Link: https://github.com/lfillaz/CVE-2024-2997
Features
- Generates a wide range of URLs based on a base URL.
- Scans URLs for a specific command injection vulnerability.
- Uses multithreading for faster scanning.
- Displays results in a color-coded format.
- Saves vulnerable URLs to a file for future reference.
- Allows resuming scans from a previous session.
Requirements
- Python 3.x
requestscolorama
You can install the required libraries using pip:
pip install requests coloramaUsage
- Clone the repository:
git clone https://github.com/yourusername/CVE-2024-2997.git
cd CVE-2024-2997
- Run the script:
python CVE-2024-2997.py
- Follow the on-screen instructions to input the base URL and start the scan.
How It Works
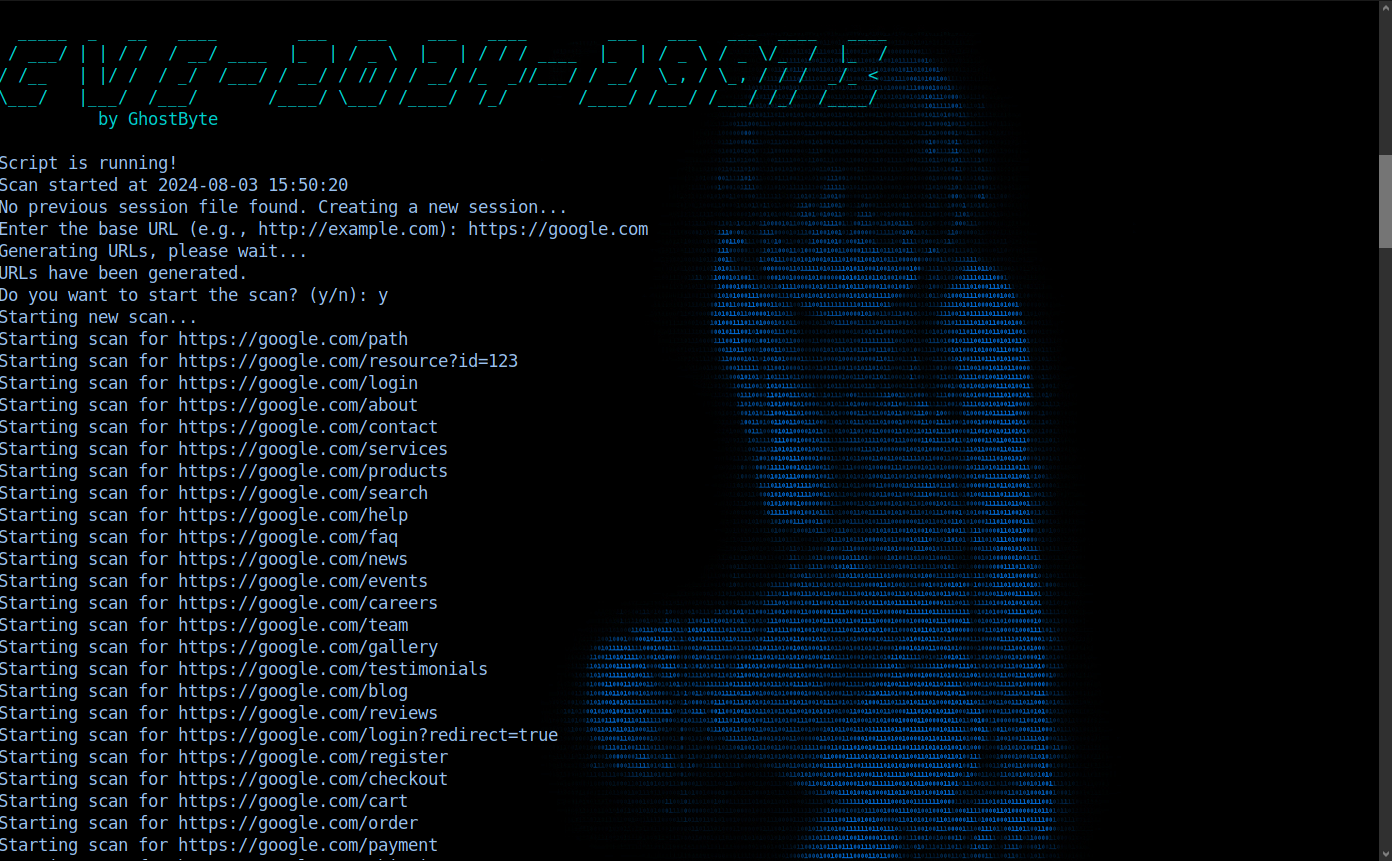
- The script prints an ASCII art banner and starts the scanning process.
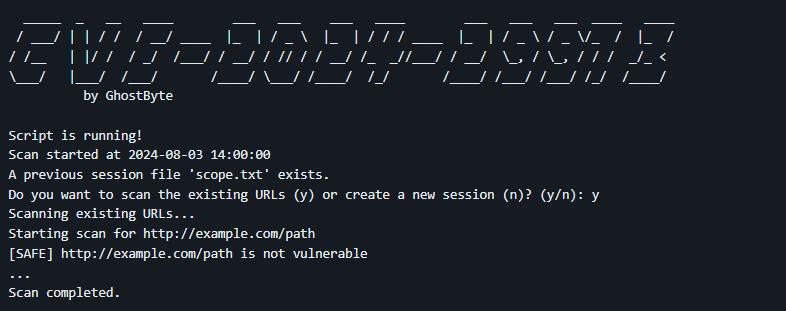
- It checks if a previous session file
scope.txtexists:- If it exists, the user can choose to continue scanning the URLs from the previous session or start a new session.
- If it doesn't exist, a new session is started.
- The user inputs the base URL.
- The script generates a wide range of URLs based on the base URL.
- The user is prompted to start the scan.
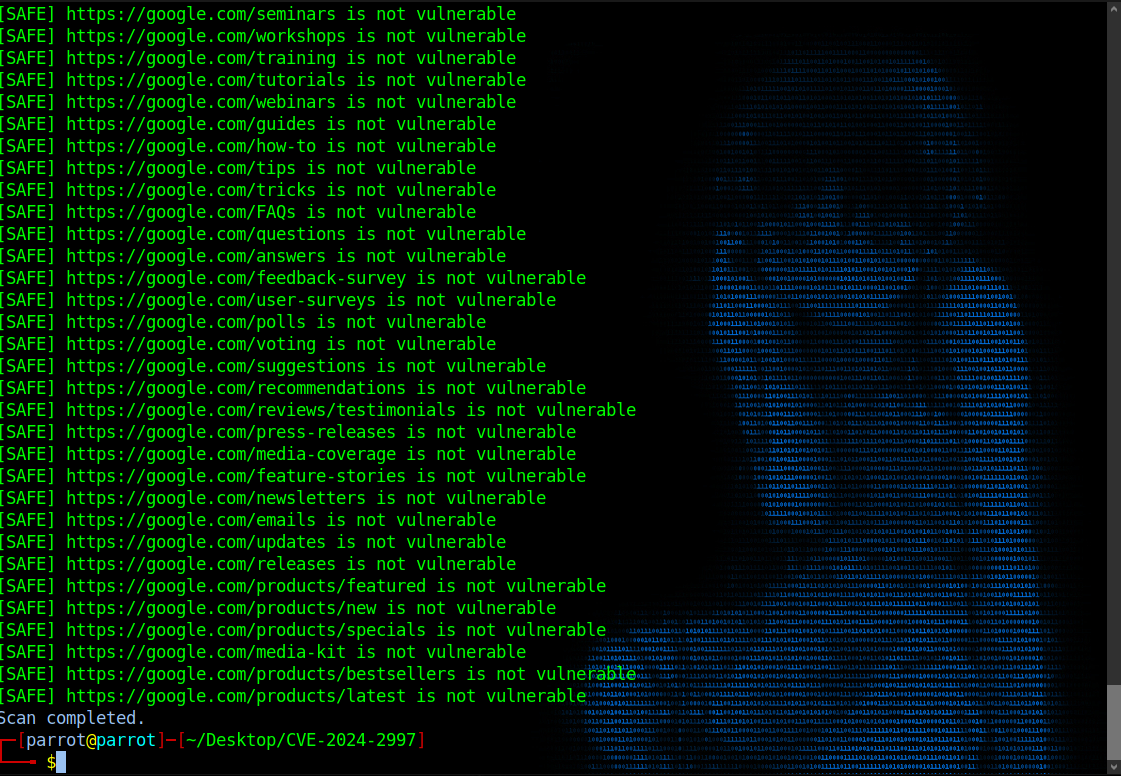
- The script scans each URL for the command injection vulnerability, displaying the results in a color-coded format:
- Vulnerable URLs are displayed in red.
- Safe URLs are displayed in green.
- Results are saved to
sus.txt.