build 9510
- Fixed Version: Build 9511 (January 15, 2026)
This authentication bypass was also discovered and documented by watchTowr Labs in their research article titled "Attackers With Decompilers Strike Again."
Attack Chain
The PoC executes a three-phase attack:
Phase 1 — Authentication Bypass: The exploit leverages WT-2026-0001 to change the administrator password without requiring verification of the original password. This is accomplished via a POST request to /api/v1/auth/force-reset-password with the IsSysAdmin parameter set to true.
Phase 2 — Admin Login: Using the newly set credentials, the exploit authenticates to the SmarterMail web interface through /api/v1/auth/login.
Phase 3 — RCE via Volume Mounts: With administrative access, the exploit creates a malicious Volume Mount through /api/v1/settings/volume-mounts configured to execute a reverse shell command. This results in command execution with SYSTEM privileges on the target server.
Technical Details
The authentication bypass payload targets the password reset endpoint without proper authorization checks:
POST /api/v1/auth/force-reset-password
{
"IsSysAdmin": "true",
"OldPassword": "dummy",
"Username": "admin",
"NewPassword": "[attacker-controlled]",
"ConfirmPassword": "[attacker-controlled]"
}A successful bypass returns a response with "success": true and a resultCode of 200, along with debug information indicating the bypass path taken through the vulnerable code.
PoC Repository Contents
The GitHub repository includes:
exploit.py— Python attack script implementing the full exploit chainrun_exploit.sh— Automated setup and execution wrappersetup_venv.sh— Virtual environment setup scriptactivate_exploit.sh/deactivate_exploit.sh— Environment management scriptsrequirements.txt— Python dependenciesconfig/— Configuration directory
Affected Systems
Organizations running SmarterMail on the following builds are potentially vulnerable:
- CVE-2025-52691: Builds 9406 and earlier, or Build 16.3.6989.16341 and earlier
- WT-2026-0001: Builds up to 9510
Both vulnerabilities must be present for the full attack chain. Systems updated to Build 9511 or later (released January 15, 2026) are patched against the authentication bypass.
Remediation
Administrators running SmarterMail should immediately update to Build 9511 or later to address both vulnerabilities. Organizations unable to patch immediately should consider restricting access to the SmarterMail web interface and monitoring for suspicious authentication activity and Volume Mount creation.
References
- PoC Repository: https://github.com/ninjazan420/CVE-2025-52691-PoC-SmarterMail-authentication-bypass-exploit-WT-2026-0001
- watchTowr Labs CVE-2025-52691 Research: https://github.com/watchtowrlabs/watchTowr-vs-SmarterMail-CVE-2025-52691
- watchTowr Labs WT-2026-0001 Article: https://labs.watchtowr.com/attackers-with-decompilers-strike-again-smartertools-smartermail-wt-2026-0001-auth-bypass/